A new kind of crypto scam has emerged that aims to trick victims into paying fake “service fees” to receive a non-existent Bitcoin payment. Known as the “You Have Received A Bitcoin Transfer” scam, this scheme utilizes spam emails, malicious ads, and social media posts to target potential victims.
If you receive a message stating that someone has sent you Bitcoin, and that you must pay a small fee within 24 hours to “release” the funds, exercise extreme caution. This is likely a scam designed to steal your money. Losses from this con approach have totaled millions of dollars already.
This comprehensive guide will provide an in-depth look at how the “You Have Received A Bitcoin Transfer” scam operates, how to spot fraudulent messages, what to do if you paid any funds, and key strategies to avoid being exploited by these cybercriminals.
Scam Overview
The “You Have Received A Bitcoin Transfer” scam utilizes the increasing popularity and value of cryptocurrencies to trick unwitting users. By claiming that a Bitcoin payment has been initiated to the victim, scammers aim to convince targets to send an “unlock” or “service” fee to secure the imaginary funds.
How the Exploit Starts
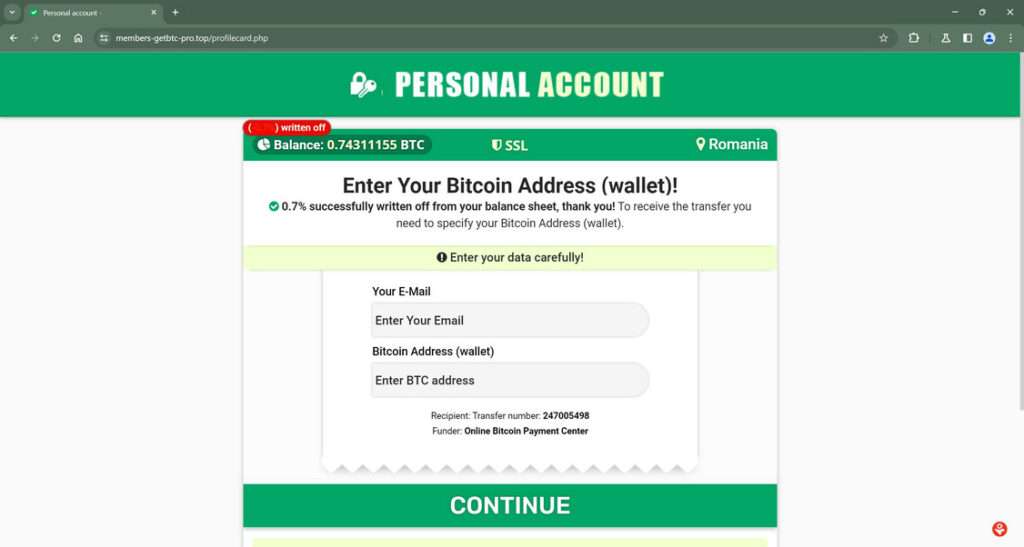
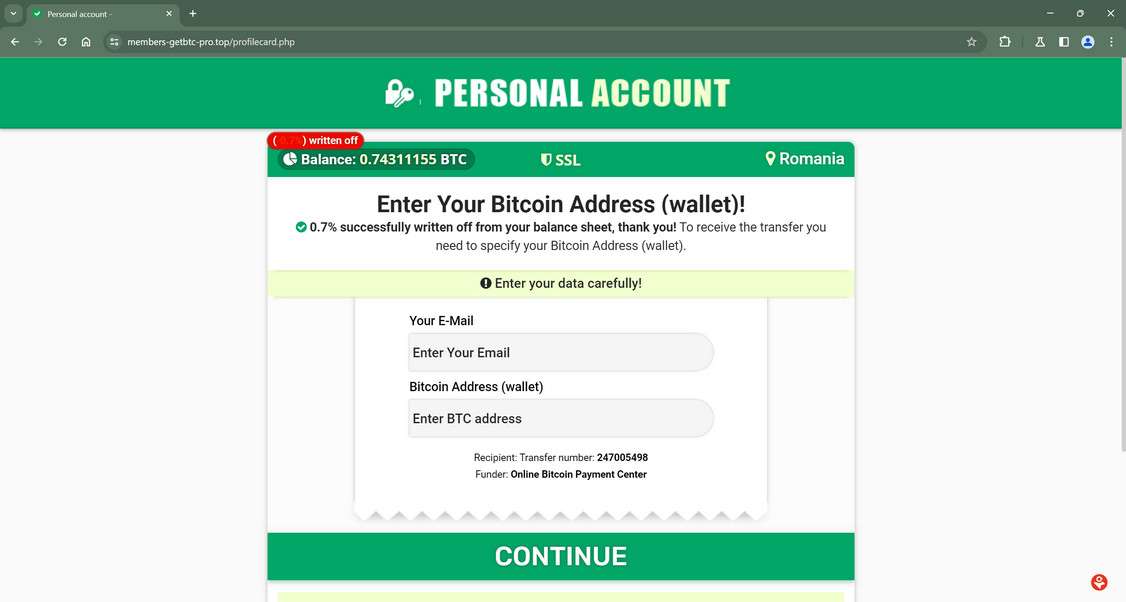
The “You Have Received A Bitcoin Transfer” scam starts by a victim receiving an unsolicited email, social media message, text message, or advertisement stating they were sent Bitcoin. The communication claims that in order to officially receive the cryptocurrency, a small fee must be paid within 24 hours to “finalize” the transfer.
If the fee isn’t paid in time, the message threatens that the Bitcoin will be returned to the sender. This places pressure on the recipient to act quickly before the made-up deadline passes.
Attackers utilize this short time window to create urgency and panic, increasing the likelihood that victims transfer real money without doing additional research.
Deceiving Users With Fake Transfer Details
To deceive recipients that a Bitcoin payment is awaiting them, scam messages contain several convincing details, including:
- A fake Bitcoin wallet address of the “sender”
