If you have ever wondered how someone could lose access to their WhatsApp account in a matter of seconds, the answer lies in cleverly crafted scams. Cybercriminals do not need advanced malware or sophisticated hacking tools, instead they exploit trust, urgency, and empathy. Bitdefender Labs researcher Razvan Gabriel Gosa has been monitoring a rapidly expanding campaign that exploits WhatsApp users through fraudulent voting contests to take over accounts and steal money.
Read on for a detailed, practical guide that will show you exactly how this scam operates, how to spot it, and precisely what to do if you have been targeted or compromised.
Scam Overview
The “Vote for My Child” scam is a targeted social engineering campaign that uses WhatsApp as both lure and propagation channel. At its core, the scam presents a fake voting contest supposedly designed to help a child win a scholarship, a prize, or a chance to perform. The story is emotionally compelling, and the message often arrives from a trusted contact. The campaign is notable for its speed and scale. In recent months, Bitdefender research has documented a rapid expansion across Central and Eastern Europe, followed by spillover into Western Europe and other regions.
What the scam looks like in practice
A typical interaction begins with a WhatsApp message. The sender is either an account that is already compromised and controlled by attackers, or it is a real contact whose account has been hijacked and used to spread the message. The message reads like a personal request. Sample text often looks like this:
“Hi! Please vote for Adeline in this contest, she is the daughter of a close friend. The main prize is a scholarship abroad. Thank you so much!”
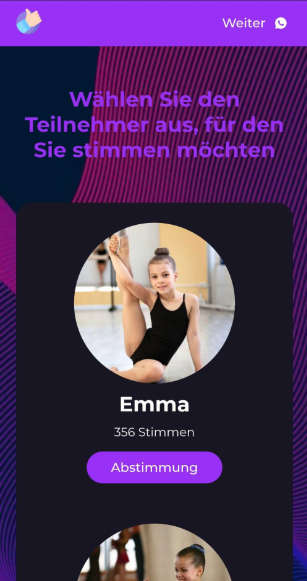
The message includes a link to a vote page. The domain name and page design are made to look credible. Photos of children in dance or gymnastics positions appear on the site, there are counters showing votes, and there are vote buttons that encourage immediate action. The page promises prizes and gives a sense of legitimacy with images, social proof, and fake statistics.
The technical trick
To “vote” users are asked to enter their phone number. The fake contest triggers an SMS or WhatsApp verification code, and the site asks the user to input that six digit code on the page. This is the critical point. That six digit code is the WhatsApp verification code that pairs an account with a device. By entering that code into the phishing page, the victim hands it directly to the attacker. With the code, attackers register the victim’s phone number on their own device and gain full access to the WhatsApp account.
Once attackers control a WhatsApp account, they send the same fraudulent message to everyone in the victim’s contacts. Because the message appears to be from a trusted contact, the success rate is high. Attackers often escalate the fraud by using the hijacked account to request money from contacts under urgent pretenses. Common demands include amounts like 1,800 RON (approximately 360 euro), followed by additional extortion requests. The account may then be used for other scams, sold, or abandoned. In some cases, aggressive spamming causes WhatsApp to suspend the account, causing confusion and further leverage for attackers to extort the original owner.
Scale and infrastructure
This campaign is not one-off. According to Bitdefender, attackers have deployed hundreds of fraudulent domains and unique URLs. During a monitored period they used around 177 fraudulent domains and 554 unique URLs, targeting thousands of users over a short timeframe. The attackers maintain a catalog of pages that mimic voting contests, tweaking content and domains to evade detection and maximize reach.
Motive and profit model
The immediate motive is financial gain, but the pathway is layered. After takeover, attackers:
- Spread the scam to contacts to harvest more verification codes and hijack additional accounts.
- Use the hijacked account to request money from contacts, often claiming urgent distress.
- Offer to sell or rent hijacked accounts to other fraudsters.
- Use accounts to disseminate malware or other malicious links.
- Perform identity theft or fraud that leverages the identity and trust of the hijacked user.
