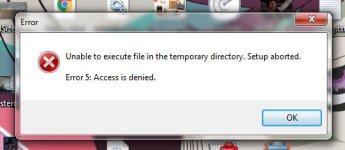
December 28 2016, accidentally installed from a lightsaber page that had a missing font. I was tired, and it seemed legit until it forcefully restarted the computer while browsing and I have not been able to install just about anything.
Accidentally installed Chrome_Font.exe and cant install most removal programs like Malwarebytes, etc
- Thread starter AnakinSkywalker
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Anything you guys can do to help would be amazing. I have been attempting various things and have tried to install windows 10 at a friend's suggestion. It won't let anything install because it seems the temp directory is inaccessible.
Hello,
 Fix with Farbar Recovery Scan Tool
Fix with Farbar Recovery Scan Tool
 This fix was created for this user for use on that particular machine.
This fix was created for this user for use on that particular machine.

 Running it on another one may cause damage and render the system unstable.
Running it on another one may cause damage and render the system unstable.

Download attached fixlist.txt file and save it to the Desktop:
Both files, FRST and fixlist.txt have to be in the same location or the fix will not work!
Please attach it to your reply.

Download attached fixlist.txt file and save it to the Desktop:
Both files, FRST and fixlist.txt have to be in the same location or the fix will not work!
- Right-click on icon and select
 Run as Administrator to start the tool.
Run as Administrator to start the tool.
(XP users click run after receipt of Windows Security Warning - Open File). - Press the Fix button just once and wait.
- If for some reason the tool needs a restart, please make sure you let the system restart normally. After that let the tool complete its run.
- When finishes FRST will generate a log on the Desktop, called Fixlog.txt.
Please attach it to your reply.
Attachments
How is your PC behaving now?
It's pretty much the same. I can't install malwarebytes or any updates to other programs. It gives me that error still. My computer is mostly usable to browse the web and stuff but it seems like some of the system files got overwritten and won't let me install anything that will help get rid of this thing. I know this might be a big pain, and I really appreciate your help. I get paid tomorrow and I can definitely PayPal you for some beers of we can get this solved.
Attachments

Please re-run Farbar Recovery Scan Tool to give me a fresh look at your system.
- Right-click on icon and select
 Run as Administrator to start the tool.
Run as Administrator to start the tool.
(XP users click run after receipt of Windows Security Warning - Open File). - Make sure that Addition.txt option is checked.

- Press Scan button and wait.
- The tool will produce two logfiles on your desktop: FRST.txt and Addition.txt.
Check Disk
Please download Zemana AntiMalware and save it to your Desktop.
- Press the on your keyboard. Type cmd and right click >> Run as Administrator.

- Copy/Enter the command below and press Enter:
-
Code:
chkdsk C: /r - You should get a message to schedule Check Disk at next system restart. Please type Y and press Enter.
- All you should do now is to restart your PC and let the Check Disk process finish uninterrupted.
- Press the + R on your keyboard at the same time. Type eventvwr and click OK.

- In the left panel, expand Windows Logs and then click on Application.
- Now, on the right side, click on Filter Current Log.
- Under Event Sources, check only Wininit and click OK.
- Now you'll be presented with one or multiple Wininit logs.
- Click on an entry corresponding to the date and time of the disk check.
- On the top main menu, click Action > Copy > Copy Details as Text.
- Paste the contents into your next reply.
Please download Zemana AntiMalware and save it to your Desktop.
- Install the program and once the installation is complete it will start automatically.
- Without changing any options, press Scan to begin.
- After the short scan is finished, if threats are detected press Next to remove them.
Note: If restart is required to finish the cleaning process, you should click Reboot. If reboot isn't required, please restart your computer manually.
- Open Zemana AntiMalware again.
- Click on icon and double click the latest report.

- Now click File > Save As and choose your Desktop before pressing Save.
- The only left thing is to attach saved report in your next message.
Log Name: Application
Source: Microsoft-Windows-Wininit
Date: 1/27/2017 2:58:24 PM
Event ID: 1001
Task Category: None
Level: Information
Keywords: Classic
User: N/A
Computer: AspireM5800
Description:
Checking file system on C:
The type of the file system is NTFS.
