Imagine cruising down the highway, only to receive an alarming text about unpaid tolls. Your heart races as you read, “Vehicle Has Been Recorded Using the FasTrak Express Lane.” But before you rush to settle this unexpected debt, pause. You might be staring at the bait of an increasingly common and dangerously convincing scam.
This isn’t just another run-of-the-mill phishing attempt. It’s a sophisticated scheme that’s fooling even the most cautious drivers. By exploiting our trust in official communications and our fear of financial penalties, scammers are reeling in unsuspecting victims at an alarming rate.
In this article, we’ll dive deep into the inner workings of this deceptive operation. You’ll discover how these digital highwaymen operate, the telltale signs of their fraudulent messages, and most importantly, how to shield yourself from becoming their next target. Buckle up – this journey through the treacherous landscape of the FasTrak text scam might just save your identity and your hard-earned money. Let’s hit the road and unmask these highway robbers!
Scam Overview
The “Vehicle Has Been Recorded Using the FasTrak Express Lane” text message scam is a sophisticated phishing attempt that preys on unsuspecting drivers. This deceptive scheme masquerades as an official communication from FasTrak, a legitimate electronic toll collection system used in various parts of California. The scam’s primary goal is to trick recipients into divulging personal and financial information under the guise of settling an overdue toll fee.
At its core, this scam exploits the fear of accumulating late fees and the desire to resolve potential legal issues quickly. The fraudsters behind this scheme craft messages that appear both urgent and official, creating a sense of immediacy that can cloud judgment and lead victims to act hastily.
The scam typically unfolds as follows: Victims receive a text message claiming their vehicle has been recorded using a FasTrak Express Lane. The message warns of impending late fees and directs the recipient to a website where they can supposedly settle their balance. However, this website is a carefully crafted forgery designed to capture sensitive information.
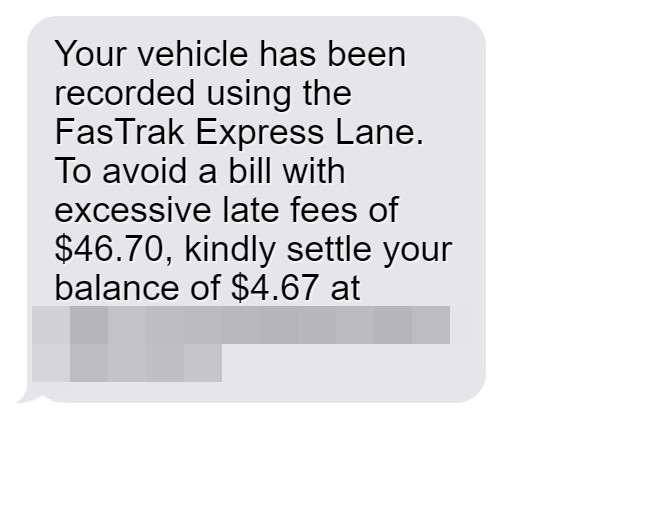
What makes this scam particularly insidious is its attention to detail. The text messages often include specific monetary amounts, both for the supposed toll and the threatened late fee. For example, a typical message might read: “Your vehicle has been recorded using the FasTrak Express Lane. To avoid a bill with excessive late fees of $46.70, kindly settle your balance of $4.67 at https://bayareafastrakservices.com.”
The use of precise figures lends an air of legitimacy to the message, making it more likely that recipients will take it seriously. Additionally, the stark contrast between the small initial fee and the much larger late fee creates a sense of urgency, prompting victims to act quickly to avoid the larger charge.
The scam website itself is often a masterclass in deception. It mimics the look and feel of official FasTrak websites, complete with logos, color schemes, and professional-looking layouts. This attention to detail can make it difficult for even savvy internet users to distinguish between the fraudulent site and a legitimate one.
One of the key elements that sets this scam apart is its use of personal information. The fraudsters may have obtained some basic details about their targets – such as names or general locations – through data breaches or other means. By incorporating this information into their messages and websites, they create a veneer of authenticity that can be very convincing.
The scammers behind this operation demonstrate a sophisticated understanding of human psychology. They exploit common fears and concerns, such as the worry about legal trouble or financial penalties. By presenting their scheme as a simple solution to avoid these problems, they manipulate victims into taking actions they might otherwise question.
It’s important to note that this scam is not limited to a single geographic area. While it often targets regions where FasTrak is commonly used, such as the San Francisco Bay Area, similar scams have been reported in other parts of the country. The fraudsters may adapt their approach to mimic local toll collection systems, making the scam relevant to a wider audience.