The result is a compound effect. Each takeover multiplies access to new victims. Because the scam uses social proof, the conversion rate can be high, making the operation scalable and profitable.
Why this scam is effective
Several factors make this scam successful:
- Trust exploitation. The message seems to come from someone you know. People are far more likely to act on a favor request from a friend.
- Emotional hook. Stories about children, scholarships, and prizes trigger empathy and urgency.
- Ease of execution. The attacker only needs a convincing webpage and the victim’s complacency to gather a one-time code. No malware or advanced hacking is required.
- Rapid propagation. WhatsApp is used to spread the scam quickly through social networks of friends, family, and colleagues.
- Limited technical awareness. Many users do not understand that the WhatsApp six digit code is a key to account control.
This combination of social engineering, legitimate-looking assets, and the technical weakness of human-mediated authentication makes the campaign dangerous. The next section unpacks the step-by-step mechanics so you can see exactly where the risk occurs and how to block it.
How The Scam Works
Below is a detailed reconstruction of the full attack chain. Understanding each step will help you spot indicators of compromise and stop the attack before it can escalate.
Step 1: Reconnaissance and domain preparation
Attackers prepare by registering domains that sound like contest pages, for example names with dance, competition, or contest keywords combined with local language variants. They create multiple variants and designs to target specific countries and languages.
Key elements of the attacker preparation:
- Register dozens to hundreds of domains to cycle when one becomes blocked.
- Build multiple phishing templates showing images of children, vote counters, and call to action buttons.
- Localize the pages to match target languages, currencies, and cultural cues.
- Host pages on distributed infrastructure, sometimes using bulletproof hosting or fast-changing hosting providers.
- Configure simple form handlers to capture phone numbers and codes, and forward them to operators.
This preparation stage is mainly about scale and camouflage. By investing in many pages and languages, attackers lower detection probability and increase reach.
Step 2: Initial message seeding and account compromise
There are two main ways an initial message is seeded into WhatsApp contact networks:
- Compromised accounts are used to seed messages. The attackers already have a set of hijacked WhatsApp accounts that they control. Using these accounts, they send personalized messages to contacts, often phrased to appear as a direct favor.
- Compromised or purchased contact lists. Attackers may buy or obtain contact lists, but the most effective approach is using hijacked accounts because messages from a trusted contact are more likely to succeed.
A sample seeded message might include:
“Hi! Please vote for Adeline in this contest, she’s the daughter of a close friend. The main prize is a scholarship abroad. Thank you so much!” plus a shortened link or a link that appears harmless at glance.
Because the link appears to be from a friend, the recipient is trained to trust it, which is exactly the attackers’ intent.
Step 3: The lure page and the decision point
When the recipient clicks the link, they land on a voting page that looks professional. The page will contain some or all of the following elements:
- A photo of a child in a dance or gymnastics pose.
- A large vote button.
- Fake counters showing votes, supporters, or rankings.
- Testimonials or short blurbs that simulate success stories.
- A prompt to enter a phone number to cast a vote.
- Language and currency tailored to the target audience.
Design matters. The page uses a mix of credibility markers so the visitor feels they are on a legitimate site.
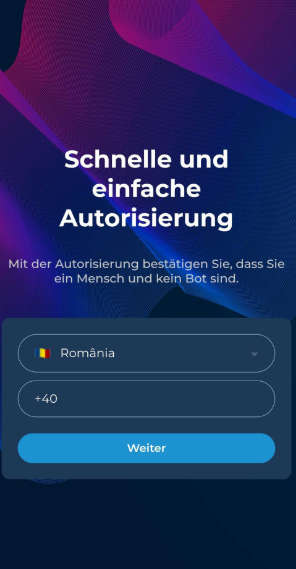
At this stage the page asks for the victim’s phone number. Many users accept this as a normal step to prevent multiple frauds or fake voting. That is the first critical mistake.
Step 4: Triggering the verification code
Once the user provides their phone number, the page or the attacker’s backend triggers WhatsApp’s registration process for that phone number. The system sends a one-time verification code to the phone number via SMS or via WhatsApp message.
