SHA256: 1bd52146e7240e771d1b7f8f9f8e30f51f28f0b6968ff71bd9b2b2829ba7b6be
File name: 1bd52146e7240e771d1b7f8f9f8e30f51f28f0b6968ff71bd9b2b2829ba7b6be.exe
File Size: 298496 bytes
File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
Detection ratio: 48 / 56
Analysis date: 2016-12-01 16:56:45 UTC
Detects VirtualBox through the presence of a library
process: {u'process_id': 1332, u'process_name': u'pV0IoR7wytjg.exe'}
signs: [{u'type': u'api', u'value': {u'category': u'system', u'status': False, u'return': u'0xc0000135', u'timestamp': u'2016-11-30 21:21:57,129', u'thread_id': u'1752', u'repeated': 0, u'api': u'LdrGetDllHandle', u'arguments': [{u'name': u'ModuleHandle', u'value': u'0x00000000'}, {u'name': u'FileName', u'value': u'VBoxHook.dll'}], u'id': 5295}}]
Detects VirtualBox through the presence of a device
process: None
signs: [{u'type': u'file', u'value': u'VBoxMiniRdrDN'}]
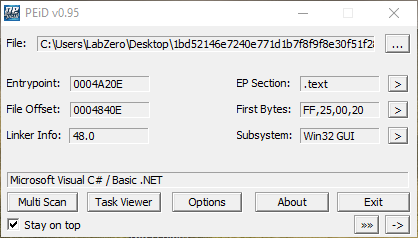
PEiD Analysis:
The sample is developed in .NET, and it seems that the majority of the source code is not obfuscated
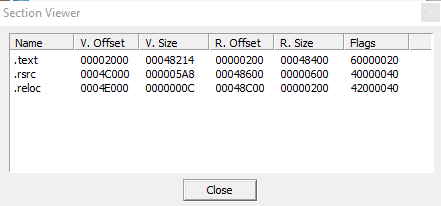
Here are the file sections:
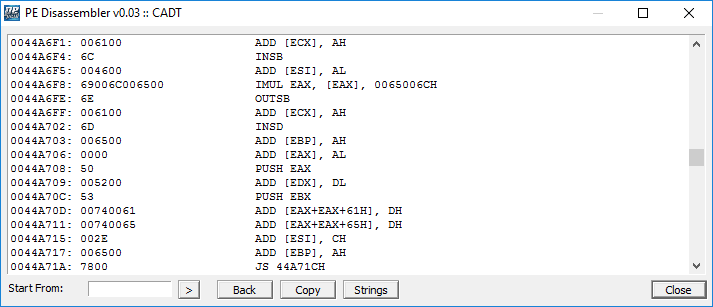
In the screenshot above we can analyze the dissassembler output, by seeing the assembly instructions, and you can assume the sample calls several times the JS function, which performs a jump to another callback according to the value of the flag.
From the screenshot below you can assume instead that part of the code is indeed encrypted, but let's focus also on the other strings!
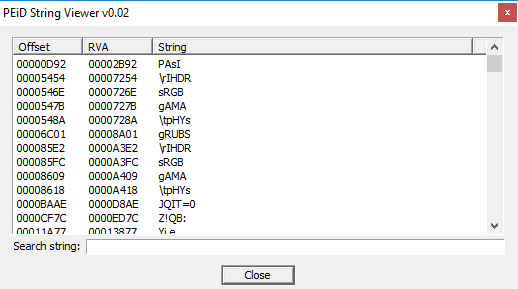
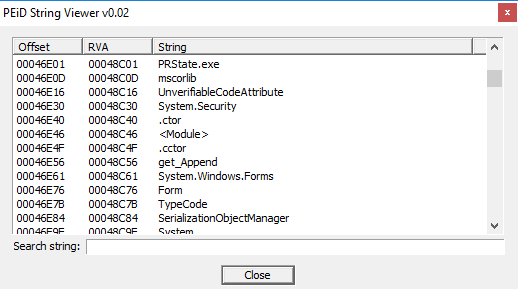
(HttpListenerTimeoutsElement)
Especially look at: "HTTP_REQUEST_INFO". Yes, the sample obviously performs connection operations, to a remote server to sends stolen data.
Instead, in the screenshot
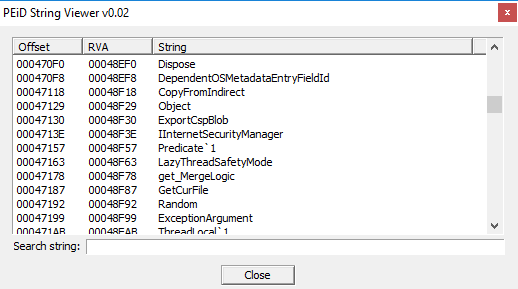
you can see the string "IInternetSecurityManager", which can manages deeply the security of Internet Explorer or also .NET based Web Browser applications. Internet Security Manager allows know in which security layer the URL belongs to, and what actions that page can do in this layer of security.
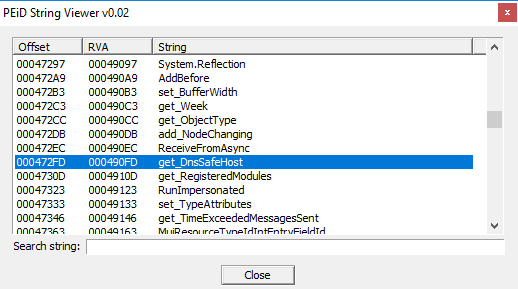
The "ReceiveFromAsync" method is used primarily to receive data on a connectionless socket.
The "get_DnsSafeHost" string contains the unescaped host part of the URI that is suitable for DNS resolution; or the original unescaped host string, if it is already suitable for resolution.
So it sends the resulting host name to a DNS server.
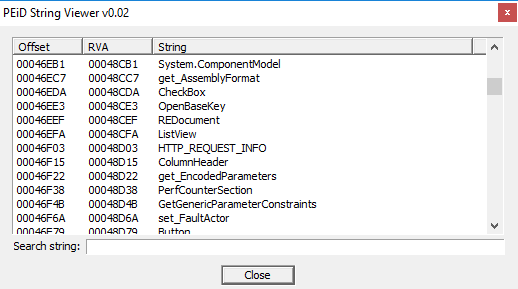
Also in the screenshot
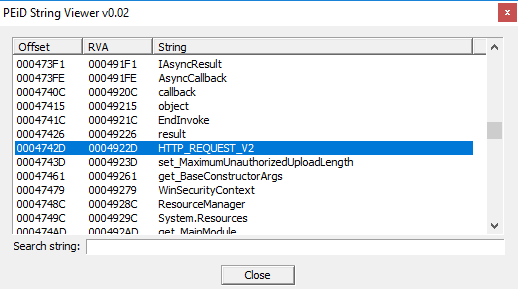
there are interesting and important strings: "HTTP_REQUEST_V2", "WinSecurityContext". Again the reference to HTTP requests methods, and WinSecurityContext is enough simple to understand what it refers to: it contains all security data for execution of contexts in threads executions.
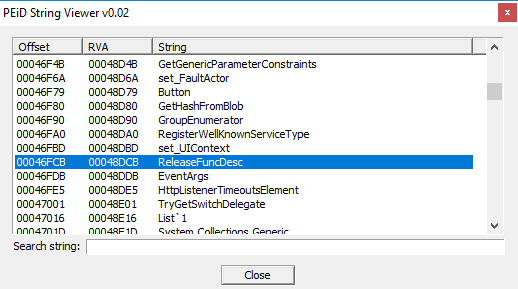
In this screenshot:
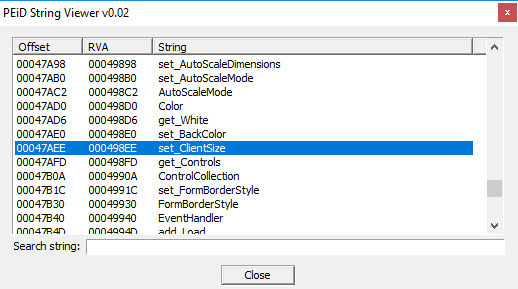
there are "set_ClientSize" string, which is a method used to specify the details of the client side, because of the connection with the remote server.
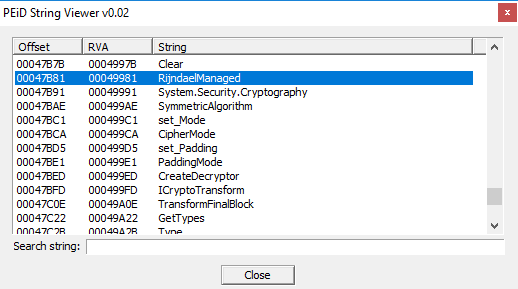
In the latest screenshot of PEiD analysis there are strings related to encryption process of the malware: "RijndelManaged", "System.Security.Cryptography", "CipherMode", "CreateDecryptor", ICryptoTransform".
