Yes you are right. I didn't see that. Wated my time on getting it manually. Wow lol.levelcomputer.exe? It's in my first post with the VT and hatching triage link
Question Analyzing SCR file
- Thread starter Fumerol_X
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
Microsoft Threat Experts confirm malicious and posted signature.
Xcitium Analysts still pending in que.
levelcomputer.exe is a cabinet file. After unpacking it with 7zip you will get 2 files ca 90 MB each, one is the 32 bit and the other the 64 bit variant of a similar .NET assembly.
64 bit: VirusTotal
32 bit: VirusTotal
I continued mainly with the 32 bit version. It downloads encrypted data from this URL and decodes it: VirusTotal
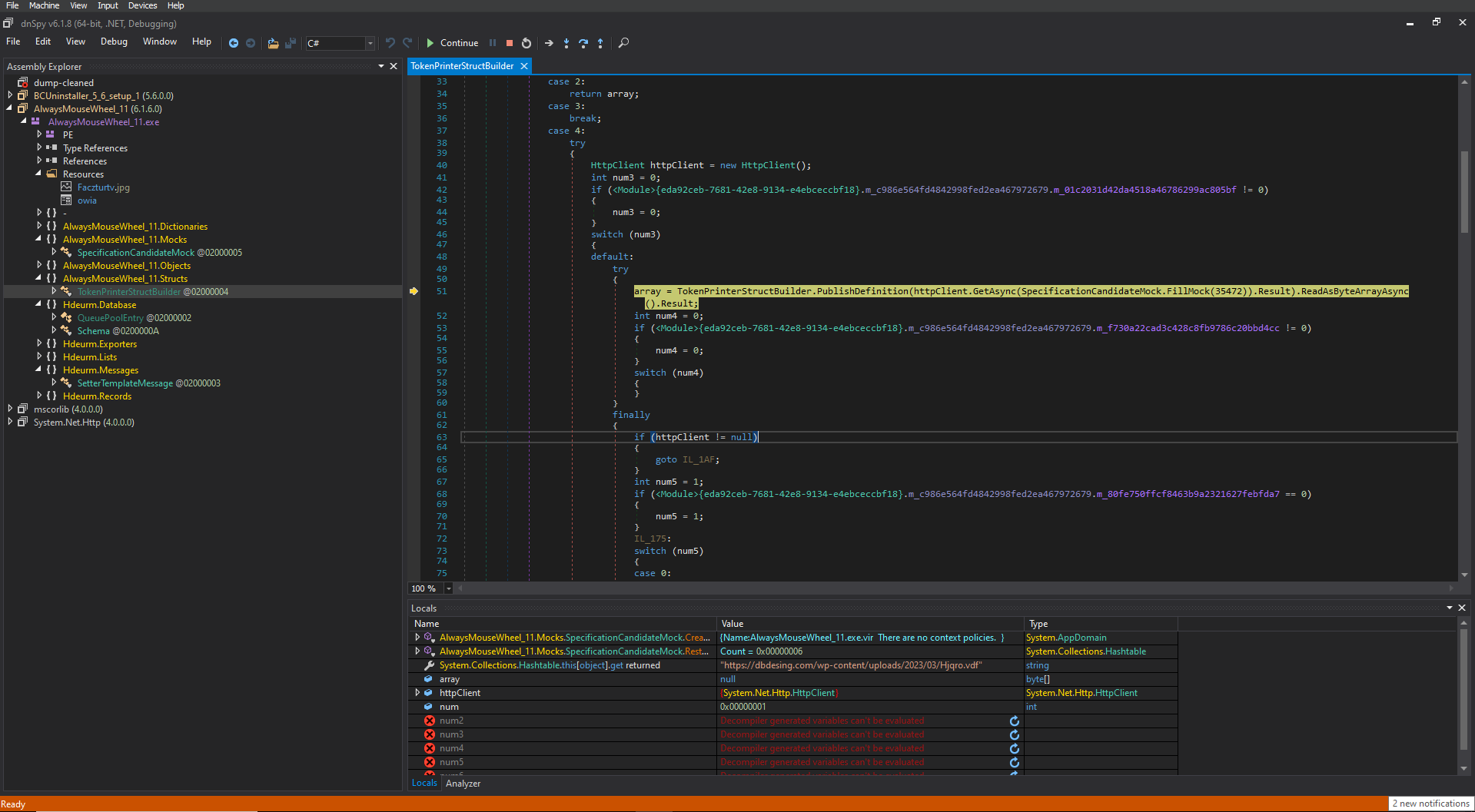
It performs process injection by running itself as a child process and injecting the payload there. I unpacked the payload and uploaded it here: VirusTotal
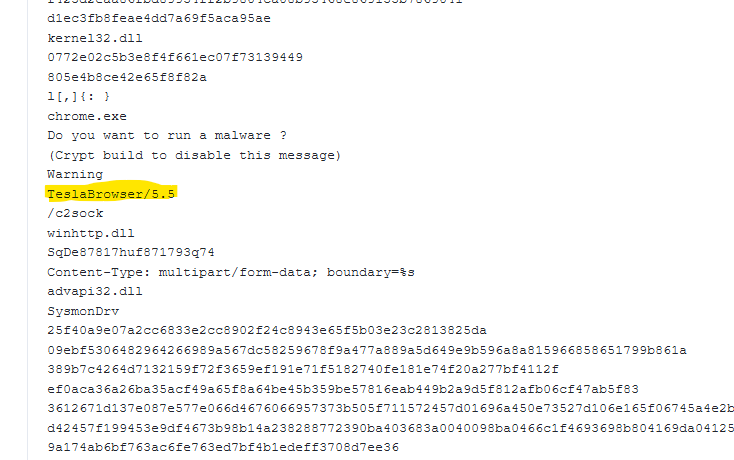
It is indeed LummaStealer. One of our analysts already worked on that malware family, hence we have a proper detection name here. It also sets the user agent TeslaBrowser/5.5 for its requests which is mentioned in this article about LummaStealer
64 bit: VirusTotal
32 bit: VirusTotal
I continued mainly with the 32 bit version. It downloads encrypted data from this URL and decodes it: VirusTotal
It performs process injection by running itself as a child process and injecting the payload there. I unpacked the payload and uploaded it here: VirusTotal
It is indeed LummaStealer. One of our analysts already worked on that malware family, hence we have a proper detection name here. It also sets the user agent TeslaBrowser/5.5 for its requests which is mentioned in this article about LummaStealer
Last edited:
I swear I aspire to be like you @struppigellevelcomputer.exe is a cabinet file. After unpacking it with 7zip you will get 2 files ca 90 MB each, one is the 32 bit and the other the 64 bit variant of a similar .NET assembly.
64 bit: VirusTotal
32 bit: VirusTotal
I continued with the 32 bit version. It downloads encrypted data from this URL and decodes it: VirusTotal
It performs process injection by running itself as a child process and injecting the payload there. I unpacked the payload and uploaded it here: VirusTotal
