Scammers are creating fake Meta Business Help Center websites mimicking Facebook’s official support hubs. Victims get redirected to these fraudulent sites through Facebook messages about trademark, copyright, or community standards violations.
- Overview of The Meta Business Help Center Scam Targeting Facebook
- How the Meta Business Help Center Scam Operates
- What To Do If You Land on a Fake Meta Business Help Website
- Frequently Asked Questions About the Fake Meta Business Help Sites Scam
- Conclusion: Verify Support Sites to Avoid Meta Business Scam Risks
The scam webpages feature “account recovery” forms capturing user credentials or personal details. Scammers use this data to hijack accounts and pages for spreading more scams, damaging reputations and reaching wider audiences.
This article exposes the Meta Business scam designed to resemble Facebook support resources. Learn how to avoid customized phishing traps aimed at theft from your social media presence and contacts.
Overview of The Meta Business Help Center Scam Targeting Facebook
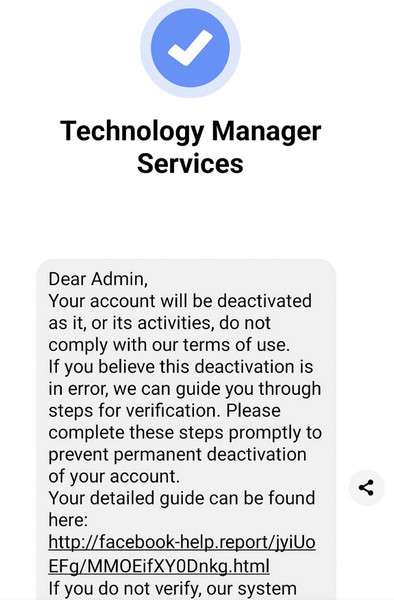
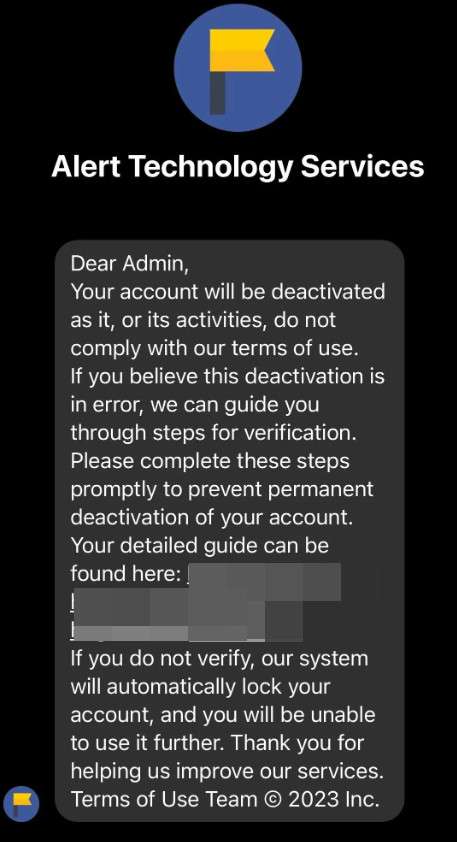
The Meta Business Help Center scam involves redirecting Facebook users to mimicked support websites using vivid copyright and policy violation warnings. Once on the realistic but fraudulent help sites, victims get prompted to enter account credentials or sensitive personal information.
Scammers gain access to accounts submitted on their phishing sites designed to recreate Facebook’s aesthetic. Account access enables posting more scam links while impersonating page owners without raising suspicions.
Stolen Facebook pages with established audiences also allow scammers to advertise fraudulent services or deals. At scale, these cons net huge profits from misled followers and site visitors.
This scam undermines user trust while hijacking valuable social media assets and data. Learn the signs of fake help pages masquerading as Facebook support to keep accounts secure.
Tactics Used in Phishing Links to Fake Support Pages
The scam messages and redirects leverage the following deceptive tactics:
- Urgent Threats of Disablement – Warnings threaten imminent account or page deletion to prompt hasty actions.
- Short Time Windows – Notices provide 24-48 hours to resolve issues, adding pressure for quick responses.
- Fraudulent Links – Embedded URLs route to phishing sites instead of Facebook’s infrastructure.
- Interface Mimicking – Imitation help sites precisely recreate fonts, colors, logos and page content to seem authentic.
- Personal Data Requests – Phishing forms require revealing valuable account credentials, names, birth dates and contact info.
By preying on fears of losing access and imposing rushed timelines, scammers undermine critical evaluation of their fake help sites. Victims enter the precise data needed to perpetrate extensive identity fraud and social media account misuse.
Scammer Motives Behind Stealing Facebook Accounts
The potential profits from accessed accounts motivate phishing schemes seeking Facebook credentials:
- Spam Friends – Leverage connections lists to distribute more viral scam links.
- Post Fake Deals – Advertise non-existent or fraudulent products/services using a trusted identity.
- Charge Ads Fraudulently – Create ads linked to stolen payment methods from user accounts.
- Install Engagement Bots – Automate artificial content interactions from account profiles.