Two things to note here:
- The attacker does not need to compromise WhatsApp to trigger a code. WhatsApp will send a code to the number any time a registration is attempted.
- The attacker only needs the user to read the code arriving on their device and retype it on the phishing page.
Step 5: Social engineering the user to share the verification code
The phishing page prompts the user to enter the six-digit WhatsApp verification code they will receive. The prompt is presented as a normal step to complete the vote, often with reassuring text that suggests the code is required only to verify a human voter and to avoid bots.
The text could be framed like:
“To make sure real people vote, please enter the code that will be sent by WhatsApp to your phone.”
This social engineering is powerful. Most users do not realize this code is the same code used to control WhatsApp accounts. Once they provide it, they have handed the attacker the key.
Step 6: Account take over
After the user enters the code, the attacker immediately uses that code to complete the registration on their side. WhatsApp pairs the phone number with the attacker’s device and logs the victim out. The attacker now has full access to messages, contact lists, profile pictures, and group memberships. Important details:
- Account access is immediate. The attacker can read messages received thereafter and use the account to send messages.
- WhatsApp will show a message on the victim’s device that the account was registered on a new device. At this point some users may notice but may not act quickly enough.
- If the victim has enabled two-step verification with a PIN, the attacker will be blocked unless they also have the PIN. However, many users do not enable two-step verification.
Step 7: Rapid propagation through hijacked account
Once the account is compromised, attackers use it to spread the same scam to the contact list. Because the message originates from a trusted contact, conversion rates are higher. The compromised account may post the same vote message or a slightly modified version to groups and contacts.
Attackers often use the following propagation tactics:
- Send targeted messages to top contacts and groups.
- Post links in active group chats where members will see the message.
- Send a short personal message with the fake link to individuals to increase click-through rate.
Propagation is automated or semi-automated. The attacker may run scripts or use multiple devices to broadcast messages quickly.
Step 8: Financial fraud and extortion
After hijacking accounts, attackers commonly attempt direct financial fraud. They reach out to close contacts claiming an emergency or urgent need for money. Common scripts include:
- “I am traveling and my card was blocked, please lend me 1,800 RON and I will pay you back.”
- “I lost my wallet abroad, please send money for tickets.”
- “I am in an emergency, I need 2,000 RON immediately.”
These messages often come with plausible details and pressure tactics. Because they appear to be from someone the recipient trusts, the requests can succeed.
Attackers may also take a two-step approach: first harvest more accounts via the voting page, then use the larger network for a subsequent extortion campaign.
Step 9: Account monetization and abandonment
After immediate exploitation, attackers may monetize the account further by:
- Selling the compromised account details on underground forums.
- Using the account to send premium rate or subscription links.
- Using the account as a trust anchor for other fraud schemes.
- Leaving the account in place to harvest more victims.
If spamming triggers account suspension by WhatsApp, attackers may exploit that too by contacting the original owner with an ultimatum that requires payment for restoration.
Step 10: Clean up and persistence
Some attackers implement persistence to regain access if the victim re-registers. They may have created secondary recovery paths or stored backup data. Because the initial entry vector is a simple code exchange, attackers rarely need long term persistence to cause damage.
Summary of the critical failure point
The exact technical weakness exploited is simple: WhatsApp’s one-time verification code is a secret that pairs an account to a device. That code is sent to the legitimate owner, but if the owner shares it with an attacker, the attacker can register the account on their own device. No malware, no password cracking, no phone sniffing is necessary. The human factor is the vulnerability.
Signs You Have Been Targeted or Compromised
Recognizing the attack quickly reduces damage. Here are indicators that you or a contact may be targeted or compromised:
- You receive an unexpected WhatsApp message from a contact asking to vote for a child or join a contest with a link.
- You see an authorization code message from WhatsApp but did not request a login on another device.
- Your WhatsApp shows “Registered on another device” or you are logged out unexpectedly.
- Friends or family report receiving suspicious messages from your account that you did not send.
