Apple devices like iPhones, iPads, and Macbooks are extremely popular around the world. With so many users, scammers have taken notice and begun targeting Apple customers with phishing scams aimed at stealing personal information and account credentials. One such scam is the “Your Apple ID Has Been Locked” phishing email.
This fraudulent email claims your Apple ID has been locked for security reasons to trick you into providing sensitive information. If you receive an unsolicited email like this, it’s best to ignore it completely. However, it’s important to understand how this scam works so you can protect yourself.
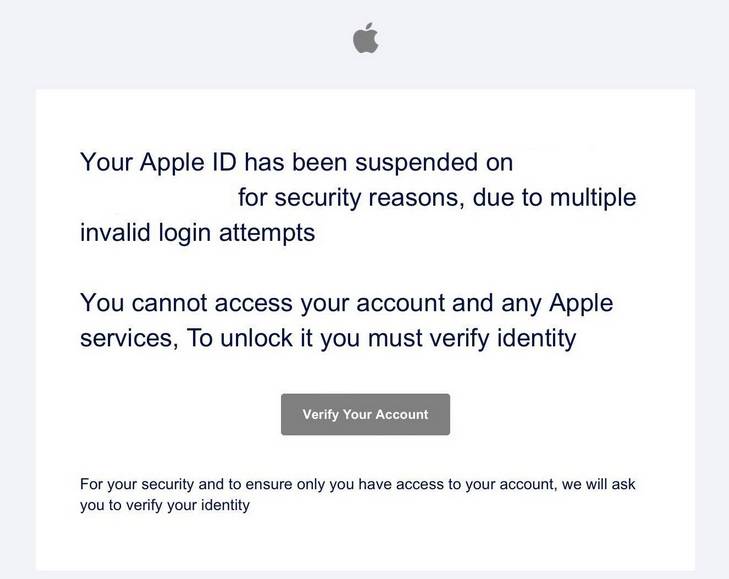
Overview of the Your Apple ID Has Been Locked Scam
The “Your Apple ID Has Been Locked” phishing scam uses fake emails pretending to be from Apple Support. The email claims your Apple ID has been locked due to “multiple invalid login attempts” as a security precaution.
It goes on to say you cannot access any Apple services or your account until you verify your identity. There is usually a link provided to a fraudulent Apple site asking you to enter your username and password to unlock your account.
In reality, this is a scam to steal login credentials and other personal information. Apple would never send an unsolicited email asking users to verify their identity in this manner. Any communication from Apple regarding account security would take place within the official Apple ID management system, not via an email link.
This phishing attack targets Apple users by exploiting fear around account security. The email is designed to convince recipients to click the link and provide sensitive information urgently before their access is taken away. If entered on the fake site, login credentials and personal information are stolen by scammers.
Some red flags that indicate the “Your Apple ID is Locked” email is a scam:
- Apple would never notify you of account locking via an unsolicited email. Official communications take place within your Apple ID account.
- Poor grammar, spelling mistakes, and unfamiliar sender addresses indicate the email is not legitimate.
- Requests to verify identity should always be treated cautiously, especially if not initiated by you.
- Links within unsolicited emails often lead to fake, fraudulent sites used to steal information.
By understanding common phishing techniques used in the “Your Apple ID is Locked” scam, you can identify and avoid this attack to keep your information safe. Scrutinize any unsolicited emails and do not provide personal data unless you have initiated the process through official Apple channels.
How the Your Apple ID Has Been Locked Scam Works
Scammers use clever psychological tricks and technical methods to carry out the “Your Apple ID Has Been Locked” phishing attack. Understanding the scam process illustrates why it can seem convincing and how to stay secure.
Crafting a Deceptive Email
The first step is creating an email that convinces recipients their Apple account is at risk. Scammers design the message to create urgency and fear over account security to prompt action.
The subject line is designed to get your attention, usually stating “Your Apple ID Has Been Locked” or something similar about account security. The sender email often spoofs an Apple Support address to appear legitimate.
The content explains your account has been “locked for security reasons” after “invalid login attempts”, a worrying prospect for any Apple user. A link is provided to quickly “verify your identity” and unlock access, directing you to the phishing site.
These tactics pressure recipients to click the link and secure their account without considering the validity of the unfamiliar email source. However, any legitimate account security alerts would come from within Apple’s official systems, not unverified emails.
Directing Victims to Fraudulent Sites
The link within the email directs users to a fake site impersonating Apple’s ID management portal. The site is designed to mimic Apple’s branding and login experience to seem credible.
Once on the site, you are prompted to enter your Apple ID email/username and password to “unlock your account”. In reality, this harvesting your Apple login credentials for malicious use.
The site may even replicate account recovery and identity verification flows, gathering more personal information that can be used to access your accounts. All data entered is captured by scammers rather than reaching official Apple systems.
Stealing Login Credentials and Personal Data
Once scam victims enter their Apple ID password and other information on the phishing site, this sensitive data is stolen by scammers. They now possess your username and password for accessing your account.
With your credentials, scammers can now login to your real Apple account, accessing personal information, files, photographs, financial details, and more. This lets them steal data, commit identity fraud, make purchases, and potentially access linked accounts like iCloud or iTunes.
Beyond just your password, any personal information submitted to the phishing site can be used for identity theft and account recovery by scammers. Details like addresses, dates of birth, phone numbers, and security questions should always be guarded.
Using Stolen Data for Further Attacks
Once scammers have your Apple ID login credentials and other personal information, this data can be used to carry out further attacks beyond just compromising your Apple account.