- Reputation Sabotage – Post inflammatory content to tarnish page owner reputations.
At scale across thousands of followers, these tactics earn substantial incomes from deception and theft enabled by compromised accounts. Victims face personal losses and reputation damage when targeted by customized social media phishing ploys. Carefully vet any warnings or support sites to protect account security.
Examples of Meta Business Help Center Scam Sites
The phishing links bring users to sites like:
- meta-business-center[.]com
- meta-bussinesshelp[.]com
- businesshelp-meta[.]com
These domains mimic the real Meta Business Help Center name to seem authentic. However, inspect URLs closely to spot subtle misspellings exposing frauds.
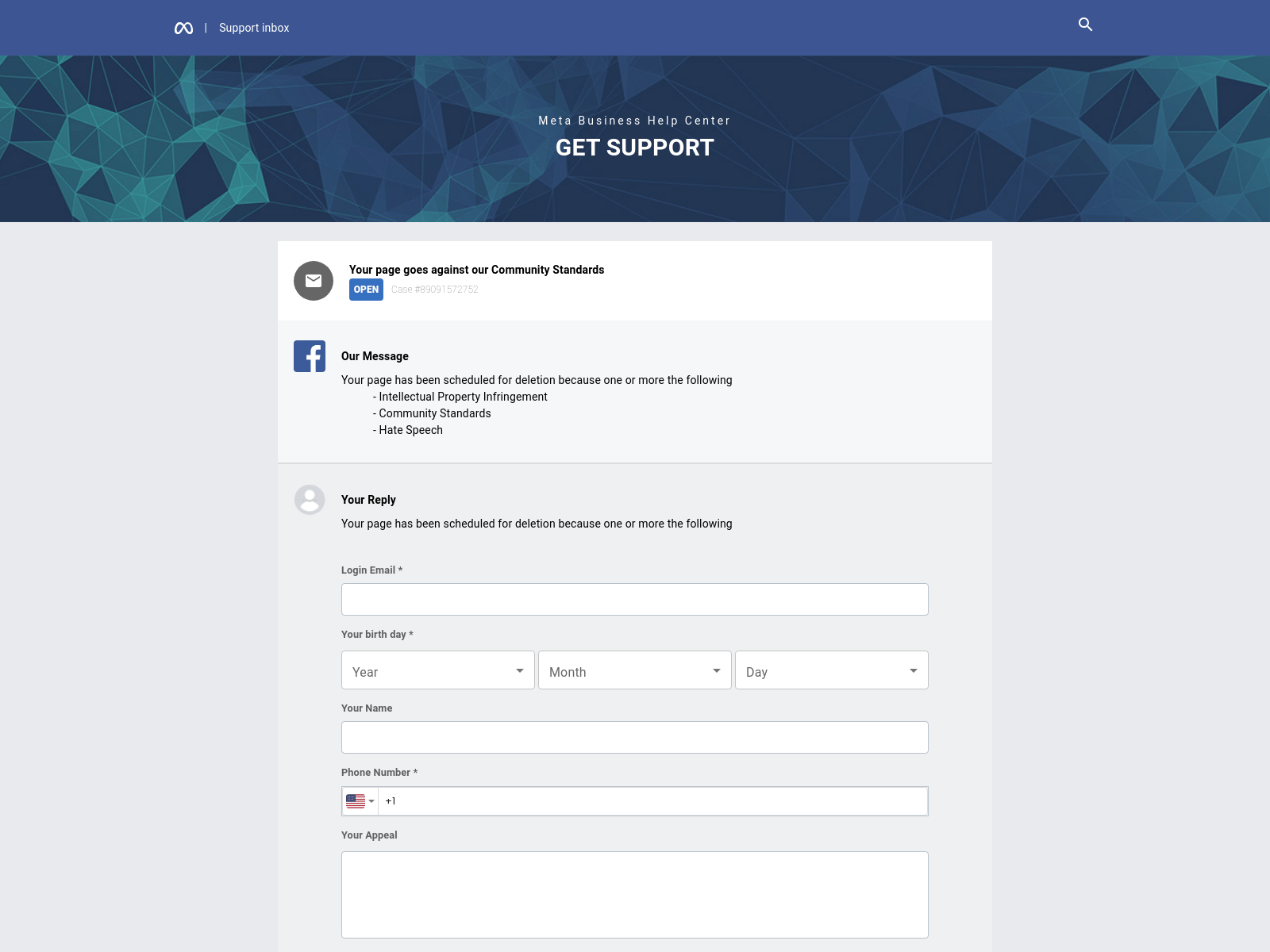
Below the URL, scam sites recreate the graphical elements of Facebook help pages. But inspection reveals missing security certificates, mismatched fonts and branding elements diverging from real support spaces.
Scam Site Content Matches Facebook’s Interface
The body content inside Meta Business scam sites mirrors Facebook’s warnings with:
- Case file ticket numbers
- Community standards violation accusations
- Field inputs capturing emails, birthdays, appeals messages, and phone numbers
This personal data gets submitted directly to scammers rather than resolving any policy issues. They use it to access accounts, steal identities and sell data.