The impact of this scam extends beyond immediate financial loss. Victims who provide their personal and financial information may find themselves vulnerable to identity theft, unauthorized charges, and a host of other fraudulent activities. The psychological toll can also be significant, leaving victims feeling violated and wary of legitimate communications in the future.
As this scam continues to evolve, it’s crucial for drivers and the general public to stay informed and vigilant. The next section will delve into the specific mechanics of how this scam operates, providing a step-by-step breakdown of the tactics employed by these cybercriminals.
How The Scam Works
Understanding the intricate mechanics of the “Vehicle Has Been Recorded Using the FasTrak Express Lane” text message scam is crucial for protecting yourself and others from falling victim to this deceptive scheme. Let’s break down the process step-by-step to reveal how these scammers operate and why their tactics are so effective.
Step 1: Initial Contact via Text Message
The scam begins with a carefully crafted text message sent to potential victims. This message is designed to appear as an official communication from FasTrak or a similar toll collection service. The text typically includes the following elements:
- A statement that the recipient’s vehicle has been recorded using an express lane
- A specific, small amount claimed as the toll fee (e.g., $4.67)
- A much larger amount presented as a potential late fee (e.g., $46.70)
- A sense of urgency to pay the smaller amount to avoid the larger fee
- A link to a website where the payment can supposedly be made
For example, the message might read: “Your vehicle has been recorded using the FasTrak Express Lane. To avoid a bill with excessive late fees of $46.70, kindly settle your balance of $4.67 at https://bayareafastrakservices.com.”
The use of specific dollar amounts and the threat of a much larger late fee are psychological tactics designed to create a sense of legitimacy and urgency. The small initial fee seems reasonable and easy to pay, while the larger late fee motivates quick action to avoid a more significant financial burden.
Step 2: The Fraudulent Website
If the recipient clicks on the link provided in the text message, they are directed to a website that closely mimics the appearance of an official FasTrak or toll collection service site. This fraudulent website is a key component of the scam, designed to fool victims into believing they are interacting with a legitimate service. The website typically includes:
- Official-looking logos and branding elements
- A professional layout and design that matches the style of legitimate toll collection websites
- Carefully worded text that maintains the illusion of an official service
- Forms requesting personal and financial information
The scammers pay close attention to detail in creating these websites, often copying elements directly from legitimate sites to enhance their credibility.
Step 3: Information Gathering
Once on the fraudulent website, victims are prompted to enter various pieces of personal information, ostensibly to verify their identity and locate their toll record. This information may include:
- Full name
- Phone number
- Address
- Date of birth
- Driver’s license number
The website may present this as a necessary step to “validate your search” or “locate your account.” In reality, this is the first stage of data collection for the scammers.
Step 4: Presenting the “Toll Fee”
After the victim enters their personal information, the website displays a page showing the supposed toll fee owed. This page typically includes:
- A transaction number (e.g., nV001Mmi9H)
- The amount owed (matching the amount in the initial text message)
- A reminder of the potential late fee
- A deadline for payment to avoid the late fee
This presentation serves to reinforce the urgency of the situation and push the victim towards making a payment.
Step 5: Payment Information Collection
The final and most critical step for the scammers is collecting payment information. The website will present a form for entering credit card details, including:
- Credit card number
- Expiration date
- CVV (Card Verification Value) number
This is where the scam reaches its most dangerous point. By entering this information, victims are not only potentially authorizing a fraudulent charge but also handing over sensitive financial data that can be used for further fraudulent activities.
Step 6: Data Exploitation
Once the scammers have collected both personal and financial information, they have several options for exploiting this data:
- Immediate unauthorized charges to the provided credit card
- Selling the collected information on the dark web to other criminals
- Using the personal information for identity theft purposes
- Employing the gathered data to make the victim more susceptible to future scams
Step 7: Covering Tracks
To delay detection and prevent immediate action by the victim, the scammers may:
- Provide a fake confirmation number for the “payment”
- Send a follow-up text or email thanking the victim for their payment
- Redirect the victim to a legitimate FasTrak website after the transaction, further confusing the issue
Step 8: Repeat and Evolve
The scammers don’t stop with a single victim. They continually:
- Send out new waves of text messages to fresh targets
- Adapt their tactics based on success rates and victim responses
- Update their fraudulent websites to stay ahead of detection efforts
- Modify their approach to mimic different toll collection systems in various regions
Understanding this step-by-step process reveals the intricate nature of the scam and the multiple layers of deception involved. The scammers rely on a combination of social engineering, technical sophistication, and psychological manipulation to achieve their goals.
