A new report from AV-TEST on self-protection of a large number of security software, both Consumer and Endpoint protection suites is out!
The test examined how well they deploy protection technologies such as ASLR & DEP, as usual.
A short introduction to ASLR and DEP for readers who are not familiar with these terms:
Address Space Layout Randomisation (ASLR) is a technology used to help prevent shellcode from being successful. It does this by randomly offsetting the location of modules and certain in-memory structures.
Data Execution Prevention (DEP) prevents certain memory sectors, e.g. the stack, from being executed. When combined it becomes exceedingly difficult to exploit vulnerabilities in applications using shellcode or return-oriented programming (ROP) techniques.
Here are the highlights:
Consumer Security



Endpoint (Corporate) Security

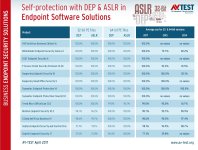

You can find more details on their report page.
The test examined how well they deploy protection technologies such as ASLR & DEP, as usual.
A short introduction to ASLR and DEP for readers who are not familiar with these terms:
Address Space Layout Randomisation (ASLR) is a technology used to help prevent shellcode from being successful. It does this by randomly offsetting the location of modules and certain in-memory structures.
Data Execution Prevention (DEP) prevents certain memory sectors, e.g. the stack, from being executed. When combined it becomes exceedingly difficult to exploit vulnerabilities in applications using shellcode or return-oriented programming (ROP) techniques.
Here are the highlights:
Consumer Security



Endpoint (Corporate) Security



You can find more details on their report page.