- An amount of Bitcoin supposedly being transferred (often 0.5 to 1+ BTC)
- Realistic company or service names like “CryptoWallet” or “Blockchain.info”
- Countdown timers or warnings the Bitcoin will expire
- Official logos of legitimate crypto companies
By making the transfer appear authentic, attackers increase the chances victims believe money awaits them by paying the asked fee, which is usually 0.5% to 5% of the total Bitcoin amount shown.
Stealing Funds Through Irreversible Crypto Transactions
Once an interested user contacts the scammer to pay the fee and secure their balance, the criminal provides a destination Bitcoin or cryptocurrency address. Victims are reassured that by sending this payment, the larger Bitcoin balance will immediately appear in the user’s account.
In reality however, after the money is deposited into the imposter’s wallet, all communication ends abruptly. Victims never receive any Bitcoin payments, while the scammers withdraw and launder the funds.
Since cryptocurrency transactions are generally irreversible, once exploited individuals transfer real money to the criminals, their chance of recovering losses plummets. This allows scam artists to quickly take the stolen crypto offline through mixing services or overseas exchanges unidentifiable to authorities or victims.
Spreading the Attack Through Spam and Malvertising
To maximize the reach of this financially-motivated attack, fraudsters rely heavily on two tactics: spam and malvertising campaigns.
Blanketing inboxes globally, spam email allows almost unlimited targeting of potential victims for just pennies per message. By hijacking vulnerable computers, attackers can transmit millions of messages per hour to distribute this scam.
Malvertising utilizes legitimate ad networks and popular websites trusted by users to hide exploitative ads. By embedding malicious code inside banner images or text links, visitors can be redirected to the fraudulent Bitcoin scheme without realizing the destination is harmful, not the real site they intended to visit.
Combining these two ubiquitous online threats allows scam campaigns to scalably target victims everywhere through channels that raise little suspicion when interacting with the content.