Awareness of accurate Facebook support interfaces helps avoid entering details onto convincing fakes harvesting credentials.
How the Meta Business Help Center Scam Operates
The Meta Business Help Center scam employs precise social engineering strategies to perpetrate account and identity fraud:
Stage 1: Send Copyright Violation Warnings
Scammers distribute messages via Facebook Messenger to page owners claiming serious violations of platform policies. The most common accusations include:
- Trademark or copyright infringement
- Hate speech violations
- Harassment reports
- Impersonation complaints
These warnings threaten permanent deletion or disabling of pages if not addressed immediately through the provided help link.
Stage 2: Redirect to Fake Support Websites
The embedded links lead to imitation Meta Business Help Center websites requesting account details to resolve the alleged complaints. Interface elements closely resemble Facebook’s to avoid raising suspicions:
- Official branding like colors, logos and layout
- Case file ticket codes matching Facebook’s system
- Required personal details matching typical recovery forms
But site URLs contain subtle misspellings if inspected closely while missing valid HTTPS encryption. Still, many understandably believe they arrived safely on Facebook’s help sites.
Stage 3: Collect and Abuse Account Login Details
If users submit their account email address and password onto the scam phishing sites, scammers gain full access immediately. From there, they post more scam links via Messages and ads using saved payment methods.
They also collect sensitive personal information like names, birthdays and phone numbers to sell data or steal identities.
Losing administrative access to pages also prevents resolving any real policy violations. So the scams create lasting fallouts beyond temporary account access.
What To Do If You Land on a Fake Meta Business Help Website
If you followed a violation warning link leading to any website making you input Facebook login credentials, take these steps immediately:
Never Enter Your Login Email and Password Combo
Closing fake support sites without providing any account access information denies scammers control despite reaching their phishing pages.
Logging into a scam help site irreversibly hands your account to fraudsters. But not inputting anything keeps that control safely with you.
Run Security Checks on Your Account
In your real Facebook account’s Security and Login settings pages, check for any unfamiliar logged in devices or sessions.
Logout out of all active sessions which exit scammers from accounts they already accessed. Change your password to prevent further misuse.
Enable Login Alerts and Approvals
Configure added notifications so Facebook warns you of unrecognized device logins in the future.
Require special confirmation codes sent your phone anytime new browsers or apps attempt accessing the account. This adds verification steps foiling scammers.
Inform Contacts of Potential Scams
Assuming scammers could have messaged your contacts while in the account, warn connections of potential phishing attempts from your account.
Suggest reviewing messages and ignoring suspicious links to contain possible viral scam distribution through your messaging lists.
Frequently Asked Questions About the Fake Meta Business Help Sites Scam
As more Facebook users encounter redirects to convincing but fraudulent Meta Business help websites, several key questions require thorough answers. This FAQ provides complete details about spotting and responding to phishing links bringing you to mimic support pages.
What are red flags signaling a fake Meta Business help site?
Warning signs include:
- Misspelled URLs like “meta-bussinesshelp” instead of “business”
- Unsecured sites without “HTTPS” browser padlock icons
- Slightly distorted logos or fonts vs Facebook’s real pages
- Requests for sensitive personal information
- Poor grammar/spelling errors throughout the content
Seeing one or more inconsistencies suggests scammers created imitation interfaces, not real Facebook help centers. Exercise extreme cautions entering any data on these sites.
What should you do if you submit account details to a phishing help site?
If you inputted a Facebook login email and password onto a scam help website, take these counteractions immediately:
- Log into the real Facebook site and change your password
- Review account Security settings for any unfamiliar sessions to terminate
- Enable two-factor authentication requiring extra login verifications
- Check message history for unauthorized spam blasts
- Alert contacts of potential fake messages from your account
These steps can contain the damage from any credentials already gathered by phishing sites posing as Facebook support hubs.
How can you report fake Meta Business pages?
File detailed complaints about any phishing websites or warning message links via:
- Facebook’s reporting form on unauthorized account access attempts
- The Anti-Phishing Working Group’s fraud reporting portal
- IC3.gov to alert national cybercrime authorities
- Web host abuse contact emails if identifiable in domain WHOIS records
Reporting fake support scams helps get fraudulent sites shut down more quickly before they compromise additional accounts. Documentation aids investigations and protections for the Facebook community.
Hopefully these FAQs provide ample awareness of the latest Meta Business help site phishing scam threatening Facebook users through convincing imitation interfaces and warnings. Take care validating any links prior to entering account details to keep profiles secure.
Conclusion: Verify Support Sites to Avoid Meta Business Scam Risks
Scammers design fake help sites mimicking Facebook’s interfaces to steal account credentials and personal data. Avoid entering login emails, passwords or sensitive details on any sites reached through violation warning links.
Compare URLs and site content elements closely to Facebook’s real support centers. Enable enhanced login approvals to require identity confirmation stopping phished accounts from misusing your profile and connections.
Carefully vet links redirecting off Facebook to protect your account’s security against customized social media phishing threats. Prioritize safety taking actions only through official help channels.