Short analysis of the tested Batch ransomware found by @upnorth
Referenced thread: https://malwaretips.com/threads/ransom-bat-03-11-2020.104942/#post-912312
Malware type: Ransomware and dropper
File type: TXT, Batch
Ransomware behavior:
It uses certutil command to encode files to base64 and append .cxk_nmsl extension.
These files can be decoded back. There is no encryption whatsoever. A ransom note seems to be missing.
Intermediate files have .cxkdata extension. These are renamed versions of not yet encoded files and they are deleted by the sample after encoding.
The ransomware portion is very noisy and creates a visible terminal window as evident from this analysis: CXK-NMSL V3.2.bat (MD5: 01B575A1012B97988655980A48430DBB) - Interactive analysis - ANY.RUN
Or this screenshot:
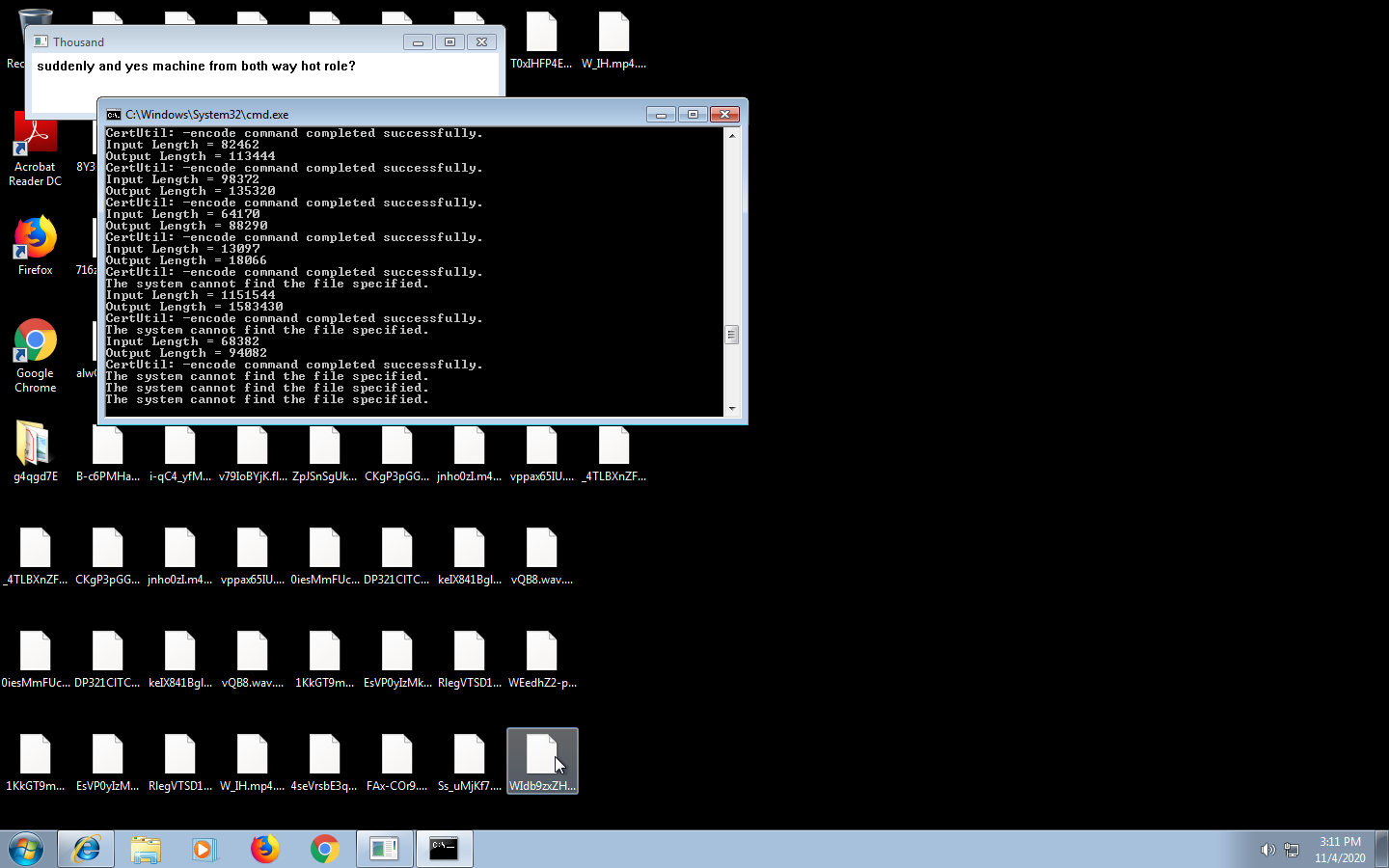
The message box content is just weird.
There is also a weird .mp3 file that is opened after encoding with VLC player. It's just a song. I guess the developer is just playing with things. Path of that file: %TEMP%/╝ª─π╠½├└.mp3
Dropper behavior:
Uses echo to write a big Base64 string into a file called x.
After decoding, x is a Portable Executable file which is detected as Flystudio trojan by most vendors. Identification is confirmed by strings like "Software\FlySky\E\Install\Path" in the binary.
VT link dropped file: VirusTotal
Referenced thread: https://malwaretips.com/threads/ransom-bat-03-11-2020.104942/#post-912312
Malware type: Ransomware and dropper
File type: TXT, Batch
Ransomware behavior:
It uses certutil command to encode files to base64 and append .cxk_nmsl extension.
These files can be decoded back. There is no encryption whatsoever. A ransom note seems to be missing.
Intermediate files have .cxkdata extension. These are renamed versions of not yet encoded files and they are deleted by the sample after encoding.
The ransomware portion is very noisy and creates a visible terminal window as evident from this analysis: CXK-NMSL V3.2.bat (MD5: 01B575A1012B97988655980A48430DBB) - Interactive analysis - ANY.RUN
Or this screenshot:
The message box content is just weird.
There is also a weird .mp3 file that is opened after encoding with VLC player. It's just a song. I guess the developer is just playing with things. Path of that file: %TEMP%/╝ª─π╠½├└.mp3
Dropper behavior:
Uses echo to write a big Base64 string into a file called x.
After decoding, x is a Portable Executable file which is detected as Flystudio trojan by most vendors. Identification is confirmed by strings like "Software\FlySky\E\Install\Path" in the binary.
VT link dropped file: VirusTotal
Last edited: