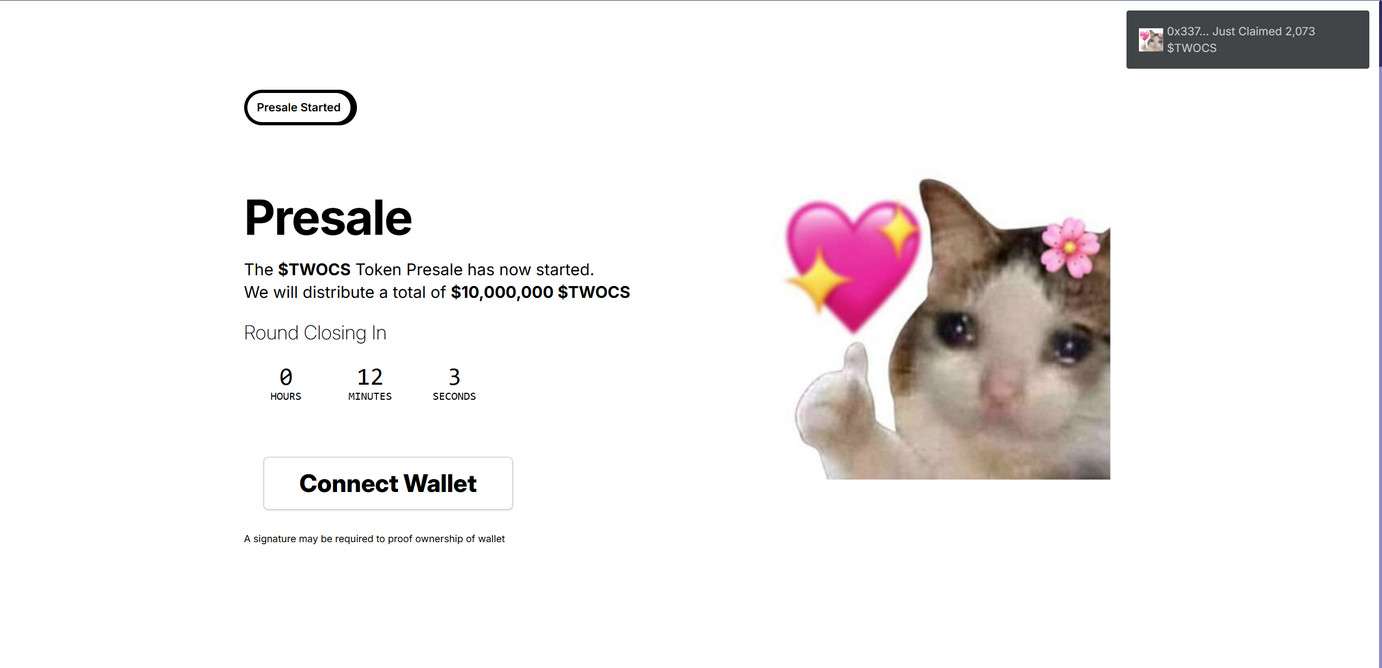
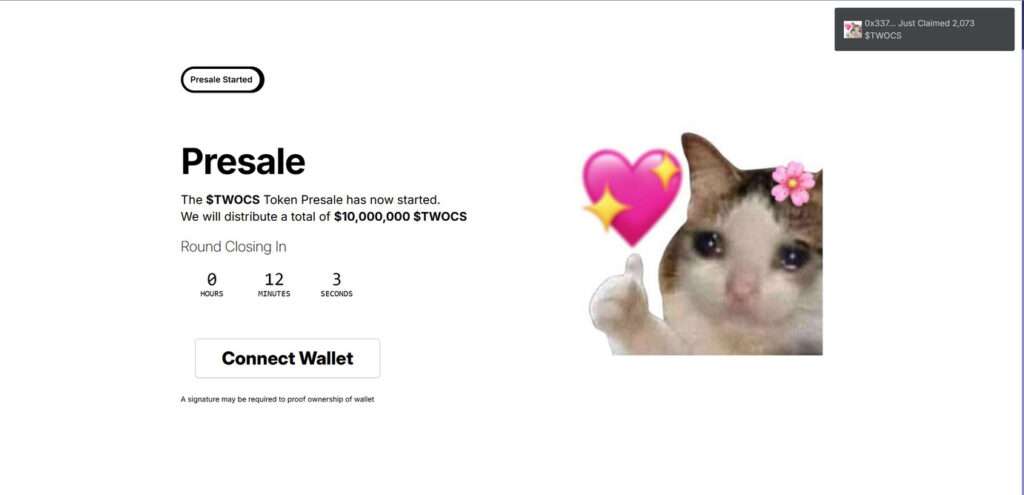
A seemingly promising token presale is making the rounds online, offering early access to a new cryptocurrency called $TWOCS. Promoted as an exclusive opportunity to invest in a presale with a $10 million token pool, it has lured unsuspecting users with flashy language and urgent messaging. But this isn’t a legitimate project. It’s a phishing scam designed to drain digital wallets and steal funds.