Volume label is BOOT.
A disk check has been scheduled.
Windows will now check the disk.
CHKDSK is verifying files (stage 1 of 5)...
Cleaning up instance tags for file 0x2d62c.
Cleaning up instance tags for file 0x69407.
451328 file records processed.
File verification completed.
14139 large file records processed.
0 bad file records processed.
2 EA records processed.
47 reparse records processed.
CHKDSK is verifying indexes (stage 2 of 5)...
611556 index entries processed.
Index verification completed.
0 unindexed files scanned.
0 unindexed files recovered.
CHKDSK is verifying security descriptors (stage 3 of 5)...
451328 file SDs/SIDs processed.
Cleaning up 1989 unused index entries from index $SII of file 0x9.
Cleaning up 1989 unused index entries from index $SDH of file 0x9.
Cleaning up 1989 unused security descriptors.
Security descriptor verification completed.
80115 data files processed.
CHKDSK is verifying Usn Journal...
35393528 USN bytes processed.
Usn Journal verification completed.
CHKDSK is verifying file data (stage 4 of 5)...
451312 files processed.
File data verification completed.
CHKDSK is verifying free space (stage 5 of 5)...
28479721 free clusters processed.
Free space verification is complete.
CHKDSK discovered free space marked as allocated in the volume bitmap.
Windows has made corrections to the file system.
616085503 KB total disk space.
501406808 KB in 299037 files.
185152 KB in 80116 indexes.
0 KB in bad sectors.
574655 KB in use by the system.
65536 KB occupied by the log file.
113918888 KB available on disk.
4096 bytes in each allocation unit.
154021375 total allocation units on disk.
28479722 allocation units available on disk.
Internal Info:
00 e3 06 00 f1 c4 05 00 4e 2a 0a 00 00 00 00 00 ........N*......
6d 5e 01 00 2f 00 00 00 00 00 00 00 00 00 00 00 m^../...........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Windows has finished checking your disk.
Please wait while your computer restarts.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Wininit" Guid="{206f6dea-d3c5-4d10-bc72-989f03c8b84b}" EventSourceName="Wininit" />
<EventID Qualifiers="16384">1001</EventID>
<Version>0</Version>
<Level>4</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2017-01-27T22:58:24.000000000Z" />
<EventRecordID>40727</EventRecordID>
<Correlation />
<Execution ProcessID="0" ThreadID="0" />
<Channel>Application</Channel>
<Computer>AspireM5800</Computer>
<Security />
</System>
<EventData>
<Data>
Checking file system on C:
The type of the file system is NTFS.
Volume label is BOOT.
A disk check has been scheduled.
Windows will now check the disk.
CHKDSK is verifying files (stage 1 of 5)...
Cleaning up instance tags for file 0x2d62c.
Cleaning up instance tags for file 0x69407.
451328 file records processed.
File verification completed.
14139 large file records processed.
0 bad file records processed.
2 EA records processed.
47 reparse records processed.
CHKDSK is verifying indexes (stage 2 of 5)...
611556 index entries processed.
Index verification completed.
0 unindexed files scanned.
0 unindexed files recovered.
CHKDSK is verifying security descriptors (stage 3 of 5)...
451328 file SDs/SIDs processed.
Cleaning up 1989 unused index entries from index $SII of file 0x9.
Cleaning up 1989 unused index entries from index $SDH of file 0x9.
Cleaning up 1989 unused security descriptors.
Security descriptor verification completed.
80115 data files processed.
CHKDSK is verifying Usn Journal...
35393528 USN bytes processed.
Usn Journal verification completed.
CHKDSK is verifying file data (stage 4 of 5)...
451312 files processed.
File data verification completed.
CHKDSK is verifying free space (stage 5 of 5)...
28479721 free clusters processed.
Free space verification is complete.
CHKDSK discovered free space marked as allocated in the volume bitmap.
Windows has made corrections to the file system.
616085503 KB total disk space.
501406808 KB in 299037 files.
185152 KB in 80116 indexes.
0 KB in bad sectors.
574655 KB in use by the system.
65536 KB occupied by the log file.
113918888 KB available on disk.
4096 bytes in each allocation unit.