How the “You Have Received A Bitcoin Transfer” Scam Actually Works
Now that you understand the overview of this emerging financial fraud, let’s break down the step-by-step process of how cybercriminals leverage this attack against cryptocurrency owners worldwide:
Step 1: Attacker Sends Unverified Communication About Fake Bitcoin Transfer
The first component leveraged by criminals is transmitting an unauthenticated message regarding a non-existent Bitcoin payment sent to the victim. This reaches the target through:
- Spam Emails: Bulk messages often disguised as legitimate notifications from major crypto exchanges, wallet providers, or retailers.
- Social Media Posts / Messages: Promotions about “free Bitcoin programs”, investment opportunities, or contests serve as fronts to harvest contact info and redirect participants off-platform.
- Pop-Up / Banner / Text Advertisements: Malicious ads purchased through mainstream networks and sites lead users to believable (but fraudulent) transfer notification pages after clicking.
- Text Messages / SMS: Blast texts sent en masse contain urgent calls-to-action guiding recipients to opt-in to release a fake balance.
Regardless of the vector, each scam communication claims the recipient has received Bitcoin from an individual, business, or service and must complete additional verification.
Step 2: Deceptive Sites Guide Victims Through “Release” Process
Once a curious recipient visits the destination URL included, an official-looking website reinforces the Bitcoin payment notification from Step 1. Complete with accurate branding, transaction data, sender wallet addresses, and countdown timers, sites apply maximum social engineering to achieve two goals:
- Build Trust: By reflecting a financial platform users expect, sites aim to validate the communication’s legitimacy and remove doubt.
- Create Urgency: Short timers, warnings of expiring funds, and constant reminders to “Unlock My Bitcoin” prompt hurried actions over rational deliberation.
Both principles increase the likelihood visitors believe money awaits them and must act quickly, dismissing safer verification suggestions displayed.
Step 3: Scammers Collect “Service” Payments From Targets
After convincing visitors of an available Bitcoin balance, fraudsters offer an ultimatum – either send a small processing or network fee immediately to receive the full amount, or miss the 24 hour deadline and lose access permanently.
This monetary value demanded ranges from 0.5% to 20% of the fake transfer total, with an average around 5% currently. So for an advertised 1 Bitcoin (worth ~$17,000 presently), targets would pay ~$850 to finalize the imaginary transaction.
To reassure victims, official instructions provided detail paying these “Unlock My Bitcoin” charges:
- Bitcoin Wallet Address: Where funds should be deposited to cover service fees
- QR Code: Scan to automatically populate payment details
- Currency Type: Bitcoin preferred but other major cryptocurrencies accepted
Once submitted, scammers receive near real-time notifications allowing them to withdraw deposits rapidly before accounts are flagged or taken offline.
Step 4: Criminals Disappear After Collecting Victim Funds
Upon receiving service payments from one or more victims, attackers abandon all communication channels with no intention of paying out Bitcoin transfers advertised.
Website domains hosting fraudulent transfer pages quickly disappear, emails bounce, phone numbers switch off, and social media accounts making initial contact all deactivate.
With no traces left online and cryptocurrency transactions near impossible to reverse, victims seldom have any recourse available to pursue refunds or aid tracking the criminals. This allows scam artists to net six and seven-figure hauls from this scheme regularly.
What To Do If You Paid Money To These Scammers Already
If you transferred any money to fraudsters already, don’t panic. Though extremely difficult, taking quick action provides the only chance of reclaiming lost funds:
Step 1: Contact The Crypto Platforms Involved Immediately
Most reputable cryptocurrency exchanges and wallets monitor transactions for suspicious indicators. By reporting fraudulent payments rapidly, staff can potentially stop withdrawals in time and freeze associated accounts.
Prepare previous order IDs, destination wallet addresses, and transaction hashes to help investigators locate and trace stolen funds.
Step 2: Check WhoIs Data And Hosting Providers
Websites soliciting payments often utilize privacy protections to mask owners. However there still may be identifiable information within page sources, DNS registration records, or web hosting companies used giving clues.
Uncover and preserve this data for authorities to subpoena later when building cases. It can prove pivotal in linking multiple scam sites to the same criminal groups.
