<#
.SYNOPSIS
This function creates new AppLocker settings using MDM WMI Bridge.
All previous rules will be deleted.
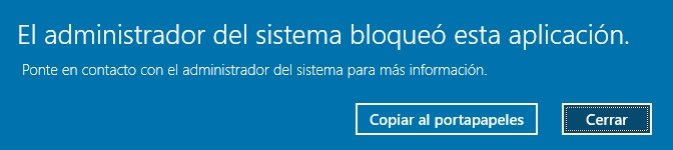
** EXE - all EXE allowed everywhere except LOLBins (blocked as Administrator too)
** DLL and MSI - blocked in some user folders (Documents, Favorites, Music, Pictures, Videos).
The settings include the below block rules:
<FilePathCondition Path="%OSDRIVE%\Users\*\Documents\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Favorites\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Music\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Pictures\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Videos\*"/>
The paths must be corrected if one or more user folders are redirected to OneDrive
or another location.
** DLL rules block also Administrators. Allow and Deny rules for DLL:
Allow all files located in the Program Files folder
Allow all files located in the Windows folder (with some exceptions for blocked writable folders)
Allow all signed files located in UserSpace (with some exceptions for blocked folders; can be
edited by the user)
Allow some paths for unsigned files located in UserSpace (can be edited by the user)
** MSI rules do not block Administrators. Allow rules:
Allow all files in the folder %systemdrive%\Windows\Installer
Allow all signed files everywhere (with some exceptions in Windows folder and UserSpace)
** Script rules do not block Administrators. Allow rules:
Allow all files located in the Program Files folder
Allow all files located in the Windows folder (with some exceptions for blocked writable folders)
** StoreApps rule blocks also Administrators. Allow rule:
Allow all signed files everywhere (with some exceptions in Windows folder and UserSpace)
--------------------------------------------------------------------------------------------------
The script uses some fake rules that are inactive. The fake path rules are:
A:\DLL_FakeWhitelistedPath\*
A:\DLL_FakeBlockedPath\*
A:\MSI_FakeBlockedPath\*
These rules have got the unused drive letter (A:), so they are always inactive, except when
the fake path is replaced by the real folder/file path.
Fake whitelisting rules require unique GUIDs.
The fake publisher block rule for LOLBins will be active after replacing the fake ProductName
with the asterisk, for example:
ProductName="HomeApplocker:POWERSHELL.EXE" ----> ProductName="*"
Similar fake rules are for powershell_ise.exe, and HH.exe .
The fake publisher block rule requires a unique GUID and the correct publisher info.
---------------------------------------------------------------------------------------------------
How to install applications.
Most of the EXE installers (signed or not) can be installed and used with enabled protection.
The signed MSI installers can be installed and used with enabled protection.
Some applications can still refuse to work properly after the installation if they try
to run some unsigned DLL libraries in UserSpace. This should be checked via Windows Event Log
(Applocker IDs: 8007, 8004).
---------------------------------------------------------------------------------------------------
.CREDITS
These scripts are based on the script for EXE files made by Sandy Zeng (Sandy Tsang).
