- Oct 23, 2012
- 12,527
The Krebs DDoS attacks have proven that the IoT landscape is a fertile ground that can breed huge botnets capable of launching massive DDoS assaults. As such, it should be to no surprise that malware authors are now focusing their efforts on this sector and putting out new threats in the hopes of building the next Mirai botnet.
One of the latest additions to the IoT malware market is a trojan codenamed Linux/NyaDrop, recently reverse engineered by MalwareMustDie, the same researcher that discovered the Mirai malware.
NyaDrop dropped via brute-force attacks on Telnet ports
MalwareMustDie points out in his research that this binary appeared in May, but was somewhat simplistic and not that common. Things changed after the Krebs DDoS attacks, and a new sample has appeared on the market, with the malware's author most likely drawn back to the IoT landscape by Mirai's success.
Just like most IoT malware nowadays, NyaDrop's author relies on brute-forcing Internet-exposed IoT devices using their default credentials.
In a conversation on Twitter, MalwareMustDie tells Softpedia that the attacks happen on the devices' Telnet ports, which is a common practice in IoT attacks.
One of the latest additions to the IoT malware market is a trojan codenamed Linux/NyaDrop, recently reverse engineered by MalwareMustDie, the same researcher that discovered the Mirai malware.
NyaDrop dropped via brute-force attacks on Telnet ports
MalwareMustDie points out in his research that this binary appeared in May, but was somewhat simplistic and not that common. Things changed after the Krebs DDoS attacks, and a new sample has appeared on the market, with the malware's author most likely drawn back to the IoT landscape by Mirai's success.
Just like most IoT malware nowadays, NyaDrop's author relies on brute-forcing Internet-exposed IoT devices using their default credentials.
In a conversation on Twitter, MalwareMustDie tells Softpedia that the attacks happen on the devices' Telnet ports, which is a common practice in IoT attacks.
NyaDrop is just a dropper for the Nya malware
If the brute-force attacker manages to authenticate on the device, a script executes a series of automated commands that download and execute the NyaDrop binary.
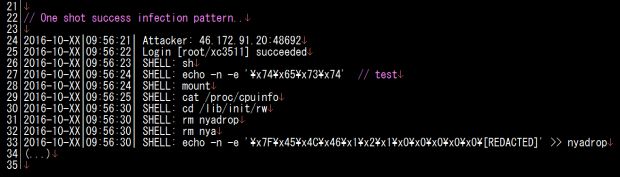
Successful brute-force attack login which ends with attacker dropping NyaDrop
The NyaDrop trojan is very small in size. This is because the malware is just a "dropper," a term used to describe malware that downloads other more potent malware.
Employing droppers to download the final payload is a common practice for desktop malware and hasn't been seen deployed regularly with IoT malware.
NyaDrop's purpose is to probe the system and see if to download the actual malware, which is an ELF (Linux-specific) binary called "nya," hence the malware's name of NyaDrop.
NyaDrop only targets MIPS architectures
MalwareMustDie says that NyaDrop will open a backdoor on the infected device and download the Nya trojan if the IoT device uses a MIPS 32-bit architecture for its CPU.
MIPS-based CPUs are often found within devices such as routers, DVRs, CCTV cameras, and other embedded systems.
The reason for the MIPS check is most likely that the NyaDrop author hasn't created fully functional payloads for other IoT platforms and wants to avoid infecting "useless" platforms, wasting bandwidth, and leaving strange binaries on systems it can't use.
But the problem here is the dropper-payload scheme. By using this modular approach, future versions can be used for all sorts of things. The NyaDrop author can decide to push new payloads to NyaDrop-infected devices, which can have different capabilities, from the ability to launch DDoS attacks to working as proxies for all sorts of web traffic, masking an attacker's location.
NyaDrop author very careful not to get caught
"This one [NyaDrop] was also made by Russian actor," MalwareMustDie told Softpedia after analyzing the malware. He also says that NyaDrop is capable of detecting honeypot environments, in which case it stops execution.
MalwareMustDie says the crook has been very careful not to spread his malware around. "It is very hard to get this sample," MalwareMustDie said. "Lucky..very lucky to finally know the [NyaDrop] scheme."
It is through the work of researchers such as MalwareMustDie, Benkow, Dr.Web, and others that we know of malware like Rex, PNScan, Mirai, LuaBot, and Linux.BackDoor.Irc, and Linux.DDoS.93.
While Mirai got all the fame due to the public way it was used against a high-profile journalist, the other malware variants are just as dangerous and in the hands of a skilled and determined actor can cause just as much damage.
