Block a browser launch from a shell link in Eset HIPS
Hello,
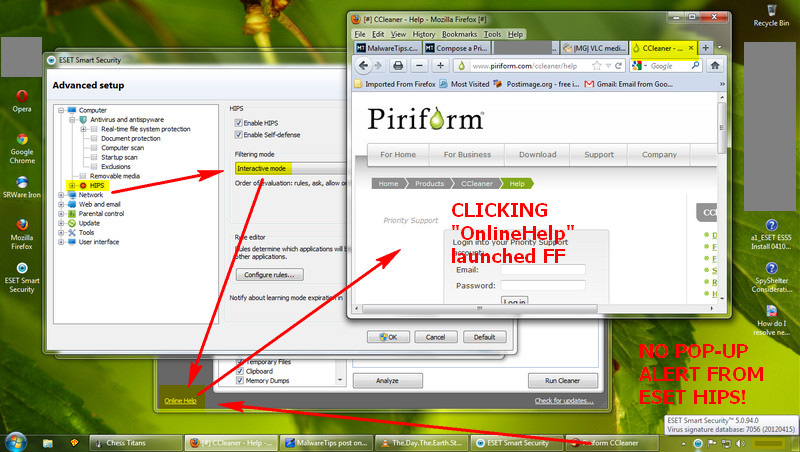
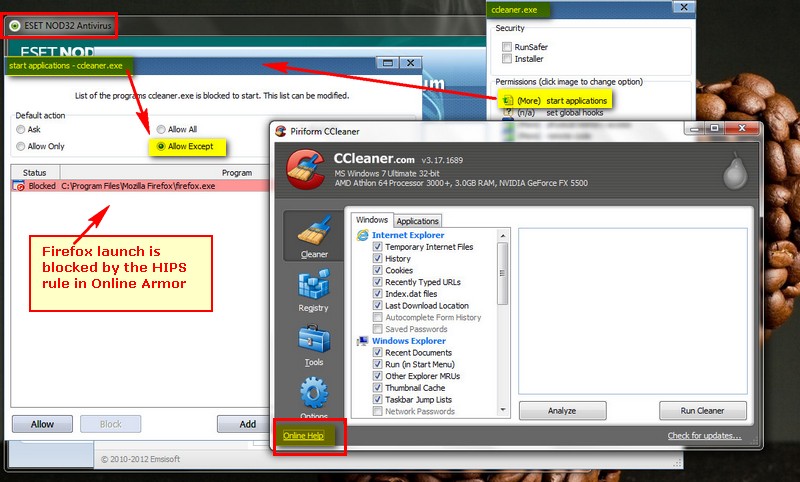
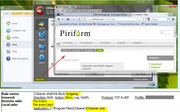
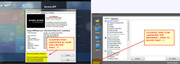
How can I block a link that launches a browser in an application GUI via Eset HIPS. In CIS and OA Premium I can block that in the HIPS portion to "not start an application". I see in ESS that it has this and I place a rule like in CCleaner:
