Bashware is the name of a new technique that allows malware to use a new Windows 10 feature called Subsystem for Linux (WSL) to bypass security software installed on an endpoint.
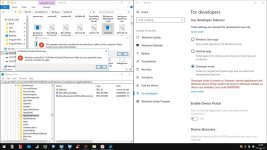
Back in 2016, Microsoft announced WSL as a way to run a Linux shell (Bash) inside the Windows 10 operating system. This was done to appeal to the developer community who primarily uses Linux due to its ease of use when it comes to programming-related tasks.
WSL works by taking Bash commands users type in a CLI, converting the shell commands to their Windows counterparts, processing the data inside the Windows kernel, and sending back a response, to both the Bash CLI and a local Linux file system.
The WSL feature has been under development in a beta stage since March 2016, but Microsoft recently announced WSL would reach a stable release this autumn with the release of the Windows 10 Fall Creators Update, scheduled for October 17.
Bashware attack is invisible to current security software
In a report issued late last night, security researchers from Check Point have published technical details about Bashware, a technique that allows malware devs to use Windows 10's secret Linux shell to hide malicious operations.
Researchers say that current security software, including next-gen antivirus solutions, fail to detect these operations.
This happens because all lack support for Pico processes, a new class of Windows processes that Microsoft added to handle WSL operations.
Bashware needs admin access, but that may not be a problem
The Bashware attack is not a surefire method to run malicious operations undetected on Windows. A Bashware attack, above all, requires administrator privileges.