It is indeed LummaStealer. One of our analysts already worked on that sample, hence we have a proper detection name here. It also sets the user agent TeslaBrowser/5.5 for its requests which is mentioned in this article about LummaStealer
View attachment 278122
Goes to show they layers really matter.I find it funny that Kaspersky detects the loader, yet doesn’t detect the payload. Funny how that works
After looking, appears the packed version is UDS, so it does, just not with scanner.Goes to show they layers really matter.
Original file is also UDS, so I guess it wasn’t detected by Scanner at all. Still, good work for Kaspersky.
I saw the UDS when VT was at 6/80.After looking, appears the packed version is UDS, so it does, just not with scanner.
Original file is also UDS, so I guess it wasn’t detected by Scanner at all. Still, good work for Kaspersky.
We do truely love System Watcher.I saw the UDS when VT was at 6/80.
First of all guys I'm amazed about the help provided and your knowledge !
I'm currently working as a sysadmin sharing my time with cybersecurity tasks, spending my free time on hacking forums, trying to learn as much as I can (offensive and defensive). I'm planning to work as a SOC Analyst for 2024. But malware analysis is definitely a field I want to dive into in my free time.
Ow, and by the way I'm french so I'll probably have few questions about some words I didn't get. And pardon my English
@Sandbox Breaker@ :
- "File shows no GUI which further indacated their MO to stay hidden" > what "MO" stands for ?
- "Unique Code" > that means that the malware is new / not already known ?
Thanks for the tools shared ! I added some I didn't have yet (especially Xcitium, Intelix, Hatching)
- "Sophos ML Broken by this sample. Reputation is known but high TTD (Time to detect)." What do you mean by "Reputation is known but
high TTD" ?
How did you submitted the file to "Microsoft Threat Expert" ? Is it through the Microsoft Defender portal related to Microsoft 365 ?
I'm familiar with Microsoft 365, got the MS-500 and the interface makes me think of it.
- "Ok so here is Microsoft Deep Analysis(SAND BOX). Still waiting on their Human Analyst." > You mean that when a file is submitted and is not
known by the tool, there is a human analysis after that ?