Step 3: Gather All Details From Initial Contact Point
Messages, emails, ads, posts, or texts first mentioning the Bitcoin transfer likely have digital footprints. harvesting key information now aids tracking the scam’s origin later:
- Email headers showing relay paths
- Linked social media accounts
- WhoIs registration data if a text link was used
- Ad network or publisher details for malvertisements
Preserve message copies and any metadata available no matter how inconsequential. Investigators piece together cases from tiny clues.
Step 4: Contact Law Enforcement And File Reports
Local police departments, state agencies, federal bureaus, and international groups all handle cryptocurrency fraud claims. Reporting losses through official channels aids getting cases assigned to agents who specialize in blockchain exploits needed.
Filing complaints also builds important statistics revealing growing threats like this Bitcoin transfer scam. Documenting every instance makes securing future policy changes and enforcement resources easier over time.
By contacting officials rapidly with well-organized documentation, victims enable the best possibility of asset recovery, investigation progress, and capturing attackers down the road.
Frequently Asked Questions About the “You Have Received a Bitcoin Transfer” Scam
This dangerous financial fraud is exploiting popularity of cryptocurrencies using deception about payments. Protect yourself by learning the answers to these common questions.
What Exactly Is The You Have Received a Bitcoin Transfer Scam?
Cybercriminals are sending phishing messages claiming recipients have an incoming Bitcoin transaction from an individual or business that must be “released” by paying a small processing fee. This is completely fraudulent with all money sent stolen by scammers rather than used to receive any BTC.
How Does the Attack Work to Steal Money?
- Victims receive spam emails, texts, fake ads, or social media messages about a Bitcoin payment receipt.
- Deceptive websites victims visit reinforce legitimacy of the transfer and provide Bitcoin wallet addresses to pay release fees.
- Users send crypto funds hoping to unlock larger imagined balances which never materialize once criminals receive the money.
What Methods Do Scammers Use to Target Victims?
This financially motivated fraud spreads through unsolicited:
- Emails masked as official notifications from cryptocurrency companies
- Social media investment promotions and contests
- Malvertising using legitimate advertising networks to hide scam redirects
- SMS and text blasts using urgency to convince recipients to click included links
How Much Money Could I Lose From This?
Demanded release fees average 0.5% to 5% of the fake pending Bitcoin transaction amount displayed. So for a promised transfer of 1 BTC (worth ~$17,000 currently), targets might pay .05 BTC (~$850) and never receive anything.
What Should I Do if I Already Paid Them?
Contact involved cryptocurrency companies and law enforcement immediately. Gather all details around the initial messages, sender addresses used, and where you sent money. This aids tracking stolen funds and identifying attackers. Expect very low chances of recovery however.
How Can I Avoid Falling Victim to This Con?
Delete messages regarding incoming crypto transfers you didn’t request. Legitimate networks never demand payment from the receiver to release funds. Report scam emails, texts, and social media accounts. Stick to well-known, trusted sources when managing digital assets.
This Bitcoin balance release scam combines plausibility and urgency to effectively exploit cryptocurrency owners. Verify the legitimacy of any notifications about incoming assets before providing personal information or payments. Actively protecting yourself using safe practices remains the only guaranteed defense.
The Bottom Line – Protecting Yourself From This Scam
This Bitcoin delivery notification scam combines urgency, plausibility, and value to effectively target cryptocurrency traders and holders. Losses already exceed tens of millions.
Everyone must exercise added caution when unverified messages arrive mentioning crypto payments. If communications insist funds expire unless you pay a release fee – cease engagement immediately.
Legitimate networks never demand payment to receive transfers sent to your wallet address. These are criminal groups stealing hard-earned money who vanish indefinitely after getting paid.
There are no shortcuts to safely accelerating wealth through cryptocurrencies. If an investment seems too good to be true, it nearly always is. Stick to well-known, trusted sources when managing digital assets to avoid this and other common crypto scams.
Hopefully this guide better prepared you to identify fraudulent Bitcoin payment schemes and educated on safer practices protecting your cryptocurrency investments from theft.

![Remove Bojel.com Pop-up Ads [Virus Removal Guide] 6 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)