- You notice changes to profile picture, status, or account settings you did not make.
- You receive payment requests via WhatsApp from contacts who have never asked for money before.
If you see any of the above, act quickly. The next section lists exact steps to take with numbered priorities.
What to Do If You Have Fallen Victim to This Scam
If you suspect your WhatsApp account has been compromised, quick and precise action can limit harm. Below is a detailed, numbered list of actions you should take immediately, with explanations and examples. Treat this as an emergency checklist.
1. Reclaim your WhatsApp account immediately
- Open WhatsApp on your phone and try to register your phone number. You will receive a six digit code. Enter the code to reclaim the account.
- If the attacker enabled two-step verification with a PIN you do not know, you will be blocked from regaining access until the forced waitout period expires. Keep reading the next steps if this happens.
Why this helps: Re-registering removes the attacker’s session and gives control back to you. If you can regain your account quickly you can stop the spread of messages.
2. Enable two-step verification if you do not already have it
- Once you regain control, go to Settings > Account > Two-step verification and set a PIN.
- Add an email address for recovery if WhatsApp asks for one.
Why this helps: Two-step verification adds a second layer of defense so attackers who have a code cannot re-register your number without the PIN.
3. Notify your contacts immediately that your account was compromised
- Use an alternate channel such as SMS, a phone call, or email to tell your contacts not to click any links they received from your WhatsApp account.
- Ask them to delete any suspicious messages and to ignore any requests for money.
Why this helps: The main damage vector is propagation to trusted contacts. Stopping that spread reduces additional victims.
4. Report the fraud to WhatsApp and block affected numbers
- In WhatsApp, open the chat with the suspicious message, tap the contact name, and choose “Report contact” and “Block”.
- Use WhatsApp’s in-app support to explain the situation. Provide screenshots of the phishing page and messages if possible.
Why this helps: Reporting helps WhatsApp take down content and suspend abusive accounts. Blocking prevents immediate re-contact by the same number.
5. Change passwords and check linked accounts
- Even though WhatsApp uses phone number verification, attackers may attempt to use your account data to access other services. Change passwords for email, social networks, and any account that uses your phone number for recovery.
- Review and remove suspicious linked devices or sessions on platforms that offer them.
Why this helps: Attackers often try to escalate privileges or pivot to other accounts.
6. Contact your bank and payment providers
- If you sent money or provided payment details via WhatsApp, contact your bank immediately. Request a freeze or reversal where possible.
- Monitor accounts for unauthorized transactions.
Why this helps: Early contact improves the chances of reversing fraudulent transfers and reduces financial loss.
7. Report to local law enforcement and cybercrime units
- Submit a report to your local police describing the scam and providing evidence such as screenshots, logs, and timestamps.
- If your country has a national cybercrime reporting portal, file a complaint there.
Why this helps: Law enforcement records help track threats and may be necessary for financial recovery or legal actions.
8. Preserve evidence
- Take screenshots of the phishing page, the messages, and any verification SMS or emails.
- Save timestamps and any transaction IDs if money was sent.
Why this helps: Evidence is critical for investigations, disputes with banks, or insurance claims.
9. Inform your mobile carrier if needed
- If attackers requested porting your number or if you experience unauthorized SIM changes, contact your mobile operator immediately.
- Request that they flag your account for potential SIM swap attempts and ask about additional protections such as port freeze.
Why this helps: SIM swap schemes can allow attackers to intercept codes and advance the attack. Carrier action can stop this escalator.
10. Seek professional help for identity theft
- If attackers had access to other sensitive data or social security numbers, consider identity theft protection services. These services can monitor credit and identity records.
- In severe cases, consult a legal advisor for next steps.
Why this helps: Identity theft can have long term consequences that require monitoring and remediation services.
11. Follow up with WhatsApp and update your contacts
- After reclaiming your account and securing it, send a group message or broadcast announcing the compromise and confirming the account is secure.
- Provide a simple checklist of what contacts should do if they clicked the link or sent money.
Why this helps: A public confirmation from you prevents confusion and reduces secondary attacks.
