My last analysis of Osno/Babax stealer

Conclusion:
Babax not only changes its name but also adds a Ring 3 rootkit and lateral spreading capabilities. Furthermore it has a ransomware component called OsnoLocker. Is this combination as dangerous as it sounds?
[...]
A colleague of mine discovered the first Osno stealer sample[1] on 5th October 2020. The sample[1] is a packed .NET assembly with the module name FallGuysStats. The module name indicates that it is using a statistics generator for the Steam game Fall Guys as a lure. The config shows version Osno 2.1.5 and has placeholders for some of the functions, including FTP and Telegram settings.
By the end of October researcher @backsla3h noted that the stealer is sold on forums. The advertisment comparison of Babax and Osno shows not only an increased price but also four more features or "Benefits" for Osno: r77 and network spreading, Anti-AV and evasion of WindowsDefender via allowlist, AnarchyGrabber and microphone records. Additionally there is a ransomware module which is not advertised (yet). Most of these features are described in the following sections
Conclusion:
Osno is not just a stealer anymore. Although that is still the main focus, the added capabilities pose a more serious threat, especially RDP access, lateral movement and file destruction.
However, none of that seems particularly scary.
Firstly, most of the serious sounding features are only possible after the malware sucessfully accessed the system and gained administrator privileges. That includes the rootkit and the anti-AV. The lateral movement portion depends on an external tool that needs to be downloaded first. It is only successful if network adminstrators disregard security measures alltogether, thus, unlikely to cause serious outbreaks.
Secondly, many of the stealer's features have been taken from public respositories and are known to defenders, making detection of the malware easier. Osno seems to have been worked around some of those tools. E.g., it uses the r77 rootkit binaries as is, although they are unfinished and only work with drawbacks. Osno renames its files to make them work for the rootkit binaries instead of implementing a rootkit that works for the Osno files.
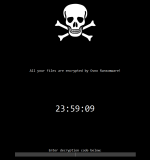
The ransomware, which may have been self-implemented, seems not finished yet, which is confirmed by existence of non-implemented XXTEA code and the fact that this feature is not advertised. Later versions will likely use encryption instead of destroying files.
Due to the mishmash of open-source code and tools from other malware Osno is best described as a patchwork Frankenstein's monster .