- Aug 17, 2014
- 11,777
A seven-year-old privilege escalation vulnerability discovered in the polkit system service could be exploited by a malicious unprivileged local attacker to bypass authorization and escalate permissions to the root user.
Tracked as CVE-2021-3560 (CVSS score: 7.8), the flaw affects polkit versions between 0.113 and 0.118 and was discovered by GitHub security researcher Kevin Backhouse, who said the issue was introduced in a code commit made on Nov. 9, 2013. Red Hat's Cedric Buissart noted that Debian-based distributions, based on polkit 0.105, are also vulnerable.
Polkit (née PolicyKit) is a toolkit for defining and handling authorizations in Linux distributions, and is used for allowing unprivileged processes to communicate with privileged processes.
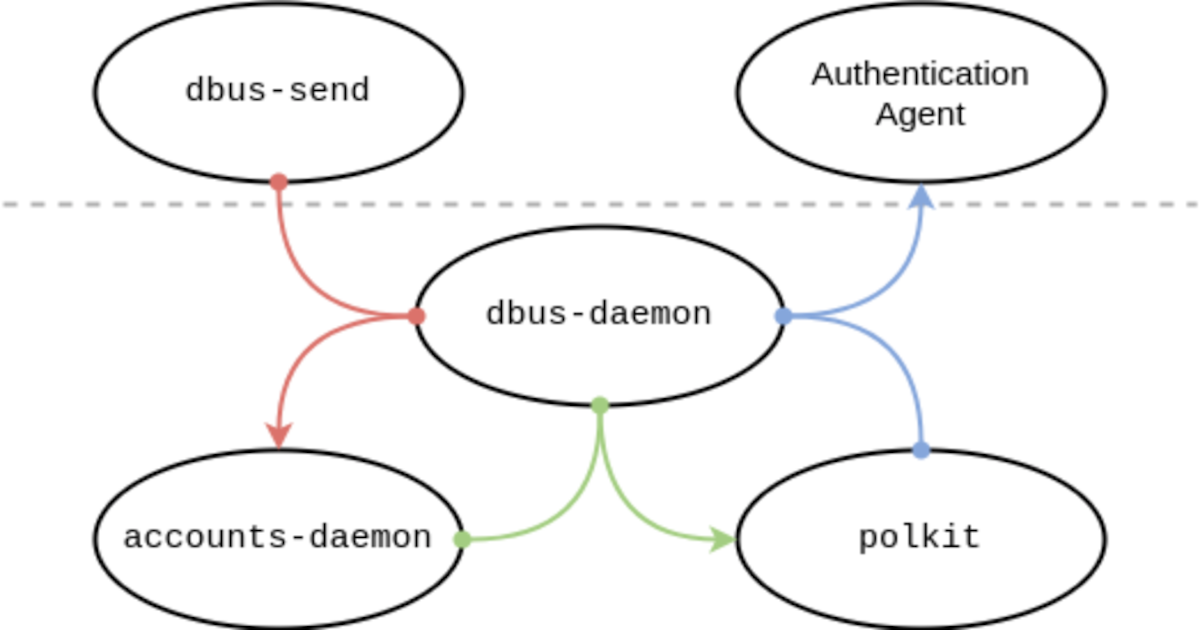
"When a requesting process disconnects from dbus-daemon just before the call to polkit_system_bus_name_get_creds_sync starts, the process cannot get a unique uid and pid of the process and it cannot verify the privileges of the requesting process," Red Hat said in an advisory. "The highest threat from this vulnerability is to data confidentiality and integrity as well as system availability."

7-Year-Old Polkit Flaw Lets Unprivileged Linux Users Gain Root Access
A newly uncovered 7-Year-Old Polkit vulnerability (CVE-2021-3560) could let unprivileged Linux users gain root-level access on targeted systems.
 thehackernews.com
thehackernews.com