https://github.com/sandytsang/MSIntune/tree/master/Intune-PowerShell/AppLocker
#>
# Deleting all previous policies
$namespaceName = "root\cimv2\mdm\dmmap" #Do not change this
$GroupName = "AppLocker001" #Your own groupName
$parentID = "./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/$GroupName"
$classNameDLL = "MDM_AppLocker_DLL03" #Do not change this
Get-CimInstance -Namespace $namespaceName -ClassName $classNameDLL -Filter "ParentID=`'$parentID`' and InstanceID='DLL'" | Remove-CimInstance
$classNameEXE = "MDM_AppLocker_ApplicationLaunchRestrictions01_EXE03" #Do not change this
Get-CimInstance -Namespace $namespaceName -ClassName $classNameEXE -Filter "ParentID=`'$parentID`' and InstanceID='EXE'" | Remove-CimInstance
$classNameMSI = "MDM_AppLocker_MSI03" #Do not change this
Get-CimInstance -Namespace $namespaceName -ClassName $classNameMSI -Filter "ParentID=`'$parentID`' and InstanceID='MSI'" | Remove-CimInstance
$classNameScript = "MDM_AppLocker_Script03" #Do not change this
Get-CimInstance -Namespace $namespaceName -ClassName $classNameScript -Filter "ParentID=`'$parentID`' and InstanceID='Script'" | Remove-CimInstance
$classNameStoreApps = "MDM_AppLocker_ApplicationLaunchRestrictions01_StoreApps03"
Get-CimInstance -Namespace $namespaceName -ClassName $classNameStoreApps -Filter "ParentID=`'$parentID`' and InstanceID='Storeapps'" | Remove-CimInstance
Add-Type -AssemblyName System.Web
#This is example Rule Collection for EXE (*.exe, *.com)
$obj = [System.Net.WebUtility]::HtmlEncode(@"
<RuleCollection Type="Exe" EnforcementMode="Enabled">
<FilePathRule Id="9cff703a-6dbd-48f5-8ce3-94f8228b6ac4" Name="Allow all files everywhere" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="*"/>
</Conditions>
</FilePathRule>
# Publisher block rules for LOLBins
# ***********************
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96000" Name="POWERSHELL.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="HomeApplocker:POWERSHELL.EXE" BinaryName="POWERSHELL.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96001" Name="POWERSHELL_ISE.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="HomeApplocker:POWERSHELL_ISE.EXE" BinaryName="POWERSHELL_ISE.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96003" Name="RUNAS.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="RUNAS.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96004" Name="CIPHER.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="CIPHER.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96005" Name="MSBUILD.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="MSBUILD.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96006" Name="InstallUtil.exe" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="InstallUtil.exe">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96007" Name="REGSVCS.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="REGSVCS.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96008" Name="WMIC.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="WMIC.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a96009" Name="PRESENTATIONHOST.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="PRESENTATIONHOST.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a9600a" Name="JSC.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="JSC.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a9600b" Name="MSHTA.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="MSHTA.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a9600c" Name="MICROSOFT.WORKFLOW.COMPILER.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="MICROSOFT.WORKFLOW.COMPILER.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="f493e22c-63a9-4811-ab94-c5d8a8a9600d" Name="HH.EXE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="HomeApplocker:HH.EXE" BinaryName="HH.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
"@)
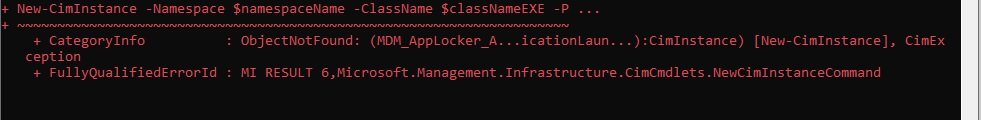
New-CimInstance -Namespace $namespaceName -ClassName $classNameEXE -Property @{ParentID=$parentID;InstanceID="EXE";Policy=$obj}
#This is example Rule Collection for MSI (*.msi, *.msp, *.mst)
$obj = [System.Net.WebUtility]::HtmlEncode(@"
<RuleCollection Type="Msi" EnforcementMode="Enabled">
<FilePublisherRule Id="b7af7102-efde-4369-8a89-7a6a392d1473" Name="Allow all signed" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
<Exceptions>
# Writable folders
<FilePathCondition Path="%WINDIR%\debug\wia\*" />
<FilePathCondition Path="%WINDIR%\registration\crmlog\*" />
<FilePathCondition Path="%SYSTEM32%\com\dmp\*" />
<FilePathCondition Path="%SYSTEM32%\config\systemprofile\appdata\local\packages\wdagrdpclientappcontainer\ac\*" />
<FilePathCondition Path="%SYSTEM32%\drivers\driverdata\*" />
<FilePathCondition Path="%SYSTEM32%\fxstmp\*" />
<FilePathCondition Path="%SYSTEM32%\microsoft\crypto\rsa\machinekeys\*" />
<FilePathCondition Path="%SYSTEM32%\spool\drivers\color\*" />
<FilePathCondition Path="%SYSTEM32%\spool\printers\*" />
<FilePathCondition Path="%SYSTEM32%\spool\servers\*" />
<FilePathCondition Path="%SYSTEM32%\tasks\*" />
<FilePathCondition Path="%SYSTEM32%\tasks_migrated\*" />
<FilePathCondition Path="%WINDIR%\tasks\*" />
<FilePathCondition Path="%WINDIR%\temp\*" />
<FilePathCondition Path="%WINDIR%\tracing\*" />
# Custom Block path rules in UserSpace for MSI (signed and unsigned)
# *****************************************************************
<FilePathCondition Path="%OSDRIVE%\Users\*\Documents\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Favorites\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Music\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Pictures\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Videos\*"/>