What makes this scam particularly effective is its exploitation of common human behaviors and emotions:
- Trust in official-looking communications
- Fear of legal or financial consequences
- Desire to resolve issues quickly and easily
- Tendency to act hastily when faced with a perceived threat
By leveraging these psychological factors, the scammers create a scenario where even typically cautious individuals might let their guard down and fall victim to the scheme.
It’s crucial to note that the scammers are constantly evolving their tactics. They may incorporate new elements such as:
- Using AI-generated voice messages to add another layer of perceived legitimacy
- Implementing more sophisticated phishing websites that can bypass some security measures
- Tailoring their approach based on data harvested from social media profiles
The ongoing evolution of this scam underscores the importance of staying informed and maintaining a healthy skepticism towards unsolicited communications, especially those requesting personal or financial information.
What to Do if You Have Fallen Victim to This Scam
If you suspect that you’ve fallen victim to the “Vehicle Has Been Recorded Using the FasTrak Express Lane” text message scam, it’s crucial to act quickly to minimize potential damage and protect yourself from further harm. Here’s a step-by-step guide on what to do:
1. Don’t Panic, But Act Swiftly
While it’s natural to feel alarmed, try to remain calm. Clear thinking will help you take the necessary steps more effectively. Remember, acting quickly can significantly mitigate the potential damage.
2. Contact Your Financial Institutions
If you provided credit card information:
- Immediately contact your credit card company.
- Report the fraudulent activity and request to have the card canceled and replaced.
- Dispute any unauthorized charges.
If you provided bank account information:
- Contact your bank immediately.
- Consider closing the compromised account and opening a new one.
- Monitor your account closely for any unauthorized transactions.
3. Place a Fraud Alert on Your Credit Reports
- Contact one of the three major credit bureaus (Equifax, Experian, or TransUnion) to place a fraud alert on your credit report.
- This alert notifies potential creditors to verify your identity before granting credit in your name.
- The bureau you contact is required to notify the other two.
4. File a Report with the Federal Trade Commission (FTC)
- Visit the FTC’s website (ftc.gov) or call 1-877-FTC-HELP to file a complaint.
- This helps law enforcement track and combat such scams.
5. File a Police Report
- Contact your local police department to file a report.
- This creates an official record of the incident, which can be useful when dealing with creditors or other institutions.
6. Change Your Passwords
- If you used any passwords on the scam website, change them immediately on all accounts where you’ve used the same or similar passwords.
- Use strong, unique passwords for each account.
7. Monitor Your Accounts and Credit Reports
- Regularly check your bank and credit card statements for any suspicious activity.
- Consider setting up alerts for transactions on your accounts.
- Review your credit reports frequently in the months following the incident.
8. Be Vigilant for Follow-Up Scams
- Be aware that falling victim to one scam might make you a target for others.
- Be especially cautious of any unsolicited communications claiming to help you recover from the scam.
9. Educate Yourself and Others
- Learn more about phishing scams and how to identify them.
- Share your experience with friends and family to help them avoid similar scams.
10. Seek Support if Needed
- If you’re feeling overwhelmed or stressed, don’t hesitate to seek support from friends, family, or a professional counselor.
- Falling victim to a scam can be emotionally taxing, and it’s okay to ask for help.
11. Contact the Real FasTrak or Toll Authority
- Reach out to the legitimate toll authority in your area to verify if you actually owe any tolls.
- Report the scam to them so they can warn other customers.
12. Consider Identity Theft Protection Services
- While not always necessary, you might want to consider subscribing to an identity theft protection service for additional monitoring and support.
Remember, taking these steps doesn’t guarantee that you won’t face any consequences from the scam, but it significantly reduces the risk of further damage and helps protect your identity and finances in the long run. Stay vigilant and don’t hesitate to seek professional help if you’re unsure about any aspect of dealing with the aftermath of the scam.
Frequently Asked Questions: “Vehicle Has Been Recorded Using the FasTrak Express Lane” Text Message Scam
1. How can I recognize the FasTrak Express Lane text message scam?
The FasTrak Express Lane text message scam can be identified by several key characteristics:
- Unsolicited text messages claiming you owe toll fees
- Urgent language pressuring you to pay immediately
- Threats of excessive late fees
- Links to websites that aren’t official FasTrak domains
- Requests for personal and financial information
Always verify any unexpected toll notifications through official channels before taking action.