Your email address and password may be tried against other popular sites and services you may use to access more accounts. Additional personal details can also help scammers impersonate you and recover accounts through password reset procedures.
Furthermore, they may be sold on to other malicious groups or individuals enabling wide-scale identity fraud and cybercrime far beyond the original phishing scam. Your data could fuel many future attacks.
By understanding each step in the phishing process, you can see how vital it is to avoid clicking unsolicited links and providing any information to suspicious sites. Identifying the scam early prevents an expanding chain of account breaches, data theft and extensive identity fraud.
What to Do If You Have Fallen Victim to the Scam
If you suspect you have been compromised by the “Your Apple ID Has Been Locked” or any similar phishing scam, urgent action is required to secure your accounts and protect your data from further misuse. Here are the steps to take:
Step 1: Change your Apple ID Password
If you entered your Apple password into a phishing site, the first step is to change it immediately so scammers can no longer access your account.
Log in directly to Apple’s password reset page at https://iforgot.apple.com and select ‘Reset your password’. This will guide you through creating a new, strong password for your Apple ID that has not been compromised. Enable two-factor authentication as well for increased security on your account.
Step 2: Review Recently Accessed Devices
Check your account security settings for any unauthorized or unfamiliar device access. Scammers may be attempting to use stolen credentials to login to your Apple ID from their own device.
Revoking access and signing out all sessions can stop this misuse. You can do this under the security settings when logged into your Apple account.
Step 3: Monitor Account Activity
Carefully check your entire Apple account for any signs of unauthorized access, data theft or malicious activity enabled through stolen credentials.
Review account details, files, stored data, contacts, and photographs for anything unfamiliar which may indicate fraudulent access. Check Apple transaction histories for any unauthorized purchases made.
Step 4: Contact Apple Support
Notify Apple Support that your account credentials have been compromised through phishing so they can secure your account. Apple can perform further reset procedures and apply enhanced security measures when informed of a successful phishing attack.
Call Apple or speak to an advisor online and explain you need to secure your account due to stolen credentials. They can walk through all the steps needed to fully protect and restore your account security.
Step 5: Reset Linked Accounts
If your Apple ID is linked to any other accounts like iCloud, iTunes, or financial services, change the passwords for these accounts immediately as well. Stolen Apple credentials could give scammers access to any linked accounts too.
Review all linked accounts thoroughly for any signs of unauthorized access. Disable connections to your Apple ID if any evidence of breach is found until security is restored.
Step 6: Be Wary of Any Further Scams
Once victim to phishing, scammers may target you with more attacks sensing you are vulnerable. Be wary of unsolicited contacts requesting personal information or account access to avoid repeated fraud. Never provide information unless you have independently verified the source.
Step 7: Monitor Your Identity & Accounts
Check your credit reports and accounts closely over the upcoming months for any unusual activity that may indicate identity fraud. Scammers may use stolen personal information for financial crimes. Immediately report any unauthorized access to your financial accounts or signs of identity theft.
Reacting quickly to reverse the damage from phishing scams is essential to secure your Apple account and wider personal data. Reset account access, monitor for misuse, and contact Apple to implement increased account security.
“Your Apple ID Has Been Locked” Scam Frequently Asked Questions
How do I know if an email saying my Apple ID is locked is a scam?
Apple will never contact you via an unsolicited email regarding account security issues. Any genuine notifications happen securely within your Apple ID account portal. Emails stating your account is locked are always scams.
What should I do if I clicked the link in the scam email?
If you entered any information on the site, change your Apple password immediately and review account activity for any unauthorized changes. Contact Apple Support to secure your account and monitor closely for signs of identity theft.
Can scammers really access my account with just my password?
Yes, your Apple ID password provides full access to your account and any linked services. Scammers can view personal data, access files, make purchases, and potentially access other linked accounts.
What if I also entered personal information like my address on the phishing site?
Provide this information to Apple when contacting them to highlight the extent of compromised data. Monitor your credit reports and accounts closely for signs of identity fraud using stolen personal information.
Are there any genuine reasons Apple would lock my account?
Apple may lock accounts temporarily if suspicious activity is detected like an unusual login location. However, you would receive notifications within your Apple ID account – never via external email. Legitimate security measures will still allow you to access key account functions.
How can I improve my account security after a phishing attack?
Always use a unique, complex password. Enable two-factor authentication and review linked devices/accounts. Be cautious of further scams and never provide info unless you have verified the source directly with Apple.
Who can I contact for help securing my account?
Contact Apple Support right away for assistance securing your account and assessing potential fraudulent activity enabled through stolen credentials. They can provide the right support to restore account security and minimize damage from phishing scams.
Conclusion
The “Your Apple ID Has Been Locked” phishing scam is a cleverly designed attack that exploits fear of account security to steal credentials and personal information from Apple users. Understanding how it works provides the knowledge to identify and avoid this scam.
Scrutinize the source of any email regarding account access issues rather than blindly clicking links and providing information urgently. Any legitimate security alerts from Apple will take place securely within official Apple systems, not via unsolicited emails.
If you have fallen victim and provided information to a phishing site, take action immediately to change account passwords, revoke unauthorized access, monitor for misuse, and contact Apple Support. With fast action, you can limit the damage and prevent your stolen information facilitating further fraud.
Stay vigilant against phishing attacks targeting your accounts and use unique, complex passwords for all services. Never provide personal information unless you have independently verified the source. Taking a cautious approach is key to protecting your data and identity online.