# Fake paths that can be edited by the user (replace A:\MSI_FakeBlockedPath with a real path)::
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\MSI_FakeBlockedPath\*"/>
# End of Block path rules in UserSpace for MSI.
</Exceptions>
</FilePublisherRule>
<FilePathRule Id="5b290184-345a-4453-b184-45305f6d9a54" Name="Allow files in the folder %systemdrive%\Windows\Installer." Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\Installer\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="64ad46ff-0d71-4fa0-a30b-3f3d30c5433d" Name="Allow for Administrators" Description="" UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
</RuleCollection>
"@)
New-CimInstance -Namespace $namespaceName -ClassName $classNameMSI -Property @{ParentID=$parentID;InstanceID="MSI";Policy=$obj}
#This is example Rule Collection for scripts (*.bat, *.cmd, *.vbe, *.vbs, *.jse, *js, *.wsf, *.wsh)
$obj = [System.Net.WebUtility]::HtmlEncode(@"
<RuleCollection Type="Script" EnforcementMode="Enabled">
<FilePathRule Id="06dce67b-934c-454f-a263-2515c8796a5d" Name="Allow scripts in Program Files folder" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="9428c672-5fc3-47f4-808a-a0011f36dd2c" Name="Allow scripts in Windows folder" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
<Exceptions>
# Writable folders
<FilePathCondition Path="%WINDIR%\debug\wia\*" />
<FilePathCondition Path="%WINDIR%\registration\crmlog\*" />
<FilePathCondition Path="%SYSTEM32%\com\dmp\*" />
<FilePathCondition Path="%SYSTEM32%\config\systemprofile\appdata\local\packages\wdagrdpclientappcontainer\ac\*" />
<FilePathCondition Path="%SYSTEM32%\drivers\driverdata\*" />
<FilePathCondition Path="%SYSTEM32%\fxstmp\*" />
<FilePathCondition Path="%SYSTEM32%\microsoft\crypto\rsa\machinekeys\*" />
<FilePathCondition Path="%SYSTEM32%\spool\drivers\color\*" />
<FilePathCondition Path="%SYSTEM32%\spool\printers\*" />
<FilePathCondition Path="%SYSTEM32%\spool\servers\*" />
<FilePathCondition Path="%SYSTEM32%\tasks\*" />
<FilePathCondition Path="%SYSTEM32%\tasks_migrated\*" />
<FilePathCondition Path="%WINDIR%\tasks\*" />
<FilePathCondition Path="%WINDIR%\temp\*" />
<FilePathCondition Path="%WINDIR%\tracing\*" />
</Exceptions>
</FilePathRule>
<FilePathRule Id="ed97d0cb-15ff-430f-b82c-8d7832957725" Name="Allow for Administrators" Description="" UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
</RuleCollection>
"@)
New-CimInstance -Namespace $namespaceName -ClassName $classNameScript -Property @{ParentID=$parentID;InstanceID="Script";Policy=$obj}
#This is example Rule Collection for DLL (*.cpl, *.dll, *.ocx, *.rll)
$obj = [System.Net.WebUtility]::HtmlEncode(@"
<RuleCollection Type="Dll" EnforcementMode="Enabled">
<FilePathRule Id="bac4b0bf-6f1b-40e8-8627-8545fa89c8b6" Name="Allow DLLs in Windows folder" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
<Exceptions>
# Writable folders
<FilePathCondition Path="%WINDIR%\debug\wia\*" />
<FilePathCondition Path="%WINDIR%\registration\crmlog\*" />
<FilePathCondition Path="%SYSTEM32%\com\dmp\*" />
<FilePathCondition Path="%SYSTEM32%\config\systemprofile\appdata\local\packages\wdagrdpclientappcontainer\ac\*" />
<FilePathCondition Path="%SYSTEM32%\drivers\driverdata\*" />
<FilePathCondition Path="%SYSTEM32%\fxstmp\*" />
<FilePathCondition Path="%SYSTEM32%\microsoft\crypto\rsa\machinekeys\*" />
<FilePathCondition Path="%SYSTEM32%\spool\drivers\color\*" />
<FilePathCondition Path="%SYSTEM32%\spool\printers\*" />
<FilePathCondition Path="%SYSTEM32%\spool\servers\*" />
<FilePathCondition Path="%SYSTEM32%\tasks\*" />
<FilePathCondition Path="%SYSTEM32%\tasks_migrated\*" />
<FilePathCondition Path="%WINDIR%\tasks\*" />
<FilePathCondition Path="%WINDIR%\temp\*" />
<FilePathCondition Path="%WINDIR%\tracing\*" />