2. What information do scammers typically ask for in this scam?
Scammers often request a range of personal and financial information, including:
- Full name
- Address
- Phone number
- Date of birth
- Driver’s license number
- Credit card details (number, expiration date, CVV)
- Bank account information
Never provide this information in response to unsolicited messages or on unverified websites.
3. Can scammers access my FasTrak account through this scam?
Scammers cannot directly access your legitimate FasTrak account through this scam. However, if you provide your FasTrak account credentials on a fraudulent website, scammers could potentially use that information to log into your real account. Always ensure you’re on the official FasTrak website before entering any login information.
4. What should I do if I’ve already responded to the scam text message?
If you’ve responded to the scam text message:
- Immediately contact your bank or credit card company to report potential fraud
- Change passwords for any accounts where you may have used the compromised information
- Place a fraud alert on your credit reports
- Monitor your accounts closely for any unauthorized activity
- Report the scam to the Federal Trade Commission (FTC) and local law enforcement
5. Are there any legitimate scenarios where FasTrak would contact me via text message?
While FasTrak may use text messages for some communications, they typically don’t initiate contact about unpaid tolls or fees via text. Legitimate FasTrak communications would direct you to their official website (www.bayareafastrak.org for the Bay Area) and wouldn’t pressure you to make immediate payments. When in doubt, contact FasTrak directly using the information on their official website.
6. How can I verify if I actually owe any tolls to FasTrak?
To verify any toll charges:
- Visit the official FasTrak website for your region (e.g., www.bayareafastrak.org for the Bay Area)
- Log into your account or use the “Pay a Toll” feature for non-account holders
- Check for any outstanding tolls or violations
- If you’re unsure, call the official FasTrak customer service number listed on their website
Never rely solely on information provided in unsolicited text messages or emails.
7. What are the potential consequences of falling for this scam?
Falling for this scam can have several serious consequences:
- Financial loss from unauthorized charges
- Identity theft using your personal information
- Compromised credit score if scammers open accounts in your name
- Increased vulnerability to future scams
- Emotional stress and anxiety
It’s crucial to act quickly if you suspect you’ve been scammed to minimize these potential impacts.
8. How can I report this scam to the authorities?
To report the FasTrak Express Lane text message scam:
- File a complaint with the Federal Trade Commission at ftc.gov/complaint
- Report it to your local law enforcement agency
- Inform your state’s Attorney General’s office
- Report the scam to the legitimate FasTrak authority in your area
- If you received the scam via text, forward the message to 7726 (SPAM) to report it to your wireless carrier
Reporting helps authorities track and combat these scams more effectively.
9. Can my phone be hacked just by receiving the scam text message?
Simply receiving a scam text message typically won’t hack your phone. However, clicking on links within the message could potentially lead to malware installation or phishing websites. To stay safe:
- Don’t click on links in suspicious text messages
- Keep your phone’s operating system and security software updated
- Be cautious about granting permissions to unknown apps or websites
If you’re concerned, consider having your device checked by a professional.
10. How do scammers obtain my phone number for these text message scams?
Scammers can obtain phone numbers through various means:
- Data breaches from companies or organizations
- Purchasing lists from unethical data brokers
- Random number generation (especially for area codes with high populations)
- Public records or online directories
- Social media profiles with visible contact information
Protect your number by being cautious about where you share it and adjusting privacy settings on social media platforms.
The Bottom Line
The “Vehicle Has Been Recorded Using the FasTrak Express Lane” text message scam serves as a stark reminder of the ever-present dangers lurking in our digital world. This sophisticated phishing scheme exploits our trust in official communications and our fear of financial penalties to trick unsuspecting victims into divulging sensitive personal and financial information.
Key takeaways from our investigation include:
- Scammers are using increasingly sophisticated tactics, including realistic-looking websites and urgent, official-sounding messages.
- The scam preys on common human behaviors and emotions, making even cautious individuals vulnerable.
- Immediate action is crucial if you suspect you’ve fallen victim to this or any similar scam.
- Prevention is the best defense – always verify the legitimacy of unsolicited communications before providing any personal or financial information.
- Staying informed about current scam tactics and maintaining a healthy skepticism can go a long way in protecting yourself.
By understanding how these scams operate and knowing how to respond if targeted, we can collectively work towards creating a safer digital environment for everyone. Stay alert, stay informed, and don’t hesitate to reach out for help if you find yourself in a suspicious situation. Your awareness and caution are your best defenses against the ever-evolving world of digital scams.