Source Code Analysis
By analyzing the source code of this sample we can examine almost all functions called by it.
There are several methods related to encryption processes, but let's focus on all screenshots.
For example, in this screenshot
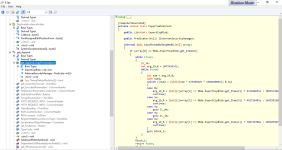
we can assume that one of the variable used is a InternetSecurityManager variable type; but there are also several HTTP related variables, used obviously during the execution of the functions, such as in the sch
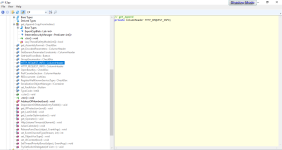
the variable HTTP_REQUEST_INFO.
The malware uses "infinite iterations" as text message and so it performs HTTP requests processes and it gets encoded parametres; but I can't see any loops in any function related to the connection to the remote server.
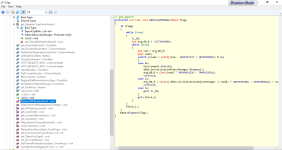
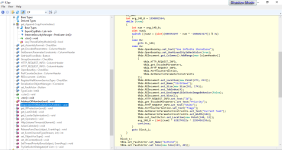
It seems that it uses the controls of the window to debugging the connection, by describing each step while connecting to the server.
It is a sort of "verbose malware" .
.
I found interesting the method "get_IPProtectionLevel()", it maybe gets information about frames management and IP host protection details. For this purpose it performs the operations with an iterator and it uses the method MoveNext() in a while loop to analyze each entry.
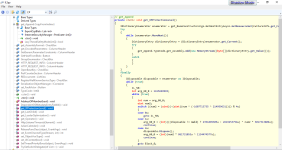
In the following sch I analyzed the method "private void HttpListenerTimeoutsElement()", it uses methods of "MuiResourceTypeIdIntEntryFieldId" to gather details about HTTP listener timeout.
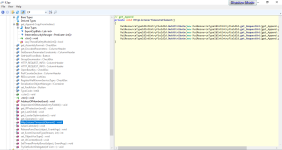
Then, the sample initialize a variable of type ResourceManager, it uses WinSecurityContext, it contains all security data for execution of contexts in threads executions as I mentioned before; but also the variable of type ResourceManager called GetHostEntryAsync, which refers to the method getIPProtectionLevel() is really interesting to identify the real purpose of this sample. So it gains security details about the infected user, in particular the IP protection level, but also it establish connections maybe to send this sensitive and personal data.
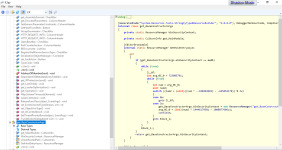
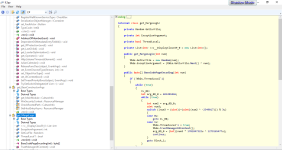
Now, with the latest 3 lines of code of this sch:
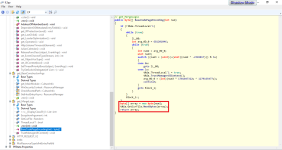
it seems that the sample initialize an array of bytes and it performs some byte operations of a specific file, in particular via NextBytes(array) function, so it gets as the parameter a bytes array.
Let's see the remaining important code of this malware!
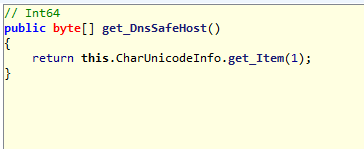
There are the method get_DnsSafeHost(), which allows the malcoder to send the resulting host name to a DNS server on his own,so we assume that the developer sends the data retrieved on his server, which can be also an administrative console.
In the method it uses "return this.CharUnicodeInfo.get_Item(1);", because CharUnicodeInfo is a List of bytes, and it uses this structure to store information about it.
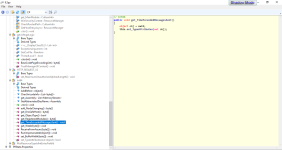
Then, the malware sets the time exceeded for the messages sent.
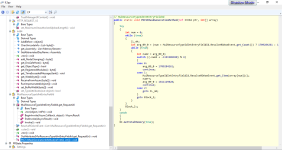
Finally in the latest function "PKCS1MaskGenerationMethod", which gets two parameters, it uses information retrieved with the function getIPProtectionLevel and it enter in an infinite "while(true)" loop to gather all information from get_IPProtectionLevel().
CONCLUSION:
At the end of the day, it seems quite well-coded backdoor sample. From the strings I found related to security, I found interesting ICryptoTransform, CreateDecryptor and CipherMode because I think it encrypts data during the transmission of the files to the remote server. This is a quite similar behaviour of APT samples.
Thanks everyone
File name: 1bd52146e7240e771d1b7f8f9f8e30f51f28f0b6968ff71bd9b2b2829ba7b6be.exe
File Size: 298496 bytes
File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
Detection ratio: 48 / 56
Analysis date: 2016-12-01 16:56:45 UTC
Detects VirtualBox through the presence of a library
process: {u'process_id': 1332, u'process_name': u'pV0IoR7wytjg.exe'}
signs: [{u'type': u'api', u'value': {u'category': u'system', u'status': False, u'return': u'0xc0000135', u'timestamp': u'2016-11-30 21:21:57,129', u'thread_id': u'1752', u'repeated': 0, u'api': u'LdrGetDllHandle', u'arguments': [{u'name': u'ModuleHandle', u'value': u'0x00000000'}, {u'name': u'FileName', u'value': u'VBoxHook.dll'}], u'id': 5295}}]
Detects VirtualBox through the presence of a device
process: None
signs: [{u'type': u'file', u'value': u'VBoxMiniRdrDN'}]
PEiD Analysis:
The sample is developed in .NET, and it seems that the majority of the source code is not obfuscated
Here are the file sections:
In the screenshot above we can analyze the dissassembler output, by seeing the assembly instructions, and you can assume the sample calls several times the JS function, which performs a jump to another callback according to the value of the flag.
From the screenshot below you can assume instead that part of the code is indeed encrypted, but let's focus also on the other strings!
(HttpListenerTimeoutsElement)
Especially look at: "HTTP_REQUEST_INFO". Yes, the sample obviously performs connection operations, to a remote server to sends stolen data.
Instead, in the screenshot
you can see the string "IInternetSecurityManager", which can manages deeply the security of Internet Explorer or also .NET based Web Browser applications. Internet Security Manager allows know in which security layer the URL belongs to, and what actions that page can do in this layer of security.
The "ReceiveFromAsync" method is used primarily to receive data on a connectionless socket.
The "get_DnsSafeHost" string contains the unescaped host part of the URI that is suitable for DNS resolution; or the original unescaped host string, if it is already suitable for resolution.
So it sends the resulting host name to a DNS server.
Also in the screenshot
there are interesting and important strings: "HTTP_REQUEST_V2", "WinSecurityContext". Again the reference to HTTP requests methods, and WinSecurityContext is enough simple to understand what it refers to: it contains all security data for execution of contexts in threads executions.
In this screenshot:
there are "set_ClientSize" string, which is a method used to specify the details of the client side, because of the connection with the remote server.
In the latest screenshot of PEiD analysis there are strings related to encryption process of the malware: "RijndelManaged", "System.Security.Cryptography", "CipherMode", "CreateDecryptor", ICryptoTransform".
Source Code Analysis
By analyzing the source code of this sample we can examine almost all functions called by it.
There are several methods related to encryption processes, but let's focus on all screenshots.
For example, in this screenshot

