This article tries to describe in detail the User Account Control (referred to as UAC) under the Windows 7 operating system and it is targeted at novice users that might not be accustomed to this feature. It also discusses UAC-s efficiency under an administrator account and proposes a more secure way to turn off the prompts.
A bit of history
One of the most basic requirements for a secure operating system is the ability to control access to resources by granting or denying access to individual users. For a long time, the Windows operating system was a single user system. With the Internet being mostly non-existent for home users and most personal computers having only a single user at a time, most people didn’t feel the need for a multi-user OS. The NT family of Windows was a multi-user environment (and the first Windows to receive a C2 level Security) but it wasn’t targeted towards home users. The latest Windows versions for home users (XP, Vista and Windows 7) are based on the NT architecture and are true multi-user operating systems.
Unfortunately crossing from a single-user environment to a multi-user one raised a number of problems. Users are not accustomed to the new security model and perceive numerous security features as annoyances. And who can blame them when using a non-administrator account on Windows XP is almost impossible. Programmers face similar problems as well. This is where UAC comes in to facilitate the usage of a non-administrator account on a Windows OS.
How UAC works?
UAC enhances security by allowing you to use standard-user wrights while providing an easy method for elevating to administrator if such elevation is needed. There is no need to switch user, log-off or use the Run as administrator command.
Important: UAC is intended to help people be more secure, but it can’t ensure security on its own.
The user interacts with UAC through one of the prompts it displays, called elevation prompts. Most likely the prompts you are receiving look slightly different than the one bellow. This is the prompt UAC displays to standard users.
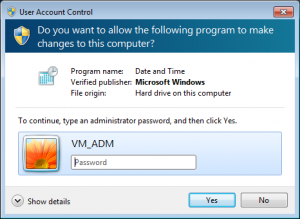
While using a standard user account you have adequate privileges allowing you to perform usual tasks such as browsing the Internet, sending mail or playing digital media. But you do not have the privileges required to perform administrative tasks, such as installing software or changing important system settings. Those privileges are reserved to administrators. However each time you try to perform an administrative task, UAC displays a notification prompting you for administrative credentials. This UAC notification is called the Credential prompt. By answering the Credential Prompt with the correct local administrator password, your standard user account is elevated to an administrator account that allows you to perform the task.
UAC works differently for an administrator account. When an administrator logs on to the computer, his account behaves similar to a standard user account without administrator privileges. This mode of operation is called Admin Approval Mode. This is the way all administrator accounts created on a Windows 7 computer run by default. During the Windows 7 Setup process, you provided a name and a password for such an account. Most probably this is the way you are currently using your computer right now. By default, when an administrator tries to perform some administrative tasks, UAC presents him with a Consent Prompt requesting approval to perform the task, but it does not require a password.

Note: Not all administrative tasks trigger a UAC prompt under the default settings. When UAC was first introduced under Windows Vista, Microsoft received a serious number of complains from users who felt that it displayed to many prompts. In Windows 7, Microsoft tried to lower the number of prompts a user receives while still preventing unauthorized changes that might interfere with security. We’ll discuss about this in part 3, for now, just remember that UAC is more effective inside a standard user account, but in that case it also displays more prompts.
By default when the UAC notification is displayed, the desktop is dimmed. The dimmed desktop (called Secure desktop) does not allow other programs to run until you respond to the notification. This prevents malicious software from interfering with the notification (by spoofing keystrokes or mouse clicks to it, for example). Although this feature can be turned off by an administrator, it is not recommended to do so.
Note: Windows 7 also includes a built-in administrator account that runs with full administrative privileges and does not receive UAC prompts. The user-name for that account is “Administrator” and it has no password but it is disabled by default.
File system and registry virtualization is a technology working behind the scenes to help many applications that require some administrative rights to run correctly without them. For example, some applications store settings or user data in areas of the registry or file system that are meant to be used only by the system. This is an unnecessary use of administrative rights and programmers should avoid such issues when designing their applications. The most common mistake is storing user settings for a specific applications inside the Program Files folder instead of using the Users folder.
To show how file system virtualization works, I’ve opened a Command Prompt with standard user rights and tried to create a new file inside the System folder. Because file system virtualization is disabled by default for the Command Prompt, I’ve received an error (marked as [1] in the screenshot below). After enabling virtualization for Command Prompt and issuing the command again it appears that I can write a file inside the System folder and by issuing the dir command I can actually see that file [2]. In fact, file system virtualization diverted my attempt to write inside the System folder to … and I can see that my text file is there by issuing a dir command inside that folder [3]. My file is not inside the System folder but for what my application is concerned, it looks as if it is there (but only when virtualization is on).

