silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,176
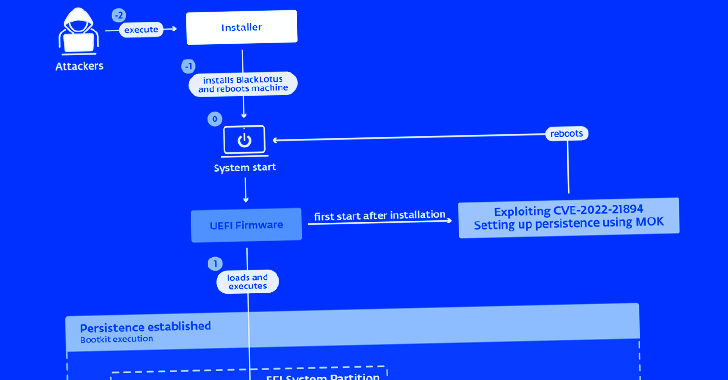
A stealthy Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape.
"This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.
"This is the first publicly known, in-the-wild abuse of this vulnerability," ESET researcher Martin Smolár said. "Its exploitation is still possible as the affected, validly signed binaries have still not been added to the UEFI revocation list."
"BlackLotus takes advantage of this, bringing its own copies of legitimate – but vulnerable – binaries to the system in order to exploit the vulnerability," effectively paving the way for Bring Your Own Vulnerable Driver (BYOVD) attacks.
BlackLotus Becomes First UEFI Bootkit Malware to Bypass Secure Boot on Windows 11
ESET warns of a new, powerful UEFI bootkit malware called BlackLotus that can bypass Secure Boot protection on Windows 11 systems.

BlackLotus UEFI bootkit: Myth confirmed | WeLiveSecurity
ESET researchers are the first to publish an analysis of BlackLotus, the first in-the-wild UEFI bootkit capable of bypassing UEFI Secure Boot.