- "Xcitium Broken but waiting on their Human Analysts also." > What do you mean by "Broken" ? I saw you used it before for Sophos ML,
does that mean "Xcitium doesn't work" ?
@struppigel@ :
"DnSpy does not work here because it cannot open .NETCore App singlefiles. You can open it with ILSpy, though." > Got it ! I'm adding this tool to my list
"The more interesting part will be the downloaded file. The levelcomputer.zip is 192 MB in size, so VT is not fond of it. I am gonna check if I can remove some bloat to share the file."
As far as I know VT can accept file up to 700Mb, what do you mean that it will not be fond of it ?
What do you mean by "Removing some bloat" ? I only know the term "Bloatware", however I know a method that consists of adding useless data to a payload in order to make it bigger and less trivial to analyze it, is it what you are talking about ?
@Xeno1234@ :
- "Original file is also UDS, so I guess it wasn’t detected by Scanner at all." > What do you mean by "UDS" ? I know FUD that makes a malware not recognizable
- "We do truely love System Watcher." > What is "System Watcher" ?
I'm currently working as a sysadmin sharing my time with cybersecurity tasks, spending my free time on hacking forums, trying to learn as much as I can (offensive and defensive). I'm planning to work as a SOC Analyst for 2024. But malware analysis is definitely a field I want to dive into in my free time.
Ow, and by the way I'm french so I'll probably have few questions about some words I didn't get. And pardon my English
@Sandbox Breaker@ :
- "File shows no GUI which further indacated their MO to stay hidden" > what "MO" stands for ?
- "Unique Code" > that means that the malware is new / not already known ?
Thanks for the tools shared ! I added some I didn't have yet (especially Xcitium, Intelix, Hatching)
- "Sophos ML Broken by this sample. Reputation is known but high TTD (Time to detect)." What do you mean by "Reputation is known but
high TTD" ?
How did you submitted the file to "Microsoft Threat Expert" ? Is it through the Microsoft Defender portal related to Microsoft 365 ?
I'm familiar with Microsoft 365, got the MS-500 and the interface makes me think of it.
- "Ok so here is Microsoft Deep Analysis(SAND BOX). Still waiting on their Human Analyst." > You mean that when a file is submitted and is not
known by the tool, there is a human analysis after that ?
- "Xcitium Broken but waiting on their Human Analysts also." > What do you mean by "Broken" ? I saw you used it before for Sophos ML,
does that mean "Xcitium doesn't work" ?
@struppigel@ :
"DnSpy does not work here because it cannot open .NETCore App singlefiles. You can open it with ILSpy, though." > Got it ! I'm adding this tool to my list
"The more interesting part will be the downloaded file. The levelcomputer.zip is 192 MB in size, so VT is not fond of it. I am gonna check if I can remove some bloat to share the file."
As far as I know VT can accept file up to 700Mb, what do you mean that it will not be fond of it ?
What do you mean by "Removing some bloat" ? I only know the term "Bloatware", however I know a method that consists of adding useless data to a payload in order to make it bigger and less trivial to analyze it, is it what you are talking about ?
@Xeno1234@ :
- "Original file is also UDS, so I guess it wasn’t detected by Scanner at all." > What do you mean by "UDS" ? I know FUD that makes a malware not recognizable
- "We do truely love System Watcher." > What is "System Watcher" ?
Modus operandi."MO" stands for ?
A Kaspersky module. I believe it replaced Application Control.What is "System Watcher" ?
UDS Is a Kaspersky Detection via Cloud Protection which states a file was detected via other means such as Behavioral Blocking rather than ScannerFirst of all guys I'm amazed about the help provided and your knowledge !
I'm currently working as a sysadmin sharing my time with cybersecurity tasks, spending my free time on hacking forums, trying to learn as much as I can (offensive and defensive). I'm planning to work as a SOC Analyst for 2024. But malware analysis is definitely a field I want to dive into in my free time.
Ow, and by the way I'm french so I'll probably have few questions about some words I didn't get. And pardon my English
@Sandbox Breaker@ :
- "File shows no GUI which further indacated their MO to stay hidden" > what "MO" stands for ?
- "Unique Code" > that means that the malware is new / not already known ?
Thanks for the tools shared ! I added some I didn't have yet (especially Xcitium, Intelix, Hatching)
- "Sophos ML Broken by this sample. Reputation is known but high TTD (Time to detect)." What do you mean by "Reputation is known but
high TTD" ?
How did you submitted the file to "Microsoft Threat Expert" ? Is it through the Microsoft Defender portal related to Microsoft 365 ?
I'm familiar with Microsoft 365, got the MS-500 and the interface makes me think of it.