Source application : C:\Program Files\CCleaner\CCleaner.exe
Target Application: Start new application
Over these applications: C:\Program Files\Mozilla Firefox\firefox.exe
Firefox still launches.
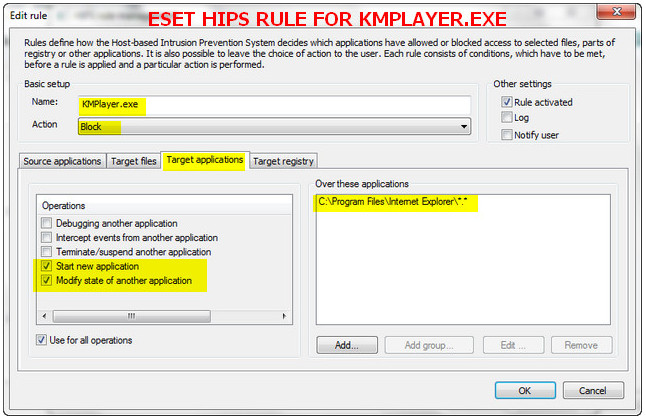
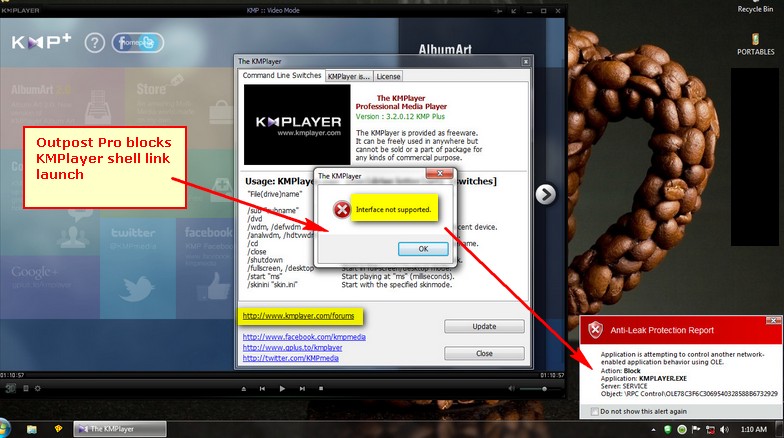
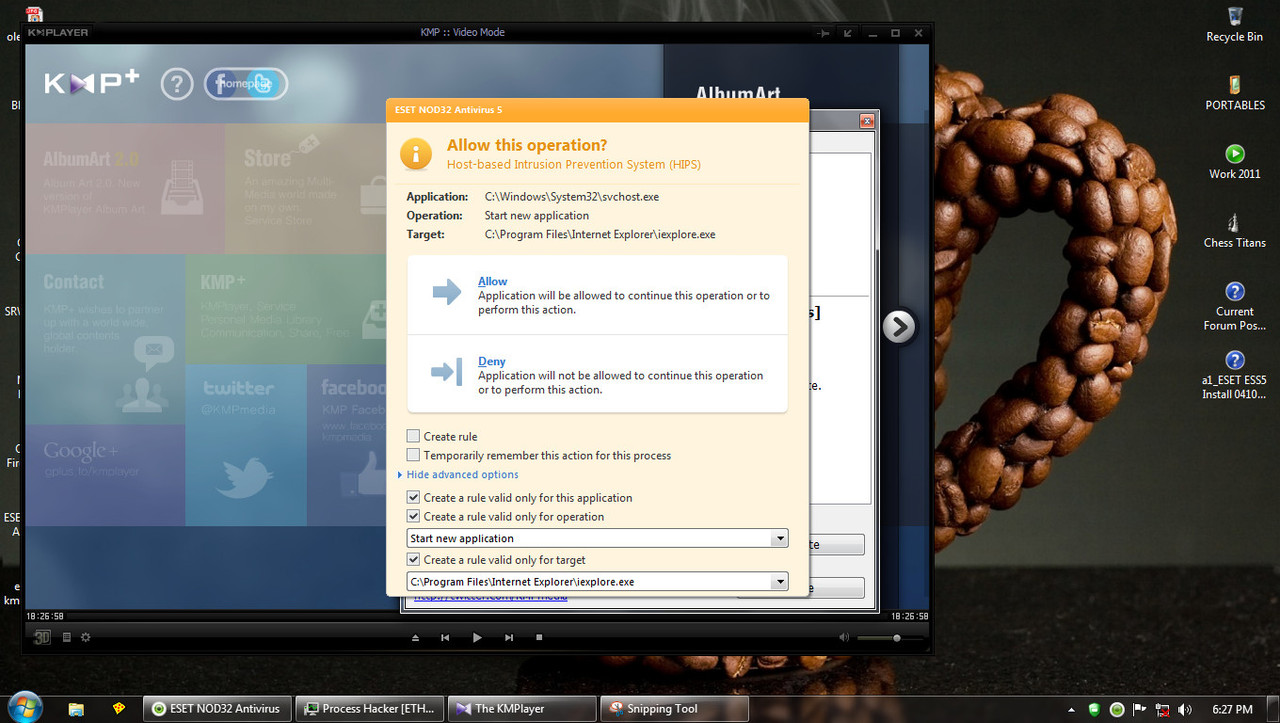
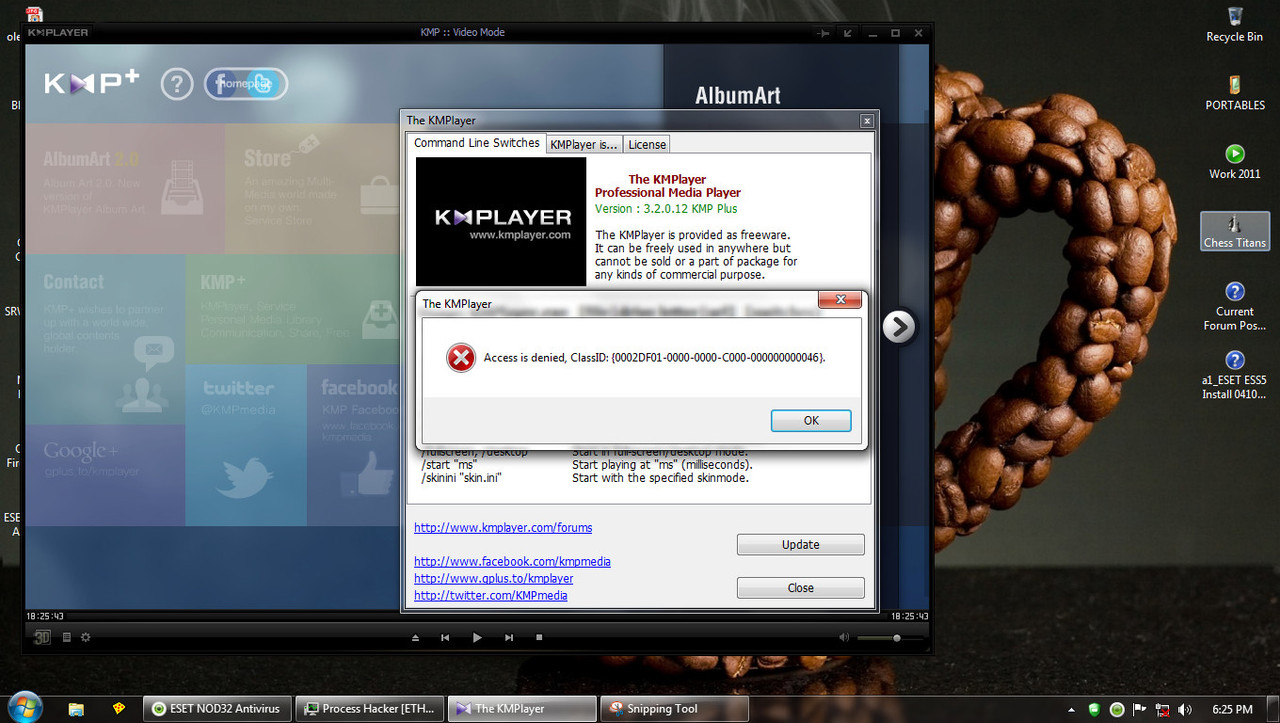
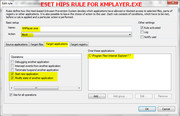
