Unlike WannaCry this attack DOES NOT SCAN THE INTERNET, it spreads on the local subnet and after completion it REBOOTS & ENCRYPTS drive.
New ransomware outbreak
So yesterday I was on twitter during the Night time and there were reports all Over the place about a new petya ransomware possibly using eternalblue.
Ransomware includes: Modified EternalBlue exploit A vulnerability in a third-party Ukrainian software product A second SMB network exploit
So I decided to grab a sample and do some insight on this malware.
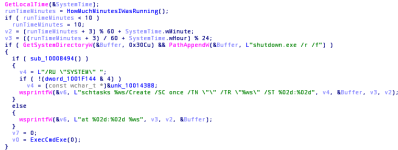
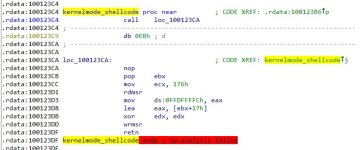
#EternalBlue, the malware has an x86 payload as shown in the screenshot below.
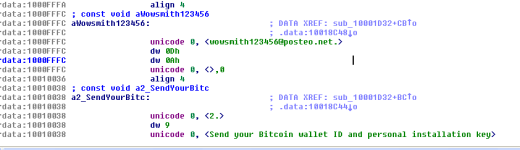
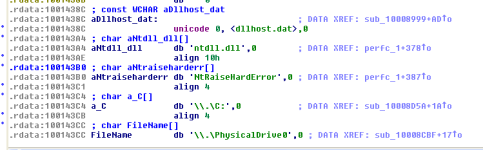
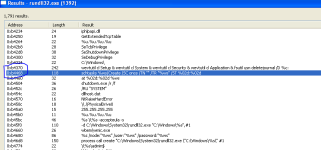
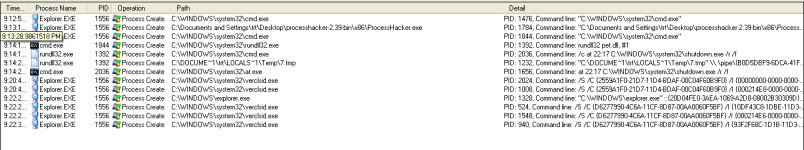
The new #Petya ransomware can do lateral movement via WMI and PSExec. Drops dllhost.dat, which is really signed PSExec
The attackers xored (0xcc) the shellcode (eb) to make sure the signature does not automatically get detected by anti-virus.
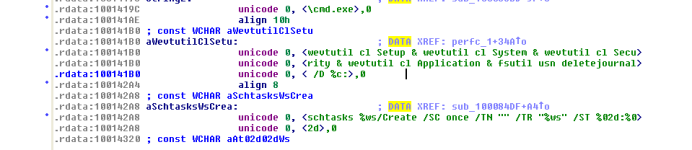
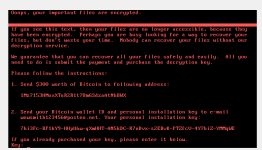
Logs are also being deleted.After a restart either by the user or by the task that was scheduled,it throws up a fake chkdsk screen like petya then it gives you the ransom message.
the amount of IPs it scans is dependant on subnet mask, but still limited to local network.
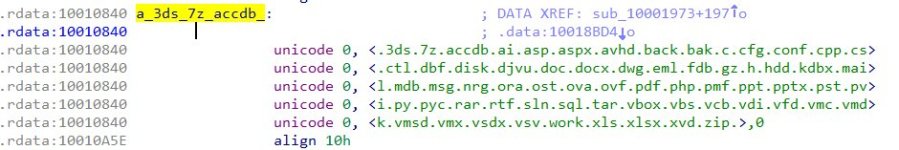
65 different file types are targeted by the ransomware.
.3ds,.7z,.accdb,.ai,.asp,.aspx,.avhd,.back,.bak,.c,.cfg,.conf,.cpp,.cs,.ctl,.dbf,.disk,.djvu,.doc,.docx,.dwg,.eml,.fdb,.gz,.h,.hdd,.kdbx,.mail,.mdb,.msg,.nrg,.ora,.ost,.ova,.ovf,.pdf,.php,.pmf,.ppt,.pptx,.pst,.pvi,.py,.pyc,.rar,.rtf,.sln,.sql,.tar,.vbox,.vbs,.vcb,.vdi,.vfd,.vmc,.vmdk,.vmsd,.vmx,.vsdx,.vsv,.work,.xls,.xlsx,.xvd,.zip
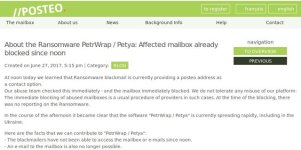
If you are infected with the latest Petya/Whatever you want to call it, restoring your MBR will not fix anything. MFT is still encrypted.Do NOT turn off your computer as soon as chkdsk screen appears if you want to save your files.
