“Foghorn” takes users out of phish-fighting with DNS “greylisting”:
SOURCE: arstechnica.com (ARTICLE DATE: 1 Sep 2016)
Eric Rand and Nik Labelle have been working on software that takes humans completely out of the loop in phishing defense by giving clicks on previously unseen domains a time out, "greylisting" them for 24 hours by default. The software, a project called Foghorn, does this by intercepting requests made to the Domain Name Service (DNS)...
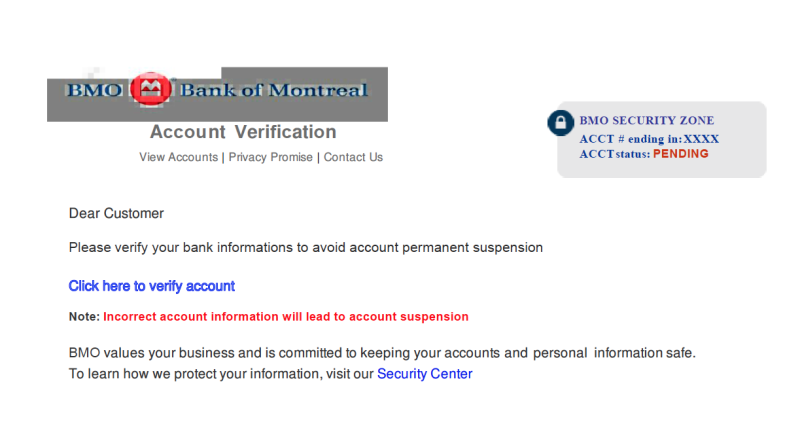
Greylisting has been used in spam filtering for e-mails, where it deliberately delays e-mails delivered from previously unseen sources and sends temporary errors back to the sender for a few minutes or hours. Spam greylisting operates under the assumption that a real mail server will re-attempt delivery, while spambots likely will not.
Foghorn applies the same approach to unseen domain names, but it does so for a different reason: many of the domains behind phishing attacks are active for less than 24 hours before they're rotated to another domain, according to an Anti-Phishing Working Group survey. As Rand said in his presentation about Foghorn at DefCon, "Lots of people are very invested in taking [phishing domains] down quickly, so phishers have to keep moving." By delaying the availability of previously unseen domains, the likelihood of users getting phished could be significantly reduced. Plus, known good domains can always be whitelisted. Additionally, greylisting domains can cut off the command and control for botnet malware that may have already infected systems on the network, since many botnets use random domain generation algorithms to evade detection and change the domains they access frequently—sometimes in as little as hours or minutes...
SOURCE: arstechnica.com (ARTICLE DATE: 1 Sep 2016)
Eric Rand and Nik Labelle have been working on software that takes humans completely out of the loop in phishing defense by giving clicks on previously unseen domains a time out, "greylisting" them for 24 hours by default. The software, a project called Foghorn, does this by intercepting requests made to the Domain Name Service (DNS)...

Greylisting has been used in spam filtering for e-mails, where it deliberately delays e-mails delivered from previously unseen sources and sends temporary errors back to the sender for a few minutes or hours. Spam greylisting operates under the assumption that a real mail server will re-attempt delivery, while spambots likely will not.
Foghorn applies the same approach to unseen domain names, but it does so for a different reason: many of the domains behind phishing attacks are active for less than 24 hours before they're rotated to another domain, according to an Anti-Phishing Working Group survey. As Rand said in his presentation about Foghorn at DefCon, "Lots of people are very invested in taking [phishing domains] down quickly, so phishers have to keep moving." By delaying the availability of previously unseen domains, the likelihood of users getting phished could be significantly reduced. Plus, known good domains can always be whitelisted. Additionally, greylisting domains can cut off the command and control for botnet malware that may have already infected systems on the network, since many botnets use random domain generation algorithms to evade detection and change the domains they access frequently—sometimes in as little as hours or minutes...
[To read the full article please visit arstechnica.com]