</Exceptions>
</FilePathRule>
<FilePathRule Id="3737732c-99b7-41d4-9037-9cddfb0de0d0" Name="Allow DLLs in Program Files folder" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
# Global Allow rule in UserSpace for signed DLL
<FilePublisherRule Id="1f0d0ec5-8523-4aa0-976a-ad2d2c21eed7" Name="Allow all Signed" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
<Exceptions>
# Writable folders
<FilePathCondition Path="%WINDIR%\debug\wia\*" />
<FilePathCondition Path="%WINDIR%\registration\crmlog\*" />
<FilePathCondition Path="%SYSTEM32%\com\dmp\*" />
<FilePathCondition Path="%SYSTEM32%\config\systemprofile\appdata\local\packages\wdagrdpclientappcontainer\ac\*" />
<FilePathCondition Path="%SYSTEM32%\drivers\driverdata\*" />
<FilePathCondition Path="%SYSTEM32%\fxstmp\*" />
<FilePathCondition Path="%SYSTEM32%\microsoft\crypto\rsa\machinekeys\*" />
<FilePathCondition Path="%SYSTEM32%\spool\drivers\color\*" />
<FilePathCondition Path="%SYSTEM32%\spool\printers\*" />
<FilePathCondition Path="%SYSTEM32%\spool\servers\*" />
<FilePathCondition Path="%SYSTEM32%\tasks\*" />
<FilePathCondition Path="%SYSTEM32%\tasks_migrated\*" />
<FilePathCondition Path="%WINDIR%\tasks\*" />
<FilePathCondition Path="%WINDIR%\temp\*" />
<FilePathCondition Path="%WINDIR%\tracing\*" />
# Custom Block path rules in UserSpace for DLL (signed and unsigned)
# *****************************************************************
<FilePathCondition Path="%OSDRIVE%\Users\*\Documents\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Favorites\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Music\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Pictures\*"/>
<FilePathCondition Path="%OSDRIVE%\Users\*\Videos\*"/>
# Fake paths that can be edited by the user (replace A:\DLL_FakeBlockedPath with a real path)::
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
<FilePathCondition Path="A:\DLL_FakeBlockedPath\*"/>
# End of Block path rules in UserSpace for DLL.
</Exceptions>
</FilePublisherRule>
# Custom Allow path rules in UserSpace for DLL (replace A:\DLL_FakeWhitelistedPath , by the real path)
# ***************************************************************************************************
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6001" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6002" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6003" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6004" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6005" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6006" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6007" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6008" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b6009" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
<FilePathRule Id="ccff703a-6dbd-48f5-8ce3-94f8228b600a" Name="" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="A:\DLL_FakeWhitelistedPath"/>
</Conditions>
</FilePathRule>
# End of whitelisting path rules for DLL
</RuleCollection>
"@)
New-CimInstance -Namespace $namespaceName -ClassName $classNameDLL -Property @{ParentID=$parentID;InstanceID="DLL";Policy=$obj}
# Rule required to prevent blocking packaged apps when rules for EXE are enforced.
$obj = [System.Net.WebUtility]::HtmlEncode(@"
<RuleCollection Type="Appx" EnforcementMode="Enabled">
<FilePublisherRule Id="a9e18c21-ff8f-43cf-b9fc-db40eed693ba" Name="All signed" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
"@)
New-CimInstance -Namespace $namespaceName -ClassName $classNameStoreApps -Property @{ParentID=$parentID;InstanceID="Storeapps";Policy=$obj}
Write-Host "The script has finished the work. The console can be closed or it will be closed automatically after 5 minutes."
start-sleep 300