154021375 total allocation units on disk.
28479722 allocation units available on disk.
Internal Info:
00 e3 06 00 f1 c4 05 00 4e 2a 0a 00 00 00 00 00 ........N*......
6d 5e 01 00 2f 00 00 00 00 00 00 00 00 00 00 00 m^../...........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Windows has finished checking your disk.
Please wait while your computer restarts.
</Data>
</EventData>
</Event>
I get the same error as above when I try to install Zemana.
Source: Microsoft-Windows-Wininit
Date: 1/27/2017 2:58:24 PM
Event ID: 1001
Task Category: None
Level: Information
Keywords: Classic
User: N/A
Computer: AspireM5800
Description:
Checking file system on C:
The type of the file system is NTFS.
Volume label is BOOT.
A disk check has been scheduled.
Windows will now check the disk.
CHKDSK is verifying files (stage 1 of 5)...
Cleaning up instance tags for file 0x2d62c.
Cleaning up instance tags for file 0x69407.
451328 file records processed.
File verification completed.
14139 large file records processed.
0 bad file records processed.
2 EA records processed.
47 reparse records processed.
CHKDSK is verifying indexes (stage 2 of 5)...
611556 index entries processed.
Index verification completed.
0 unindexed files scanned.
0 unindexed files recovered.
CHKDSK is verifying security descriptors (stage 3 of 5)...
451328 file SDs/SIDs processed.
Cleaning up 1989 unused index entries from index $SII of file 0x9.
Cleaning up 1989 unused index entries from index $SDH of file 0x9.
Cleaning up 1989 unused security descriptors.
Security descriptor verification completed.
80115 data files processed.
CHKDSK is verifying Usn Journal...
35393528 USN bytes processed.
Usn Journal verification completed.
CHKDSK is verifying file data (stage 4 of 5)...
451312 files processed.
File data verification completed.
CHKDSK is verifying free space (stage 5 of 5)...
28479721 free clusters processed.
Free space verification is complete.
CHKDSK discovered free space marked as allocated in the volume bitmap.
Windows has made corrections to the file system.
616085503 KB total disk space.
501406808 KB in 299037 files.
185152 KB in 80116 indexes.
0 KB in bad sectors.
574655 KB in use by the system.
65536 KB occupied by the log file.
113918888 KB available on disk.
4096 bytes in each allocation unit.
154021375 total allocation units on disk.
28479722 allocation units available on disk.
Internal Info:
00 e3 06 00 f1 c4 05 00 4e 2a 0a 00 00 00 00 00 ........N*......
6d 5e 01 00 2f 00 00 00 00 00 00 00 00 00 00 00 m^../...........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Windows has finished checking your disk.
Please wait while your computer restarts.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Wininit" Guid="{206f6dea-d3c5-4d10-bc72-989f03c8b84b}" EventSourceName="Wininit" />
<EventID Qualifiers="16384">1001</EventID>
<Version>0</Version>
<Level>4</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2017-01-27T22:58:24.000000000Z" />
<EventRecordID>40727</EventRecordID>
<Correlation />
<Execution ProcessID="0" ThreadID="0" />
<Channel>Application</Channel>
<Computer>AspireM5800</Computer>
<Security />
</System>
<EventData>
<Data>
Checking file system on C:
The type of the file system is NTFS.
Volume label is BOOT.
A disk check has been scheduled.
Windows will now check the disk.
CHKDSK is verifying files (stage 1 of 5)...
Cleaning up instance tags for file 0x2d62c.
Cleaning up instance tags for file 0x69407.
451328 file records processed.
File verification completed.
14139 large file records processed.
0 bad file records processed.
2 EA records processed.
47 reparse records processed.
CHKDSK is verifying indexes (stage 2 of 5)...
611556 index entries processed.
Index verification completed.
0 unindexed files scanned.
0 unindexed files recovered.
CHKDSK is verifying security descriptors (stage 3 of 5)...
451328 file SDs/SIDs processed.
Cleaning up 1989 unused index entries from index $SII of file 0x9.
Cleaning up 1989 unused index entries from index $SDH of file 0x9.
Cleaning up 1989 unused security descriptors.
Security descriptor verification completed.
80115 data files processed.