If you’ve come across a presale hosted on .live, .xyz, or similar domains, do not connect your wallet. This scam is not affiliated with any known crypto project and is solely designed to exploit unsuspecting investors. In this article, we break down how the scam works, what it aims to steal, and most importantly, how you can protect yourself.
Scam Overview: The Truth Behind the $TWOCS Token Presale
The so-called $TWOCS Token Presale presents itself as a legitimate cryptocurrency offering. On the surface, it mimics the appearance of real presale dashboards used in blockchain launches. The site claims it is distributing $10 million worth of $TWOCS tokens, creating urgency with countdown timers, referral bonuses, and early allocation messaging.
The scam is hosted on wiflove[.]live, a deceptive domain designed to look credible. But like most phishing scams, it may also operate under alternative domain names to avoid being shut down or blacklisted. It’s important to understand that no real $TWOCS token exists, and the campaign has no affiliation with any recognized blockchain project or platform.
False Promises Used to Build Trust
Some of the statements from the scam site include:
- “The $TWOCS Token Presale has now started”
- “We will distribute a total of $10,000,000 $TWOCS”
- “A signature may be required to prove ownership of wallet”
- “Connect Wallet”
These messages are designed to encourage users to take fast action, usually without questioning the legitimacy of the offer. The layout includes options to connect through:
- WalletConnect (via QR code)
- Trust Wallet
- MetaMask
- Uniswap Wallet
Additionally, the site includes a prompt for users who do not yet have a wallet, inviting them to “Get started” and thus expand the potential pool of victims.
What the Site Is Really After
This scam isn’t about selling a token. It’s about gaining unauthorized access to cryptocurrency wallets. Once connected, victims are prompted to sign a smart contract that appears benign but in fact gives the scammer control over wallet assets.
The drainer script is typically engineered to do the following:
- Transfer native assets (ETH, SOL, BNB, etc.)
- Withdraw stablecoins (USDT, USDC, DAI)
- Target valuable tokens or NFTs
- Continue operating in the background until detected
The most alarming aspect is that many of these transactions are not obviously malicious. They may not even trigger wallet alerts, and users might not notice the missing funds until it’s too late.
No Audit, No Whitepaper, No Team
Legitimate crypto presales usually offer:
- A verifiable team
- A roadmap
- Smart contract audits
- Whitepapers explaining tokenomics
The $TWOCS scam offers none of these. There is no visible team, no smart contract transparency, and no whitepaper. The entire operation is designed around psychological manipulation: urgency, exclusivity, and ease of access.
How the $TWOCS Scam Works: Step-by-Step Breakdown
This scam follows a carefully orchestrated sequence of steps, exploiting trust and urgency to achieve its goal of draining user wallets. Below is a breakdown of each phase in detail.
Step 1: Traffic Generation Through Social Media and Messaging Apps
Scammers spread the fake presale primarily via:
- Twitter/X posts
- Telegram messages
- Discord DMs
- Paid ads on crypto-related websites
They use phrases like:
- “Limited-time presale now live!”
- “$10M $TWOCS tokens available!”
- “Connect wallet to claim your airdrop”
These messages often include shortened URLs to obscure the real domain and avoid detection.
Step 2: A Professional-Looking Website
The fake website is visually convincing. It uses common design elements found in real DeFi dashboards:
- A countdown timer (“Round Closing In: 0 Hours 13 Minutes 17 Seconds”)
- A “Connect Wallet” prompt
- Logos of popular wallets
- A clean and simple UI to appear trustworthy
Everything on the site is tailored to lower skepticism and push users toward wallet interaction.
Step 3: Wallet Connection
When the user clicks “Connect Wallet,” they are presented with standard options:
- MetaMask
- Trust Wallet
- WalletConnect
- Uniswap Wallet
The site may also encourage users to create a new wallet if they don’t have one, expanding the attack surface.
Step 4: Signature Request and Smart Contract Approval
After connecting, users are prompted to sign a message or approve a transaction under the guise of verifying ownership or reserving tokens. This is where the damage begins.
- The signature authorizes a smart contract
- The contract has access to move funds
- Some contracts remain active in the background
Because the action doesn’t always result in immediate fund loss, victims may not recognize the theft for hours or even days.
Step 5: Drainer Activates and Moves Assets
Once approved, the drainer contract automatically scans for valuable assets, including:
- High-value tokens
- Stablecoins
- NFTs
- DeFi LP tokens
Funds are often funneled through multiple wallets to launder the stolen assets before reaching the scammer’s final address.
Step 6: Victim Remains Unaware
Many victims don’t realize they’ve been scammed until they:
- Open their wallet and notice missing assets
- Receive token transfer alerts (if enabled)
- Check Etherscan or Solscan and spot unauthorized transactions
Some smart contracts even bypass wallet alerts by using less common transaction methods or gasless approvals.
