- May 4, 2019
- 825
- Content source
- https://shenaniganslabs.io/2021/04/13/Airstrike.html
By default, domain joined Windows workstations allow access to the network selection UI from the lock screen.
An attacker with physical access to a locked device with WiFi capabilities (such as a laptop or a workstation) can abuse this functionality to force the laptop to authenticate against a rogue access point and capture a MSCHAPv2 challenge response hash for the domain computer account.
This challenge response hash can then be submitted to crack.sh to recover the NTLM hash of the computer account in less than 24 hours.
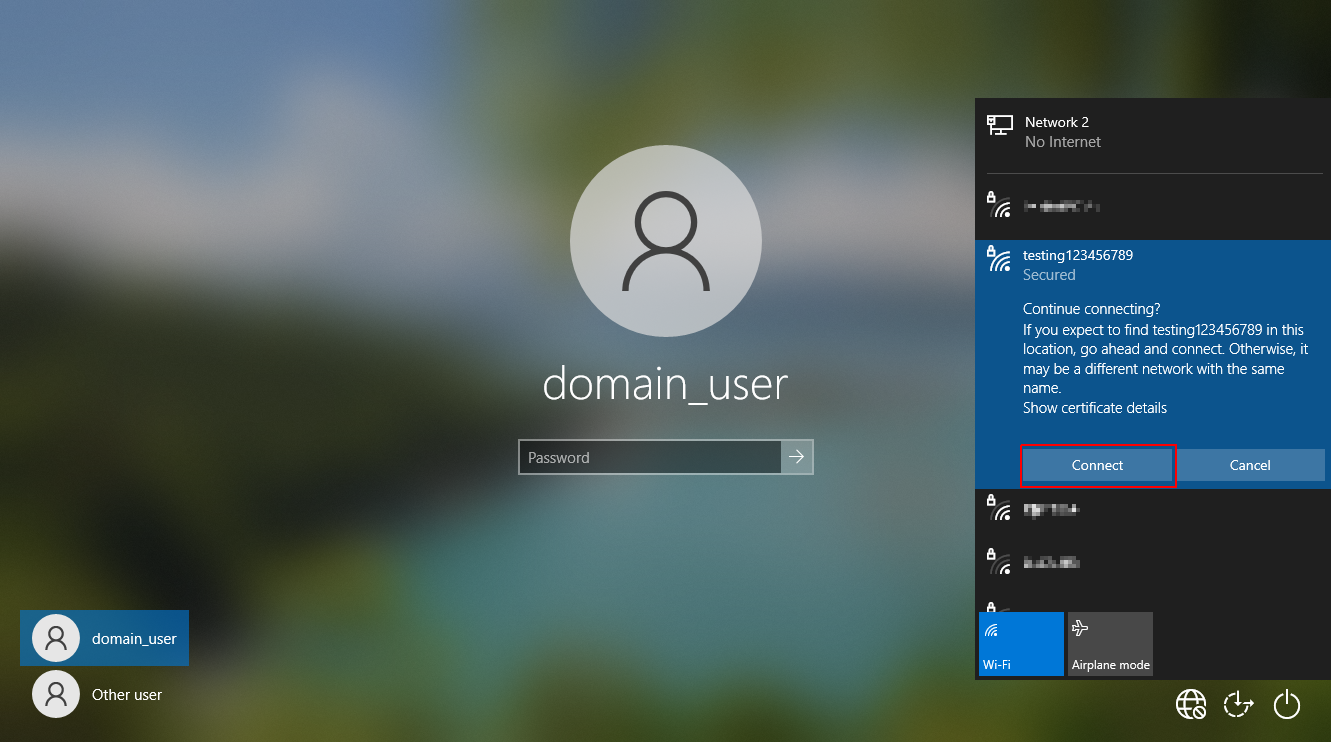
Airstrike Attack - FDE bypass and EoP on domain joined Windows workstations (CVE-2021-28316)
By default, domain joined Windows workstations allow access to the network selection UI from the lock screen. An attacker with physical access to a locked device with WiFi capabilities (such as a laptop or a workstation) can abuse this functionality to force the laptop to authenticate against a...
shenaniganslabs.io