CHKDSK is verifying Usn Journal...
35393528 USN bytes processed.
Usn Journal verification completed.
CHKDSK is verifying file data (stage 4 of 5)...
451312 files processed.
File data verification completed.
CHKDSK is verifying free space (stage 5 of 5)...
28479721 free clusters processed.
Free space verification is complete.
CHKDSK discovered free space marked as allocated in the volume bitmap.
Windows has made corrections to the file system.
616085503 KB total disk space.
501406808 KB in 299037 files.
185152 KB in 80116 indexes.
0 KB in bad sectors.
574655 KB in use by the system.
65536 KB occupied by the log file.
113918888 KB available on disk.
4096 bytes in each allocation unit.
154021375 total allocation units on disk.
28479722 allocation units available on disk.
Internal Info:
00 e3 06 00 f1 c4 05 00 4e 2a 0a 00 00 00 00 00 ........N*......
6d 5e 01 00 2f 00 00 00 00 00 00 00 00 00 00 00 m^../...........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Windows has finished checking your disk.
Please wait while your computer restarts.
</Data>
</EventData>
</Event>
I get the same error as above when I try to install Zemana.
From what I can tell as well, the temp folder keeps switching itself back to Read Only every time I change it too.
I am trying everything I can to install Zemana and anything else. I keep trying to change the folder permissions so that it's not read only and it keeps switching to read only, even in safe mode. I suspect this is why I can't install anything, because I can't even write to the temp folder. When I click to install it, nothing happens. If I click several times it eventually says that access is denied to the temp folder, the same error that I posted a screenshot of earlier.
I have no idea why is it happening. I can suggest you to perform a system restore before you got infected.
Last edited:
I fixed it, at least to the point were I can clean the rest of it with other things because I can install again. I used this: Anti-Rootkit BETA - Free Rootkit Scanner & Remover
I attached the log so maybe now you can see what it was and know what to do for the next person.
I attached the log so maybe now you can see what it was and know what to do for the next person.
Attachments
Ah, so it was a Rootkit after all 
Sorry, I haven't seen proper a rootkit infection for years so I didn't realize it could be caused by the rootkit activity based on how you described the problem. Rootkit infections are very very rare today and I am really surprised you got infected by one.
Can you now run Zemana scan?
Sorry, I haven't seen proper a rootkit infection for years so I didn't realize it could be caused by the rootkit activity based on how you described the problem. Rootkit infections are very very rare today and I am really surprised you got infected by one.
Can you now run Zemana scan?
Yeah.... It was most likely because I basically installed it myself. I am bad with virus terminology so I had to do some research based on my symptoms and stumbled upon that version of malwarebytes.
It was a VERY tricky site/infection. I was looking up Star Wars lightsabers and it popped open a page where it looked like the fonts hadn't loaded properly. Then it popped up saying I needed new fonts and to install chrome_font.exe. It looked official. It didn't really do anything after I said it was okay to install then about 10 minutes later my computer rebooted with no warning, closing all my unsaved work. It was at that moment I knew something was wrong but I didn't really notice anything until I tried to use BitTorrent and it had been removed for some reason, then when I tried to re install it deleted every time. I haven't been able to find much about it online and nobody helped me at other places like bleeping computer. It's been rough! Anyway here is the Zemana scan. I included a couple of scans above that had a plethora of issues so who knows how much this thing has done.