The same thing with KMPLayer but instead of FF it's IE. I placed the IE folder there in the "Over these application" but it still launches IE.
I used the same rule for some applications, like a freeware game that launches the default browser upon exit.
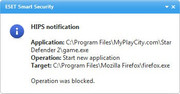
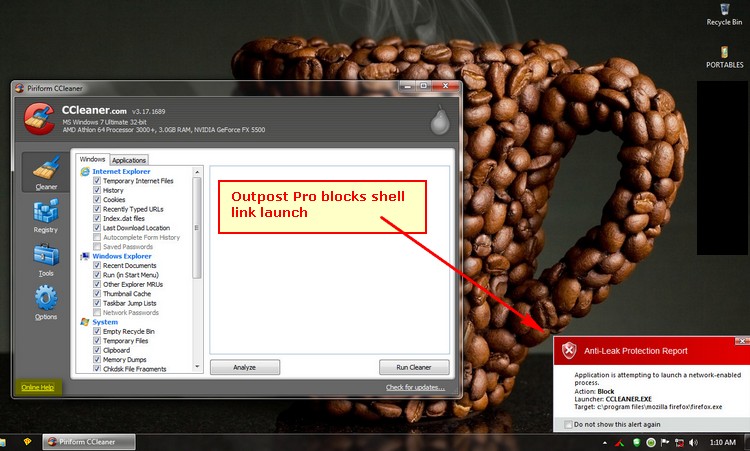
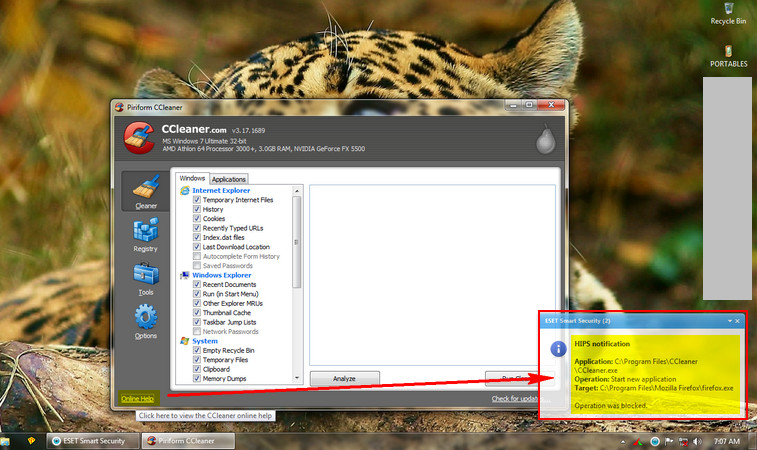
The Eset HIPS blocks it. On this two specific application (CCleaner and KMPlayer) the rule is useless.