12. Review and update privacy settings
- Restrict who can see your profile photo and status to contacts only.
- Disable auto-download of media for unknown contacts and review group join settings.
Why this helps: Reducing the public surface area of your account decreases opportunities to abuse your profile for social engineering.
How to Recover Your Account and Reduce Damage
Recovering from a successful takeover can be stressful. This section expands on the recovery steps with additional details and recovery timelines.
Immediate recovery actions
- Register the account on your device with the verification code. This will log out the attacker.
- Reset two-step verification by enabling a PIN and adding an email address for reset.
- Review current sessions for any linked web or desktop sessions and log them out.
What if the attacker enabled two-step verification already?
If the attacker enabled the two-step verification and you cannot re-register, you must wait for the mandatory reset period that WhatsApp imposes, usually seven days. During that time, you may be unable to log in. Important steps:
- Contact WhatsApp support via email or in-app form and report the account takeover. Include your phone number in international format and all evidence.
- Contact your carrier if you suspect SIM swap or unauthorized porting. Ask them to lock any port requests.
- Use alternate communication channels to notify contacts of the situation.
Payment recovery
- If you sent money via bank transfer, share evidence with your bank and request a fraud investigation.
- If you used peer-to-peer payment apps, contact those services immediately and follow their dispute procedures.
- Keep records of requests for reversal and case numbers.
Long term monitoring
- Monitor financial statements for several months.
- Consider placing a fraud alert or credit freeze with credit bureaus if identity details were exposed.
- Regularly review account recovery options and update recovery emails and phone numbers.
Prevention Checklist: Protect Yourself and Your Contacts
This checklist helps reduce risk and is optimized for clarity and actionability.
Account security
- Enable WhatsApp two-step verification and set a strong PIN.
- Add an email address to your two-step verification for recovery.
- Limit who can see your profile photo, about, and status.
- Disable auto-add to groups if possible.
Behavioral practices
- Never share a WhatsApp verification code with anyone, even if they claim to be from WhatsApp.
- Treat any unexpected verification code as suspicious. If you get one, inform contacts that your account may be at risk.
- Verify requests for money with a secondary channel, such as a phone call. If a friend messages you asking for funds, call them before sending anything.
- Avoid entering verification codes on websites. If a site asks for a WhatsApp code, it is almost certainly fraudulent.
Technical hygiene
- Use a reputable mobile security product that can detect phishing pages.
- Keep your phone OS and apps updated.
- Do not click unfamiliar links from contacts without verifying context first.
- Use strong passwords for email accounts and enable multi-factor authentication that does not rely on SMS alone.
Community actions
- Educate family members, particularly older adults, about the scam. They are often targeted due to lower familiarity with these tricks.
- Share this article or a simplified checklist in community groups, school parent groups, and workplace communications.
- Encourage local organizations that run legitimate contests to publish clear guidance stating that no official contest will ask for a WhatsApp verification code.
The Bottom Line
The “Vote for My Child” WhatsApp scam is a simple but powerful social engineering attack that leverages trust and empathy to harvest WhatsApp verification codes. Attackers then use hijacked accounts to propagate scams and extort money. The attack is scalable because it relies on human behavior more than complex technology. The good news is that clear prevention steps work: never share verification codes, enable two-step verification, verify money requests over a second channel, and educate your contacts.
If you are targeted, act immediately. Reclaim your account, enable two-step verification, notify contacts, and report the incident to WhatsApp, your bank, and law enforcement. Prevention and quick response are the best defenses.
Frequently Asked Questions
What is the “Vote for My Child” WhatsApp scam?
The “Vote for My Child” scam is a phishing and social engineering campaign that targets WhatsApp users by pretending to be a harmless voting contest. Victims receive a message from a friend or family member asking them to vote for a child in a contest, usually involving scholarships or talent competitions. The message contains a link to a fake voting website that asks the user to enter their phone number and the six-digit WhatsApp verification code they receive. Once the victim enters that code, scammers gain full access to their WhatsApp account and use it to spread the same scam or steal money from their contacts.
