- Feb 4, 2016
- 2,520
source (bleepingcomputer.com): Avira Introduces SafeThings to Protect your Network's IOT Devices
As electronics manufacturers rush to develop new connected gadgets, invariably there is always one thing that falls short; security. We have seen time and time again that connected devices, even though fun and helpful, can have very serious security issues.
These issues could allow attackers to enlist your devices into performing DDOS attacks like Mirai and IoT_reaper, invade your privacy by connecting to your WiFi cameras, or brick your devices using BrickerBot.
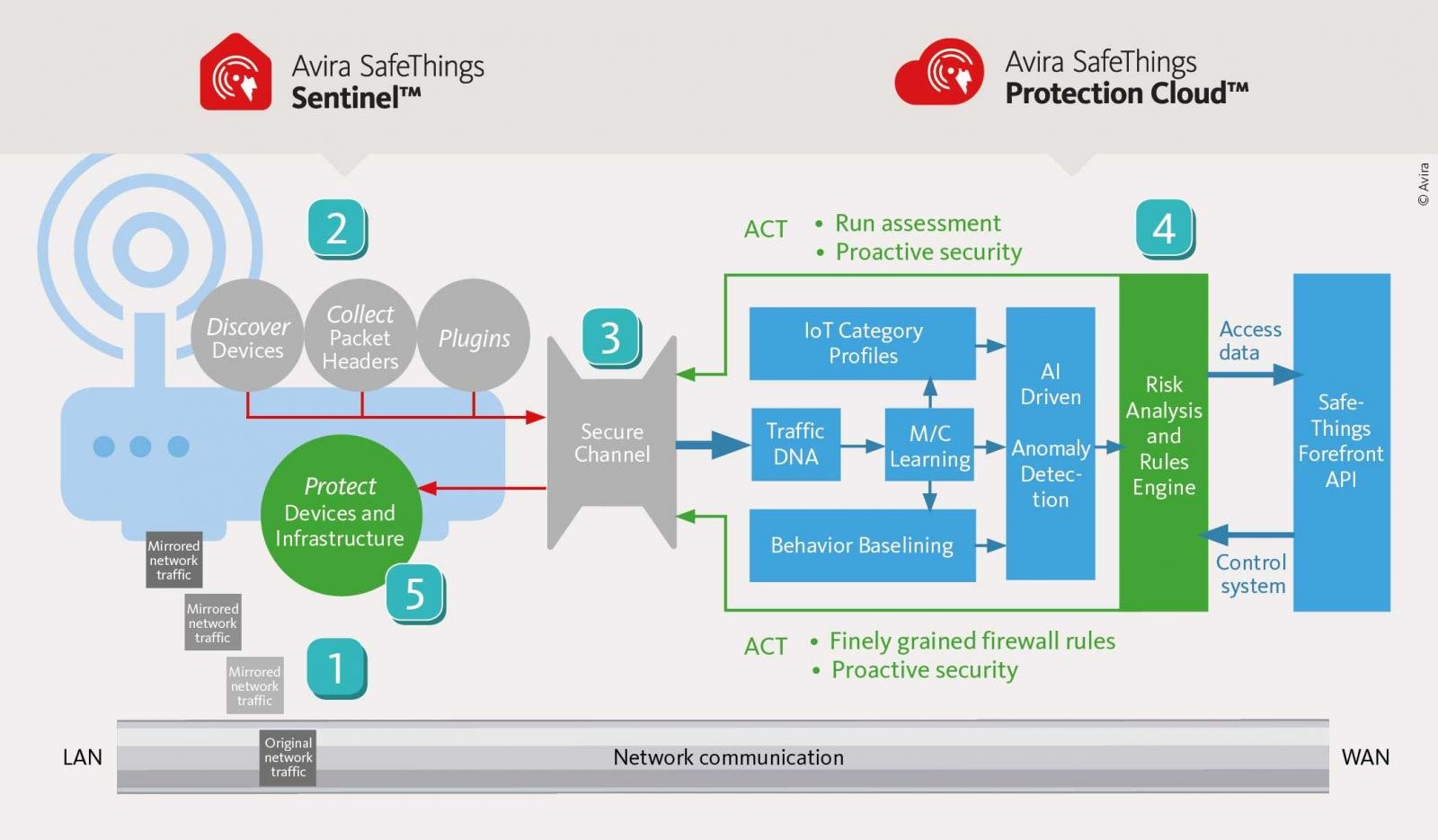
To help with this Avira has just launched a new solution called SafeThings, which is a software solution targeted at ISPs and router manufacturers to help protect consumers from poorly secured IoT devices.
Avira wants to take over IoT security
The Avira's SafeThings solution is a software component that ISPs and router manufacturers can add to their CPE, or Customer-Premises Equipment, in order to monitor for abnormal behavior in IoT devices and block them if detected. This software is called SafeThings Sentinel and quietly runs in the background in order to discover devices, analyze packet headers, and enforce protection rules on the router.
The Sentinel software on the router would then transmit the gathered data back to Avira's SafeThings Protection Cloud, which uses AI to learn the normal activity of the devices on the network. If it detects any anomalies, it will transmit back instructions on how the SafeThings Sentinel on the CPE should protect the network or alert the user.