The same happens with the registry. Some legacy applications store their settings in the system-wide portion of the registry (HKEY_LOCAL_MACHINE\Software) instead of the user portion (HKEY_CURRENT_USER\Software), for example. Registry virtualization diverts attempts to write to the system location to one in HKEY_CURRENT_USER (HKCU) while preserving application compatibility.
Important: Turning off UAC disables file system and registry virtualization. As a side effect some applications might not work and for others you will loose existing settings.
UAC elevation prompts
UAC prompts provide contextual information such as the name of the program that triggered the notification along with its publisher name and (if applicable) a link to the digital certificate. Further more, they are color coded as a quick way to determine the trust level of the application that triggered the prompt. This should help users decide when to click “Yes” on a UAC prompt, but before moving on, we need to discuss two aspects.
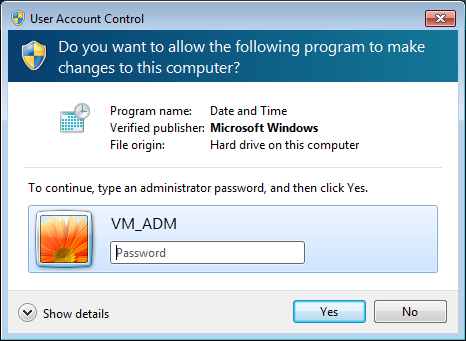
The UAC shield icon appears next to buttons, links or icons to inform you that clicking those items will trigger a UAC prompt. Again, (as mentioned in a previous note) when running with default UAC settings in Admin Approval Mode the prompt might not be displayed when you try to modify certain system settings (like changing the date and time on your operating system).
A digital signature added to a file demonstrates its authenticity. I’ll take for example CCleaner setup package. You can view the digital certificate used to sign the file by right clicking on the file, choosing Properties, Digital signatures, clicking Details after selecting the signature from the list and finally clicking View Certificate. You can see that the setup package was created by Piriform Ltd (the owner of the certificate).

Note: Unfortunately, it is not impossible for malicious software to be digitally signed. If you are not familiar with the author of the file, do a little research before clicking Yes. The Stuxnet malware (currently, proofs indicate that this was a government supported malware) contained files digitally signed with stolen certificates belonging to trusted companies. This is a rare event and the stolen certificates will be promptly revoked (invalidated).
Now we can proceed to describing the various UAC color-coded prompts.
Blue with UAC shield icon: A Windows component (application that is a part of the Windows operating system) digitally signed by Microsoft needs administrative privileges to continue. You can click yes if you are certain that you’ve triggered this prompt (the UAC shield icon was present next to an object you’ve clicked).
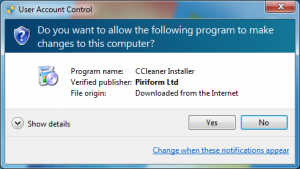
Blue with question mark icon: An executable that is digitally signed by a third-party developer needs administrative privileges to continue. If you’ve triggered this prompt and you fully trust the author of the file, you can click Yes. You can view the digital certificate used to sign this file by clicking Show Details and Show information about this publisher’s certificate.
An important thing to remember is that the digital signature tells you who the author of the file is, but it doesn’t tell you if the author can be trusted. You may click Yes only if you are familiar to the company that created the file.

Yellow with exclamation mark: An executable that that is not digitally signed is accessed. There is no digital signature that can confirm the authenticity of this file. You can click yes if you are absolutely sure that the file can be trusted.
Luckily, most popular applications are digitally signed and you should not see this prompt too often.
Although receiving a certificate costs software authors money and some good free-ware applications are not digitally signed, most malicious files are not digitally signed as well. You should be suspicious when you encounter this prompt and, as a method of precaution, I would recommend uploading the file to an on-line scanning service as VirusTotal.

Red: You attempt to run an executable file that has been specifically blocked by an administrator. You don’t have the option to click yes.
Configuring UAC
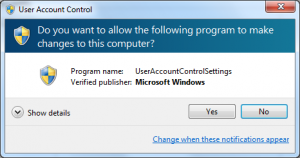
One easy way for an administrator to configure UAC is through the Action Center (Control Panel > System and Security > Action Center). Once there, click the Change User Account Control Settings link. This screen offers you a slider you can use to switch between four security levels for UAC.

- Always notify (top) – This is the highest level and makes UAC in Windows 7 behave similarly to how it used to on Vista. Installing programs and changing Windows settings will trigger a UAC prompt on a secure desktop.
- The default level – Installing programs and changing some security related Windows settings will trigger a UAC prompt on a secure desktop.
- Same as above but the UAC prompts will occur on a normal desktop.
- Never notify – Turns UAC off.
Consequences when turning UAC off
File system and registry virtualization are disabled; as a side effect some applications might not work and for others you will loose existing settings. Protected Mode in Internet Explorer is disabled as well. IE’s Protected Mode is tightly related to virtualization and it is designed to protect the computer by restricting the parts of the system that code running in the IE process can affect. If a malicious web page exploits a bug in IE or an IE plugin, that code will not be able to do damage to the system. While there are no prompts at this setting, the loss of Protected Mode in IE is a significant security disadvantage.
Further configuration can be done through Local Security Policy (found in Control Panel > System and Security > Administrative Tools). Once there navigate to Security Settings – Local Policies – Security Options and you will find 10 settings related to UAC.