Zemana AntiMalware 2.70.2.591 (Installed)
-------------------------------------------------------
Scan Result : Completed
Scan Date : 2017/1/29
Operating System : Windows 7 64-bit
Processor : 4X Intel(R) Core(TM)2 Quad CPU Q9400 @ 2.66GHz
BIOS Mode : Legacy
CUID : 127D5F9F4E1CF1EF5016BB
Scan Type : System Scan
Duration : 30m 48s
Scanned Objects : 219376
Detected Objects : 4
Excluded Objects : 0
Read Level : SCSI
Auto Upload : Enabled
Detect All Extensions : Disabled
Scan Documents : Disabled
Domain Info : WORKGROUP,0,2
Detected Objects
-------------------------------------------------------
Chrome Shortcut
Status : Scanned
Object : --app-id=gbchcmhmhahfdphkhkmpfmihenigjmpp
MD5 : -
Publisher : -
Size : -
Version : -
Detection : Suspicious Browser Setting
Cleaning Action : Repair
Related Objects :
Browser Setting - Chrome Shortcut
Chrome Startup Url
Status : Scanned
Object : Search
MD5 : -
Publisher : -
Size : -
Version : -
Detection : Suspicious Browser Setting
Cleaning Action : Repair
Related Objects :
Browser Setting - Chrome Startup Url
Chrome Startup Url
Status : Scanned
Object : Certified-Toolbar Search
MD5 : -
Publisher : -
Size : -
Version : -
Detection : Suspicious Browser Setting
Cleaning Action : Repair
Related Objects :
Browser Setting - Chrome Startup Url
F.B. Purity For Facebook
Status : Scanned
Object : %localappdata%\google\chrome\user data\profile 1\extensions\ncdlagniojmheiklojdcpdaeepochckl
MD5 : -
Publisher : -
Size : -
Version : -
Detection : PUA.ChromeExt!Gr
Cleaning Action : Repair
Related Objects :
Browser Extension - F.B. Purity For Facebook
Cleaning Result
-------------------------------------------------------
Cleaned : 4
Reported as safe : 0
Failed : 0
It was a VERY tricky site/infection. I was looking up Star Wars lightsabers and it popped open a page where it looked like the fonts hadn't loaded properly. Then it popped up saying I needed new fonts and to install chrome_font.exe. It looked official. It didn't really do anything after I said it was okay to install then about 10 minutes later my computer rebooted with no warning, closing all my unsaved work. It was at that moment I knew something was wrong but I didn't really notice anything until I tried to use BitTorrent and it had been removed for some reason, then when I tried to re install it deleted every time. I haven't been able to find much about it online and nobody helped me at other places like bleeping computer. It's been rough! Anyway here is the Zemana scan. I included a couple of scans above that had a plethora of issues so who knows how much this thing has done.
Zemana AntiMalware 2.70.2.591 (Installed)
-------------------------------------------------------
Scan Result : Completed
Scan Date : 2017/1/29
Operating System : Windows 7 64-bit
Processor : 4X Intel(R) Core(TM)2 Quad CPU Q9400 @ 2.66GHz
BIOS Mode : Legacy
CUID : 127D5F9F4E1CF1EF5016BB
Scan Type : System Scan
Duration : 30m 48s
Scanned Objects : 219376
Detected Objects : 4
Excluded Objects : 0
Read Level : SCSI
Auto Upload : Enabled
Detect All Extensions : Disabled
Scan Documents : Disabled
Domain Info : WORKGROUP,0,2
Detected Objects
-------------------------------------------------------
Chrome Shortcut
Status : Scanned
Object : --app-id=gbchcmhmhahfdphkhkmpfmihenigjmpp
MD5 : -
Publisher : -
Size : -
Version : -
Detection : Suspicious Browser Setting
Cleaning Action : Repair
Related Objects :
Browser Setting - Chrome Shortcut
Chrome Startup Url
Status : Scanned
Object : Search
MD5 : -
Publisher : -
Size : -
Version : -
Detection : Suspicious Browser Setting
Cleaning Action : Repair
Related Objects :
Browser Setting - Chrome Startup Url
Chrome Startup Url
Status : Scanned
Object : Certified-Toolbar Search
MD5 : -
Publisher : -
Size : -
Version : -
Detection : Suspicious Browser Setting
Cleaning Action : Repair
Related Objects :
Browser Setting - Chrome Startup Url
F.B. Purity For Facebook
Status : Scanned
Object : %localappdata%\google\chrome\user data\profile 1\extensions\ncdlagniojmheiklojdcpdaeepochckl
MD5 : -
Publisher : -
Size : -
Version : -
Detection : PUA.ChromeExt!Gr
Cleaning Action : Repair
Related Objects :
Browser Extension - F.B. Purity For Facebook
Cleaning Result
-------------------------------------------------------
Cleaned : 4
Reported as safe : 0
Failed : 0
You may also like...
-
Google's 7-year slog to improve Chrome extensions still hasn't satisfied developers
- Started by oldschool
- Replies: 9
-
-