How does the “Vote for My Child” scam work step by step?
- Initial contact – Victims receive a WhatsApp message from a known contact asking them to vote for a child in a contest.
- Clicking the link – The message includes a link that leads to a fake website that looks like a real contest or event page.
- Fake voting form – The page asks users to enter their phone number to “confirm the vote.”
- Verification code request – The website tells users they will receive a code to verify their vote and asks them to enter it on the page.
- Account hijack – The six-digit code is actually the WhatsApp verification code. Once the user provides it, the attackers take over their WhatsApp account.
- Propagation and fraud – The scam spreads through the victim’s contacts, and attackers use the hijacked account to request money or further verification codes.
Why is this scam so successful?
The “Vote for My Child” scam succeeds because it exploits trust and emotion. People tend to believe messages from friends and family. The emotional story about helping a child makes the request seem genuine. Additionally, most users are unaware that their WhatsApp verification code can give attackers total control of their account. This combination of emotional manipulation and lack of awareness makes the scam highly effective.
What countries are being targeted by this WhatsApp scam?
Research from Bitdefender shows that this scam is most active in Central and Eastern Europe, but it has expanded globally. The top targeted countries include:
- Poland – approximately 41% of detected cases
- Romania – around 29%
- Germany – about 20%
- Czech Republic, Italy, and Austria – smaller but ongoing campaigns
There are also reports of incidents in Spain, the United Kingdom, the United States, and Kazakhstan. Attackers adapt messages and fake websites to local languages and cultural contexts to make them more convincing.
What kind of websites are used in this scam?
Scammers use domains that sound like legitimate contest or event pages. They include keywords such as “dance,” “battle,” or “contest” combined with country names or common terms. Examples of fraudulent domains linked to this campaign include:
- best-dance[.]live
- dansului-battle[.]live
- dancebattle[.]life
- thebestdance[.]world
- gimnast[.]life
These domains are constantly changed and replaced to avoid detection and blocking by security systems.
What happens if I enter my WhatsApp verification code on the fake page?
If you enter your WhatsApp verification code on a phishing page, you immediately hand over control of your account to cybercriminals. They will use that code to register your WhatsApp account on their device. You will be logged out, and they will have full access to your messages, groups, and contact list. The attackers will then use your account to send fraudulent messages to your contacts and may even demand money from your friends and family.
Can I recover my WhatsApp account after it’s hacked?
Yes, you can recover your WhatsApp account, but you must act quickly. Open WhatsApp, enter your phone number, and request a new verification code. Enter that code to regain access to your account. This will automatically log out the attackers. If they have activated two-step verification, you may need to wait for a seven-day period before you can log in again. During this time, report the incident to WhatsApp support and inform your contacts not to interact with any suspicious messages coming from your account.
What should I do if I received a suspicious voting link on WhatsApp?
Do not click the link, and do not forward it to anyone. Delete the message immediately. Contact the person who sent it through another channel, such as a phone call or text message, to verify whether they intentionally sent it. If they confirm they did not, advise them that their account might be compromised. Reporting the message to WhatsApp helps prevent the scam from spreading further.
How can I protect myself from the “Vote for My Child” WhatsApp scam?
Follow these preventive steps to stay safe:
- Never share your WhatsApp verification code with anyone, even friends or WhatsApp representatives.
- Enable two-step verification in WhatsApp and set a secure PIN and recovery email.
- Be cautious with links received through WhatsApp, especially if they promise rewards or ask for votes.
- Confirm messages directly with the sender through a different channel before clicking any link.
- Educate family and friends about this scam so they recognize it if it appears.
- Keep your apps updated to ensure you have the latest security patches.
What if I sent money to the scammer?
If you have sent money to someone through WhatsApp who later turned out to be a scammer, contact your bank or payment provider immediately. Report the transfer as fraudulent and request a reversal or investigation. Provide as many details as possible, including the phone number, messages, and any transaction information. Report the incident to local law enforcement and file a complaint with your national cybercrime reporting center.