In Comodo IS, KMPlayer uses COM so I place the block in COM Interfaces in D+. I assume that CCleaner is the same. Where can I plave that in ESS?
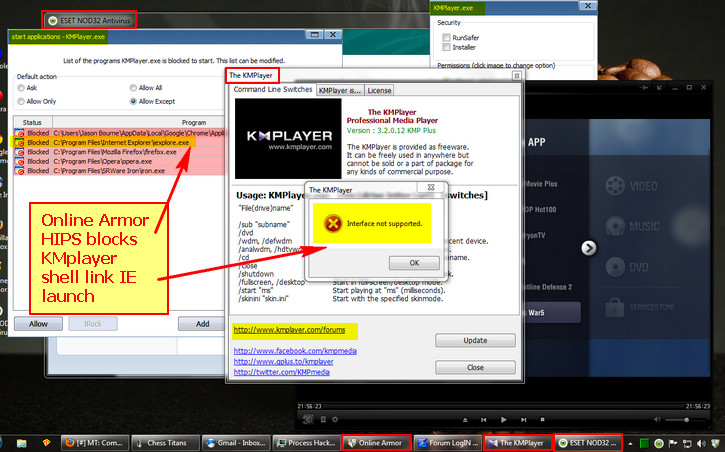
In OA Premium I placed it in the Advanced setup and add the broswers and it blocks it from launching.
How can I block such "shell links"(correct...?) in ESS HIPS...?
I'd like to be able to restrict such like these in the windows of applications other what I need. The kids might use the pc and might accidentally click. You know kids...
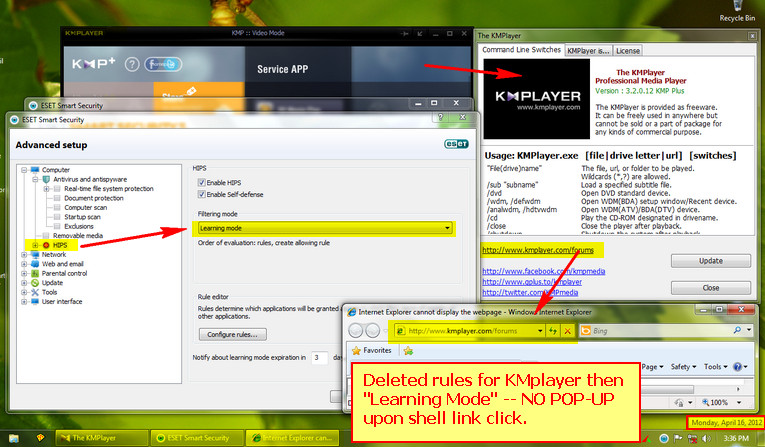
I tried to block the URL in KMPLayer but it also launched and connected. So blocking it via the firewall is useless also or the rule is wrong.
Kindly see images attached.
Please help
Hello,
How can I block a link that launches a browser in an application GUI via Eset HIPS. In CIS and OA Premium I can block that in the HIPS portion to "not start an application". I see in ESS that it has this and I place a rule like in CCleaner:
Source application : C:\Program Files\CCleaner\CCleaner.exe
Target Application: Start new application
Over these applications: C:\Program Files\Mozilla Firefox\firefox.exe
Firefox still launches.
The same thing with KMPLayer but instead of FF it's IE. I placed the IE folder there in the "Over these application" but it still launches IE.
I used the same rule for some applications, like a freeware game that launches the default browser upon exit.

The Eset HIPS blocks it. On this two specific application (CCleaner and KMPlayer) the rule is useless.
In Comodo IS, KMPlayer uses COM so I place the block in COM Interfaces in D+. I assume that CCleaner is the same. Where can I plave that in ESS?
In OA Premium I placed it in the Advanced setup and add the broswers and it blocks it from launching.
How can I block such "shell links"(correct...?) in ESS HIPS...?
I'd like to be able to restrict such like these in the windows of applications other what I need. The kids might use the pc and might accidentally click. You know kids...
I tried to block the URL in KMPLayer but it also launched and connected. So blocking it via the firewall is useless also or the rule is wrong.

Kindly see images attached.


Please help