What to Do If You Have Fallen Victim to the $TWOCS Presale Scam
If you connected your wallet or signed a transaction on the scam site, follow these steps immediately:
1. Revoke Smart Contract Permissions
Use trusted tools to revoke access to the malicious contract:
Search your wallet address and remove any suspicious approvals.
2. Transfer Remaining Assets to a New Wallet
Assume the compromised wallet is no longer safe. Move all tokens, NFTs, and other assets to a newly created wallet using a different seed phrase.
3. Use a Hardware Wallet Going Forward
Hardware wallets offer a much higher level of protection. They keep your private keys offline, reducing the risk of future phishing or contract exploits.
4. Scan Your Device for Malware
Ensure your computer or smartphone isn’t infected with spyware or malicious browser extensions. Use a trusted antivirus or antimalware tool to scan your system.
5. Report the Scam
Help others avoid the same fate by reporting:
- The domain to Google Safe Browsing
- The scam to Chainabuse.com
- Social media accounts or ads that promoted the scam
6. Monitor Wallet Activity
Keep a close eye on the original wallet for any delayed transactions or unusual approvals. Tools like DeBank can help visualize wallet permissions and token flows.
7. Share Your Experience
Spread the word to others in the crypto space. Post on:
- r/CryptoCurrency
- Web3 Discord groups
- Telegram scam alert channels
Community awareness can stop future victims from falling into the same trap.
Frequently Asked Questions (FAQ) About the $TWOCS Token Presale Scam
What is the $TWOCS Token Presale scam?
The $TWOCS Token Presale scam is a fraudulent cryptocurrency scheme presented as an exclusive token sale event. It lures users into connecting their digital wallets to a fake website, such as wiflove[.]live, and tricks them into signing malicious smart contracts. These contracts allow scammers to drain funds directly from users’ wallets. This scam has no affiliation with any real blockchain project or token.
Is there a legitimate $TWOCS token?
No. There is no official or verified cryptocurrency called $TWOCS. The presale is completely fake and was created solely to exploit users through phishing and wallet-draining tactics. Any claim of a real $TWOCS token should be considered fraudulent until proven otherwise through trusted crypto sources.
How does the $TWOCS scam work?
Victims are invited to join a token presale, often promoted via social media or deceptive advertising. Once on the site, users are prompted to connect their crypto wallet and sign a transaction to “verify ownership.” In reality, this signature grants access to a malicious contract that silently transfers funds and assets from the victim’s wallet to a scammer-controlled address.
What happens when I connect my wallet?
When you connect your wallet and approve the transaction, you may unknowingly authorize a smart contract that enables ongoing access to your assets. This allows the scammers to withdraw funds, tokens, or NFTs without further approval or interaction. The effects may not be immediate, which is why many victims only discover the theft days later.
Is signing a wallet transaction always dangerous?
Not always—but in this case, yes. Wallet signatures can authorize different actions depending on the contract. In this scam, the prompt to “prove ownership of wallet” masks the fact that you’re giving away spending permissions. Always read and verify what you’re signing, especially on unfamiliar platforms.
Where is the scam hosted?
The $TWOCS scam is currently hosted at wiflove[.]live, though scammers may use other domains to avoid detection. It’s common for phishing schemes to rotate URLs and launch cloned versions across different hosting services.
What are the signs that a crypto presale is a scam?
Key red flags include:
- Requests to sign wallet transactions without clear purpose
- Fake countdown timers to create urgency
- Unverifiable token names and no presence on CoinMarketCap or CoinGecko
- Generic promises of “guaranteed allocation” or high returns
- Hosting on suspicious or non-standard domain names
- No verifiable team or official project announcements
What should I do if I connected my wallet?
If you interacted with the scam, take these steps immediately:
- Revoke all token approvals using tools like revoke.cash
- Transfer your remaining funds to a new, uncompromised wallet
- Run a full malware scan on your device
- Report the scam to phishing databases, blockchain security services, and the crypto platforms you use
- Notify other users via social media and crypto communities
Can I recover funds stolen through a drainer?
Unfortunately, once a malicious smart contract drains a wallet, the transaction is irreversible due to the nature of blockchain technology. Unless law enforcement intervenes and the attacker is caught quickly, recovery is unlikely. Prevention and fast response are the best defenses.
How can I avoid falling for similar scams in the future?
To stay safe from wallet drainers and fake presales:
- Always verify a token’s legitimacy through trusted sources
- Never sign wallet transactions from unfamiliar or suspicious sites
- Use a hardware wallet for larger holdings
- Regularly check and manage token approvals
- Follow official project accounts for updates and announcements
- Be skeptical of unsolicited airdrops, referrals, or investment opportunities
The Bottom Line
The $TWOCS Token Presale is not a real crypto project. It’s a wallet-draining scam hosted on wiflove[.]live and potentially other domains. By tricking users into connecting their wallets and signing malicious contracts, scammers are able to steal digital assets with little resistance.
Always verify a presale through official sources. Never sign unknown smart contracts. And if something feels off, trust your instincts and walk away.
Stay safe. Stay alert. Protect your wallet.