- "Ok so here is Microsoft Deep Analysis(SAND BOX). Still waiting on their Human Analyst." > You mean that when a file is submitted and is not
known by the tool, there is a human analysis after that ?
- "Xcitium Broken but waiting on their Human Analysts also." > What do you mean by "Broken" ? I saw you used it before for Sophos ML,
does that mean "Xcitium doesn't work" ?
@struppigel@ :
"DnSpy does not work here because it cannot open .NETCore App singlefiles. You can open it with ILSpy, though." > Got it ! I'm adding this tool to my list
"The more interesting part will be the downloaded file. The levelcomputer.zip is 192 MB in size, so VT is not fond of it. I am gonna check if I can remove some bloat to share the file."
As far as I know VT can accept file up to 700Mb, what do you mean that it will not be fond of it ?
What do you mean by "Removing some bloat" ? I only know the term "Bloatware", however I know a method that consists of adding useless data to a payload in order to make it bigger and less trivial to analyze it, is it what you are talking about ?
@Xeno1234@ :
- "Original file is also UDS, so I guess it wasn’t detected by Scanner at all." > What do you mean by "UDS" ? I know FUD that makes a malware not recognizable
- "We do truely love System Watcher." > What is "System Watcher" ?
System Watcher is Kaspersky's Behavior Blocker which uses Deep ML and Signatures.
@struppigel@ :
"DnSpy does not work here because it cannot open .NETCore App singlefiles. You can open it with ILSpy, though." > Got it ! I'm adding this tool to my list
"The more interesting part will be the downloaded file. The levelcomputer.zip is 192 MB in size, so VT is not fond of it. I am gonna check if I can remove some bloat to share the file."
As far as I know VT can accept file up to 700Mb, what do you mean that it will not be fond of it ?
What do you mean by "Removing some bloat" ? I only know the term "Bloatware", however I know a method that consists of adding useless data to a payload in order to make it bigger and less trivial to analyze it, is it what you are talking about ?
Yes, that was what I meant. There is no reason those files need to be that big. Since automatic analysis systems often have a file size limit, some malware deliberately adds junk/bloat to be above that limit. Most of the time I can remove those junk bytes and create a smaller version of the same file. In this case I did not see an obvious way to remove the bloat because it is more integrated with the file.
Machines will never replace the Analyst. This is proof of that. So many "systems" were fooled by this long and encryption execution chain that it took Analyst's to un cloak this.Yes, that was what I meant. There is no reason those files need to be that big. Since automatic analysis systems often have a file size limit, some malware deliberately adds junk/bloat to be above that limit. Most of the time I can remove those junk bytes and create a smaller version of the same file. In this case I did not see an obvious way to remove the bloat because it is more integrated with the file.
"never" is perhaps too strong. I think this is like chess and Go, soon enough Ai will out-think us in all areas.Machines will never replace the Analyst. This is proof of that. So many "systems" were fooled by this long and encryption execution chain that it took Analyst's to un cloak this.
Let's see"never" is perhaps too strong. I think this is like chess and Go, soon enough Ai will out-think us in all areas.(must be true, look at all the billions being spent on Ai...)
Computing isn't thinking. One of many reasons is that creativity is part of the thinking process. Computing can employ randomness but not creativity. The example of driver-less cars is relevant here because a big problem is how the AI car responds to emergencies, stopping and clogging up access for emergency vehicles. San Francisco is a living nightmare of a lab experiment, and has warned other cities' leaders of the danger they pose.I think this is like chess and Go, soon enough Ai will out-think us in all areas.
The randomness of AI is what has most of us laughing. Just look at some of pure crap AI spits out, eg. just look at @Bot 's posts here on the forum.
Irrelevant.(must be true, look at all the billions being spent on Ai...)
sure, but "never" is a long time. We can chat about this again in + 5 years.Computing isn't thinking. One of many reasons is that creativity is part of the thinking process. Computing can employ randomness but not creativity. The example of driver-less cars is relevant here because a big problem is how the AI car responds to emergencies, stopping and clogging up access for emergency vehicles. San Francisco is a living nightmare of a lab experiment, and has warned other cities' leaders of the danger they pose.
The randomness of AI is what has most of us laughing. Just look at some of pure crap AI spits out, eg. just look at @Bot 's posts here on the forum.
Irrelevant.
a computer scientist (UK) recently wrote something re distinction (non-distinction) people & machines, "both are just collection of atoms..." (paraphrase)
You may also like...
-
Question Hi, please is this file malicious?
- Started by fedor345
- Replies: 9
-
Hot Take Missed script malware by signature analysis
- Started by Parkinsond
- Replies: 100
-
-

