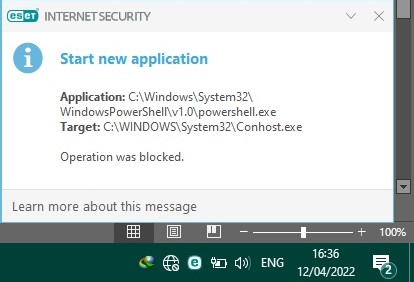
Could anyone shed a light about the meaning of this notification? Does this indicate a harmful action? I have never seen such before
Advice Request A strange notification from Eset IS
- Thread starter restwrst
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
- May 26, 2014
- 1,378
- 9,319
- 2,288
Are you using custom HIPS settings? What you changed from default settings?
That’s what I wonder too. But if you were not expecting it, having PowerShell randomly spawn in the background would make me feel very paranoid too. Might be worth running a second opinion scanner.Are you using custom HIPS settings? What you changed from default settings?
- May 26, 2014
- 1,378
- 9,319
- 2,288
That’s what I wonder too. But if you were not expecting it, having PowerShell randomly spawn in the background would make me feel very paranoid too. Might be worth running a second opinion scanner.
Contrary to popular opinion I dont think that it is a good ideia to tweak ESET settings, default is totally fine, unless the user really knows what he is doing and has a reason to.
I had this happen every half hour once when running ESET. From what I could tell it was a printer driver update stuck in a loop from being blocked. Just in case I reimaged and it didn’t reoccur. Never figured it out for sure. But the peace of mind of the reimage was better.That’s what I wonder too. But if you were not expecting it, having PowerShell randomly spawn in the background would make me feel very paranoid too. Might be worth running a second opinion scanner.
Yes. I use custom HIPS. I imported it from someone's because I did not know how to tweak it manually. This problem started to come up just a couple days ago. Any recommendation to fix this problem other than reinstalling windows?Are you using custom HIPS settings? What you changed from default settings?
Oh interesting. Yes I suppose it could be a legitimate installation script as well. But this is why I am also, as @Nightwalker alluded to, opposed to tightening HIPS settings by hand with ESET. This is basically inventing your own first-generation behavior blocker, except all the mature behavior blocker products have literally years of experience whitelisting specific exceptions. ESET HIPS is a powerful tool for enterprises or hardening servers that have very static workflows, but I don't think most of us want to sign up to invent our own antivirus add-on!I had this happen every half hour once when running ESET. From what I could tell it was a printer driver update stuck in a loop from being blocked. Just in case I reimaged and it didn’t reoccur. Never figured it out for sure. But the peace of mind of the reimage was better.
Agreed. The only hand entered HIPS rules I did amounted to basically recreating controlled folder access and blocking child processes from Office apps.Oh interesting. Yes I suppose it could be a legitimate installation script as well. But this is why I am also, as @Nightwalker alluded to, opposed to tightening HIPS settings by hand with ESET. This is basically inventing your own first-generation behavior blocker, except all the mature behavior blocker products have literally years of experience whitelisting specific exceptions. ESET HIPS is a powerful tool for enterprises or hardening servers that have very static workflows, but I don't think most of us want to sign up to invent our own antivirus add-on!
F
ForgottenSeer 94654
No. It does not. In Windows there are a number of tasks that run that use powershell, which in turn executes conhost. None of these powershell tasks are needed one bit by the typical Windows operating system. For example, powershell will occasionally run a check to verify if Applocker policy is enabled on the system. This powershell check only has relevance to systems that are part of a domain\Azure Active Directory with Applocker policy pushed by either InTune or Microsoft Endpoint Manager.Could anyone shed a light about the meaning of this notification? Does this indicate a harmful action? I have never seen such before
View attachment 265802
You can compare the time stamp of the above block event in the ESET log with the time stamp in the Windows (System) Event Log to see why powershell is launching (what is triggering the block).
Your HIPS rule for powershell is messed up. Powershell should not be permitted to launch at all (whereas it being allowed to launch the child process conhost launching is much less of a concern).
Thanks for the advice. I think I'm going to set my HIPS to default. I'm not a happy clicker. At least I know what I do.No. It does not. In Windows there are a number of tasks that run that use powershell, which in turn executes conhost. None of these powershell tasks are needed one bit by the typical Windows operating system. For example, powershell will occasionally run a check to verify if Applocker policy is enabled on the system. This powershell check only has relevance to systems that are part of a domain\Azure Active Directory with Applocker policy pushed by either InTune or Microsoft Endpoint Manager.
You can compare the time stamp of the above block event in the ESET log with the time stamp in the Windows (System) Event Log to see why powershell is launching (what is triggering the block).
Your HIPS rule for powershell is messed up. Powershell should not be permitted to launch at all (whereas it being allowed to launch the child process conhost launching is much less of a concern).
- May 26, 2014
- 1,378
- 9,319
- 2,288
Yes. I use custom HIPS. I imported it from someone's because I did not know how to tweak it manually. This problem started to come up just a couple days ago. Any recommendation to fix this problem other than reinstalling windows?
That's what I thought, try to reset the settings for default values or better yet, reinstall ESET and don't import someone else settings, default is fine.
You may also like...
-
-
update-macos spam notifications.
- Started by bazhowland
- Replies: 2
-
Security News EU looking ‘very seriously’ at taking action against X over Grok
- Started by Brownie2019
- Replies: 2
-
Advice Request HELP! My device is locked by ESET Mobile Security
- Started by restwrst
- Replies: 20
-