Double click on a setting and a window with two tabs will open. The first tab offers you the option to Enable/Disable the setting or a drop-box with the various value that setting can contain. The second tab (entitled “Explain”) offers you complete information about the setting you are trying to edit, including the default value. This information should be sufficient for most users so I will describe only a few of the settings.
Admin Approval Mode for the built-in Administrator account – enables UAC for the built-in “Administrator” account (disabled by default).
Behavior of the elevation prompt for standard users – as the name implies this setting changes the way UAC behaves for standard users. You have the following options:
- Automatically deny elevation requests – Every time a standard user tries to install applications or change Windows settings he receives an error message informing him that the group policy prevents him from doing that action.
- Prompt for credentials – Every time a standard user tries to perform an operation that requires elevation of privilege, the user is prompted to enter an administrative user name and password on a normal desktop.
- Prompt for credentials on a secure desktop – same as above but a secure desktop is used. (Default)
Only elevate executable files that are signed and validated – Enabling this options will prevent any application that is not digitally signed by a vendor inside the Trusted Publishers list on your computer to run. Although powerful this option is highly impractical for home users. The Trusted Publishers list of certificates has to be populated by hand by an administrator and all applications that don’t have a digital signature will not be able to run. This option is disabled by default.
There are a couple of settings referring to User Interface Accessibility programs (UIAccess or UIA) like Windows Remote Assistance for example. If you leave the defaults enabled and connect remotely to your PC you won’t be able to answer the UAC prompts because they are on a secure desktop. Only a user in front of the PC will be able to interact with the prompt. To solve this issue you should change Allow UIAccess applications to prompt for elevation without using the secure desktop to Enabled.
The last setting I will describe is Behavior of the elevation prompt for administrators in Admin Approval Mode. This setting controls the behavior of the elevation prompt for administrators and has the following settings:
- Elevate without prompting – Allows privileged accounts to perform an operation that requires elevation without requiring consent or credentials. If you are determined to turn off UAC, this setting might interest you. As you already know turning off UAC has some possibly undesired consequences. This setting allows you to get rid of the prompts while still keeping UAC on and benefiting from virtualization and Protected Mode in Internet Explorer.
- Prompt for credentials on the secure desktop – It makes UAC display the credential prompt as it does on standard user accounts on a secure desktop.
- Prompt for credentials – Same as above but the prompt is displayed on a normal desktop.
- Prompt for consent on the secure desktop – UAC will display the consent prompt on a secure desktop.
- Prompt for consent – Same as above but the prompt is displayed on a normal desktop.
- Prompt for consent for non – Windows binaries: All the above settings displayed the prompt for all applications and settings (similar to Windows Vista). This setting determines UAC to display the consent prompt on a secure desktop only when non-Microsoft application requires elevation of privilege, or the administrator tries to modify an important Windows setting. (This is the default setting.)
Note for Windows 7 Home users: The Local Security Policy is only available for Windows 7 Professional and higher versions but you should still be able to change the above settings using the Windows registry. The registry keys are found in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System. To modify the behavior of elevation prompt for administrators running in Admin Approval Mode to “Elevate without prompting”, you need to change the value ConsentPromptBehaviorAdmin to 0 (zero). You can consult the Microsoft Technet Library for the complete list of UAC-related registry settings.
UAC controversy
When UAC was first introduced under Windows Vista people considered it to bee an annoying feature displaying too many prompts and making trivial tasks harder to achieve. To address this issues Microsoft altered the behavior of UAC under Windows 7 and lowered the number of prompts it displays considerably. Unfortunately Microsoft might have gone too far. Under the early beta stages of Windows 7 Long Zeng published an exploit on his blog that could silently turn off UAC. The exploit passed keystrokes to an Explorer window, navigating to the UAC Control Panel, and setting the slider to disabled. Because Explorer is a trusted executable, the user behind the screen received no warning. Microsoft fixed this issue but an interesting problem upraised from this incident: Windows 7’s default UAC configuration on the admin approval account (the default account created during the install) is not completely secure and it can be bypassed.
Microsoft’s Jon DeVaan has posted a response on the official Windows 7 blog stating that the default behavior for UAC is a result of Microsoft’s “goal to create a useful, usable, and secure Windows for all types of people” and that “one important thing to know is that UAC is not a security boundary. UAC helps people be more secure, but it is not a cure all.”
Conclusion
The only secure way to run Windows 7 is under a standard user account. Under such an account UAC can provide an easy and secure method for elevating to administrator if needed. Under the default account running in admin approval mode, UAC is not as useful. Disabling UAC has the followind undesiereble consequences:
- Protected Mode in Internet Explorer is turned off.
- File and registry virtualization is turned off.
It is recommended that UAC prompting not be turned off by changing the slider setting. Instead, consider configuring UAC to elevate without prompting using Local (or Group) Security Policy.