we can assume that one of the variable used is a InternetSecurityManager variable type; but there are also several HTTP related variables, used obviously during the execution of the functions, such as in the sch

the variable HTTP_REQUEST_INFO.
The malware uses "infinite iterations" as text message and so it performs HTTP requests processes and it gets encoded parametres; but I can't see any loops in any function related to the connection to the remote server.


It seems that it uses the controls of the window to debugging the connection, by describing each step while connecting to the server.
It is a sort of "verbose malware"
I found interesting the method "get_IPProtectionLevel()", it maybe gets information about frames management and IP host protection details. For this purpose it performs the operations with an iterator and it uses the method MoveNext() in a while loop to analyze each entry.

In the following sch I analyzed the method "private void HttpListenerTimeoutsElement()", it uses methods of "MuiResourceTypeIdIntEntryFieldId" to gather details about HTTP listener timeout.

Then, the sample initialize a variable of type ResourceManager, it uses WinSecurityContext, it contains all security data for execution of contexts in threads executions as I mentioned before; but also the variable of type ResourceManager called GetHostEntryAsync, which refers to the method getIPProtectionLevel() is really interesting to identify the real purpose of this sample. So it gains security details about the infected user, in particular the IP protection level, but also it establish connections maybe to send this sensitive and personal data.


Now, with the latest 3 lines of code of this sch:

it seems that the sample initialize an array of bytes and it performs some byte operations of a specific file, in particular via NextBytes(array) function, so it gets as the parameter a bytes array.
Let's see the remaining important code of this malware!
There are the method get_DnsSafeHost(), which allows the malcoder to send the resulting host name to a DNS server on his own,so we assume that the developer sends the data retrieved on his server, which can be also an administrative console.
In the method it uses "return this.CharUnicodeInfo.get_Item(1);", because CharUnicodeInfo is a List of bytes, and it uses this structure to store information about it.
Then, the malware sets the time exceeded for the messages sent.

Finally in the latest function "PKCS1MaskGenerationMethod", which gets two parameters, it uses information retrieved with the function getIPProtectionLevel and it enter in an infinite "while(true)" loop to gather all information from get_IPProtectionLevel().

CONCLUSION:
At the end of the day, it seems quite well-coded backdoor sample. From the strings I found related to security, I found interesting ICryptoTransform, CreateDecryptor and CipherMode because I think it encrypts data during the transmission of the files to the remote server. This is a quite similar behaviour of APT samples.
Thanks everyone