New ransomware outbreak
So yesterday I was on twitter during the Night time and there were reports all Over the place about a new petya ransomware possibly using eternalblue.
Ransomware includes: Modified EternalBlue exploit A vulnerability in a third-party Ukrainian software product A second SMB network exploit
So I decided to grab a sample and do some insight on this malware.
#EternalBlue, the malware has an x86 payload as shown in the screenshot below.
The new #Petya ransomware can do lateral movement via WMI and PSExec. Drops dllhost.dat, which is really signed PSExec
The attackers xored (0xcc) the shellcode (eb) to make sure the signature does not automatically get detected by anti-virus.
Logs are also being deleted.After a restart either by the user or by the task that was scheduled,it throws up a fake chkdsk screen like petya then it gives you the ransom message.
the amount of IPs it scans is dependant on subnet mask, but still limited to local network.
65 different file types are targeted by the ransomware.
.3ds,.7z,.accdb,.ai,.asp,.aspx,.avhd,.back,.bak,.c,.cfg,.conf,.cpp,.cs,.ctl,.dbf,.disk,.djvu,.doc,.docx,.dwg,.eml,.fdb,.gz,.h,.hdd,.kdbx,.mail,.mdb,.msg,.nrg,.ora,.ost,.ova,.ovf,.pdf,.php,.pmf,.ppt,.pptx,.pst,.pvi,.py,.pyc,.rar,.rtf,.sln,.sql,.tar,.vbox,.vbs,.vcb,.vdi,.vfd,.vmc,.vmdk,.vmsd,.vmx,.vsdx,.vsv,.work,.xls,.xlsx,.xvd,.zip
If you are infected with the latest Petya/Whatever you want to call it, restoring your MBR will not fix anything. MFT is still encrypted.Do NOT turn off your computer as soon as chkdsk screen appears if you want to save your files.
Attachments
-
 Capture.PNG19.3 KB · Views: 584
Capture.PNG19.3 KB · Views: 584 -
 Capture2.PNG42.1 KB · Views: 612
Capture2.PNG42.1 KB · Views: 612 -
 Capture3.PNG55.6 KB · Views: 598
Capture3.PNG55.6 KB · Views: 598 -
 Capture4.PNG68.3 KB · Views: 621
Capture4.PNG68.3 KB · Views: 621 -
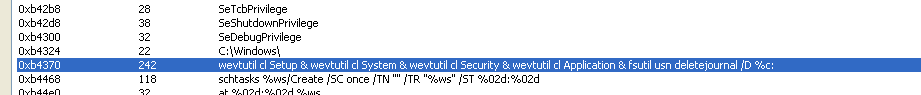 Capture5.PNG5 KB · Views: 606
Capture5.PNG5 KB · Views: 606 -
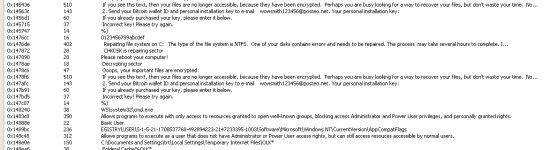 Capture6.PNG25.1 KB · Views: 600
Capture6.PNG25.1 KB · Views: 600 -
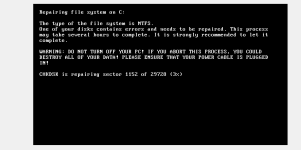 Capture7.PNG13.7 KB · Views: 610
Capture7.PNG13.7 KB · Views: 610 -
 DDWGcsIVYAETHTU.jpg60 KB · Views: 565
DDWGcsIVYAETHTU.jpg60 KB · Views: 565 -
 file exxts.jpg43.5 KB · Views: 603
file exxts.jpg43.5 KB · Views: 603 -
 ransom.PNG18.7 KB · Views: 594
ransom.PNG18.7 KB · Views: 594 -
 DDWdUMrUIAAFOyz.jpg119.3 KB · Views: 515
DDWdUMrUIAAFOyz.jpg119.3 KB · Views: 515
Last edited: