Vulnerability would have allowed attackers to take over computers running the Avast antivirus.
Czech antivirus maker Avast has taken the extreme step of disabling a major component of its antivirus product after a security researcher found a dangerous vulnerability that put all of the company's users at risk.
The security flaw was found in Avast's JavaScript engine, an internal component of the Avast antivirus that analyzes JavaScript code for malware before allowing it to execute in browsers or email clients.
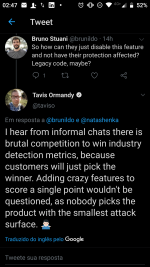
"Despite being highly privileged and processing untrusted input by design, it is unsandboxed and has poor mitigation coverage," said Tavis Ormandy, a security researcher at Google.
Any vulnerabilities in this process are critical, and easily accessible to remote attackers," Ormandy said on Monday when he also released a tool that he used to analyze the company's antivirus.
EXPLOITATION WAS TRIVIAL
Exploiting this type of bug is trivial. All it would take is sending a user a malicious JS or WSH file via email, or tricking a user into accessing a boobytrapped file with malicious JavaScript code.
Ormandy argues that once the Avast antivirus would download and run the malicious JavaScript code inside its own custom engine, malicious operations could be executed on the user's computer, with SYSTEM-level access.
For example, using this bug, attackers would have the ability to install malware on an Avast user's device.
AVAST NOTIFIED LAST WEEK
While Avast knew of the bug for almost a week, the company had yet to patch the issue, and earlier today, decided to disable its antivirus' JavaScript scanning capabilities until a patch would be ready.
Contacted by ZDNet for comment, the Czech company provided the following statement on the series of events that led to today's drastic measure.
"Last Wednesday, March 4, Google vulnerability researcher Tavis Ormandy reported a vulnerability to us affecting one of our emulators. The vulnerability could have potentially been abused to carry out remote code execution.
On March 9, he released a tool to greatly simplify vulnerability analysis in the emulator.
We have fixed this by disabling the emulator, to ensure our hundreds of millions of users are protected from any attacks. This won't affect the functionality of our AV product, which is based on multiple security layers."
There is no current timeline for when a patch would be ready.
Ormandy discovered the Avast antivirus bug using a tool he developed in 2017 that allows him to port Windows DLL files to Linux, where automated fuzzing and other security tests can be carried out more easily.
Source: Avast disables JavaScript engine in its antivirus following major bug | ZDNet
Czech antivirus maker Avast has taken the extreme step of disabling a major component of its antivirus product after a security researcher found a dangerous vulnerability that put all of the company's users at risk.
The security flaw was found in Avast's JavaScript engine, an internal component of the Avast antivirus that analyzes JavaScript code for malware before allowing it to execute in browsers or email clients.
"Despite being highly privileged and processing untrusted input by design, it is unsandboxed and has poor mitigation coverage," said Tavis Ormandy, a security researcher at Google.
Any vulnerabilities in this process are critical, and easily accessible to remote attackers," Ormandy said on Monday when he also released a tool that he used to analyze the company's antivirus.
EXPLOITATION WAS TRIVIAL
Exploiting this type of bug is trivial. All it would take is sending a user a malicious JS or WSH file via email, or tricking a user into accessing a boobytrapped file with malicious JavaScript code.
Ormandy argues that once the Avast antivirus would download and run the malicious JavaScript code inside its own custom engine, malicious operations could be executed on the user's computer, with SYSTEM-level access.
For example, using this bug, attackers would have the ability to install malware on an Avast user's device.
AVAST NOTIFIED LAST WEEK
While Avast knew of the bug for almost a week, the company had yet to patch the issue, and earlier today, decided to disable its antivirus' JavaScript scanning capabilities until a patch would be ready.
Contacted by ZDNet for comment, the Czech company provided the following statement on the series of events that led to today's drastic measure.
"Last Wednesday, March 4, Google vulnerability researcher Tavis Ormandy reported a vulnerability to us affecting one of our emulators. The vulnerability could have potentially been abused to carry out remote code execution.
On March 9, he released a tool to greatly simplify vulnerability analysis in the emulator.
We have fixed this by disabling the emulator, to ensure our hundreds of millions of users are protected from any attacks. This won't affect the functionality of our AV product, which is based on multiple security layers."
There is no current timeline for when a patch would be ready.
Ormandy discovered the Avast antivirus bug using a tool he developed in 2017 that allows him to port Windows DLL files to Linux, where automated fuzzing and other security tests can be carried out more easily.
Source: Avast disables JavaScript engine in its antivirus following major bug | ZDNet