The Dutch National Police, Europol, Intel Security, and Kaspersky Lab joined forces today and announced the launch of No More Ransom, a Web portal that aggregates official information regarding ransomware, its mode of operation, and ways to fight it.
Accessible at nomoreransom.org, the portal contains a basic Q&A about how ransomware works, advice to prevent ransomware infections, and links where ransomware victims can report the infection (crime) to the appropriate agency in the EU and the US.
Shade ransomware decrypter available
The portal's Decryption Tools section will probably be the most visited page on the site, because users will find here decrypters for various ransomware families that can unlock their files without paying the ransom.
Currently, the page features decrypters for ransomware families such as CoinVault, Rannoh, AutoIt, Fury, Crybola, Cryakl, CryptXXX (v1 and v2), Rakhni, Agent.iih, Aura, Pletor, Rotor, Lamer, Lortok, Cryptokluchen, and Democry.
The latest addition to this list is the Shade (Troldesh) ransomware, for which Europol said they were able to seize the C&C servers, recover encryption keys, and use them to create a free decrypter. According to Microsoft, Shade is last month's tenth ranked ransomware in terms of activity.
A ransomware identification service that still needs some work
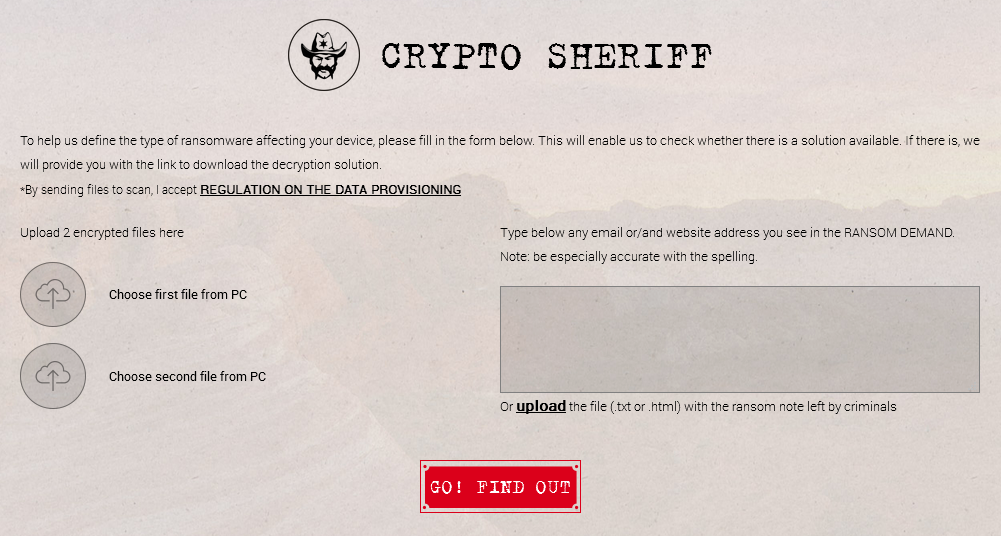
Another page, called Crypto Sheriff, also allows users to upload two encrypted files and the ransom note (or the ransom note's text), which would immediately tell victims with what type of ransomware they have been infected.
Once Crypto Sheriff identifies the threat, it will automatically provide a link to the decrypter.
The concept behind Crypto Sheriff is identical to the ID-Ransomware service created by Michael Gillespie, which at this point has become a mammoth project, capable of recognizing 145 ransomware families at the time of writing.
Unfortunately, after a few tests, Crypto Sheriff was not able to identify different types of ransomware such as Jigsaw, AMBA, or TeslaCrypt v3 and v4. The service looks like it still needs some work, so if nothing shows up, make sure to visit ID-Ransomware as well.
Anyhow, the portal is a step in the right direction, a sign that authorities are starting to notice this epidemic that has grown five times in the period of 2015-2016, compared to 2014-2015.
Accessible at nomoreransom.org, the portal contains a basic Q&A about how ransomware works, advice to prevent ransomware infections, and links where ransomware victims can report the infection (crime) to the appropriate agency in the EU and the US.
Shade ransomware decrypter available
The portal's Decryption Tools section will probably be the most visited page on the site, because users will find here decrypters for various ransomware families that can unlock their files without paying the ransom.
Currently, the page features decrypters for ransomware families such as CoinVault, Rannoh, AutoIt, Fury, Crybola, Cryakl, CryptXXX (v1 and v2), Rakhni, Agent.iih, Aura, Pletor, Rotor, Lamer, Lortok, Cryptokluchen, and Democry.
The latest addition to this list is the Shade (Troldesh) ransomware, for which Europol said they were able to seize the C&C servers, recover encryption keys, and use them to create a free decrypter. According to Microsoft, Shade is last month's tenth ranked ransomware in terms of activity.
A ransomware identification service that still needs some work
Another page, called Crypto Sheriff, also allows users to upload two encrypted files and the ransom note (or the ransom note's text), which would immediately tell victims with what type of ransomware they have been infected.
Once Crypto Sheriff identifies the threat, it will automatically provide a link to the decrypter.
The concept behind Crypto Sheriff is identical to the ID-Ransomware service created by Michael Gillespie, which at this point has become a mammoth project, capable of recognizing 145 ransomware families at the time of writing.
Unfortunately, after a few tests, Crypto Sheriff was not able to identify different types of ransomware such as Jigsaw, AMBA, or TeslaCrypt v3 and v4. The service looks like it still needs some work, so if nothing shows up, make sure to visit ID-Ransomware as well.
Anyhow, the portal is a step in the right direction, a sign that authorities are starting to notice this epidemic that has grown five times in the period of 2015-2016, compared to 2014-2015.
