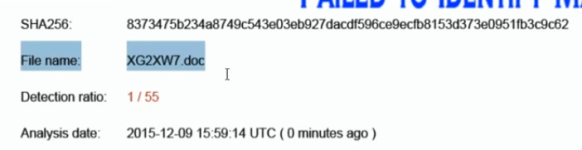
VT detection in the video is not the focus of the test. And so, it's irrelevant to bring into attention the unreliability of VT in testing. VT is just there to show that the file is at least detected as malicious by few AVs. 
When the file is established as malicious through VT, AppGuard is then tested against it.
AppGuard is the focus of the test, that is, how it prevents a malicious file doing its actions.
When the file is established as malicious through VT, AppGuard is then tested against it.
AppGuard is the focus of the test, that is, how it prevents a malicious file doing its actions.