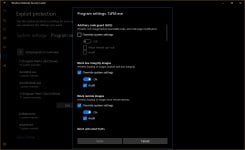
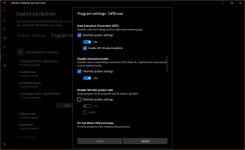
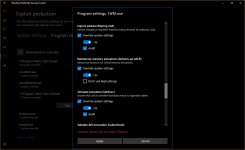
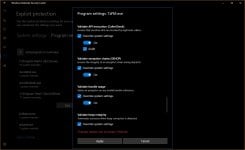
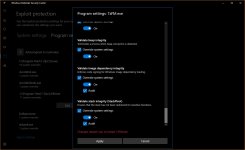
Three mitigations did not work for me: Arbitrary code guard (ACG), Code integrity guard, Disable Win32k system calls.
.
You can allow 7zFM.exe and 7zG.exe:
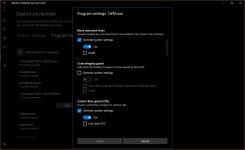
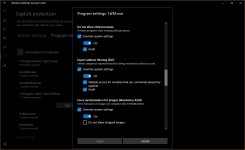
Block low integrity images, Block remote images, Block untrusted fonts, Control flow guard (CFG but not strict CFG), Data Execution Prevention + ATL (DEP), Disable extension points, Do not allow child processes (but then no execution from archive), Export address filtering (EAF), Import address filtering (IAF), Force randomization for images (Mandatory ASLR), Force randomization for images (Mandatory ASLR, do not tick the checkbox below), Randomize memory allocations (Bottom-Up ASLR with high entropy, do not tick the checkbox below in 64-bit Windows), Simulate execution (SimExec), Validate API invocation (CallerCheck), Validate exception chains (SEHOP), Validate handle usage, Validate heap integrity, Validate image dependency integrity, Validate stack integrity (StackPivot).
.
That was a quick test - if something will cause problems then let me know.

.
Edit1
The above mitigations work well in Explorer right-click context menu for 7-zip options, when opening archiwe to view the file list (but not file content), creating archive, adding new files, delete files from it, or decompressing it. If someone wants to do more (viewing the contents of files, viewing/editing the contents of files, running files) then the mitigation 'Do not allow child processes' should be set to OFF.
.
Edit2
If someone uses external File Manager (for example Total Commander) then it will not probably use 7zFM.exe to open archives but 7zG.exe or one of 7-Zip DLLs (7zip.dll, 7-zip.dll or 7-zip32.dll).