Quote: " BPFDoor is interesting. It allows a threat actor to backdoor a system for remote code execution, without opening any new network ports or firewall rules. For example, if a webapp exists on port 443, it can listen and react on the existing port 443, and the implant can be reached over the webapp port (even with the webapp running). This is because it uses a BPF packet filter.
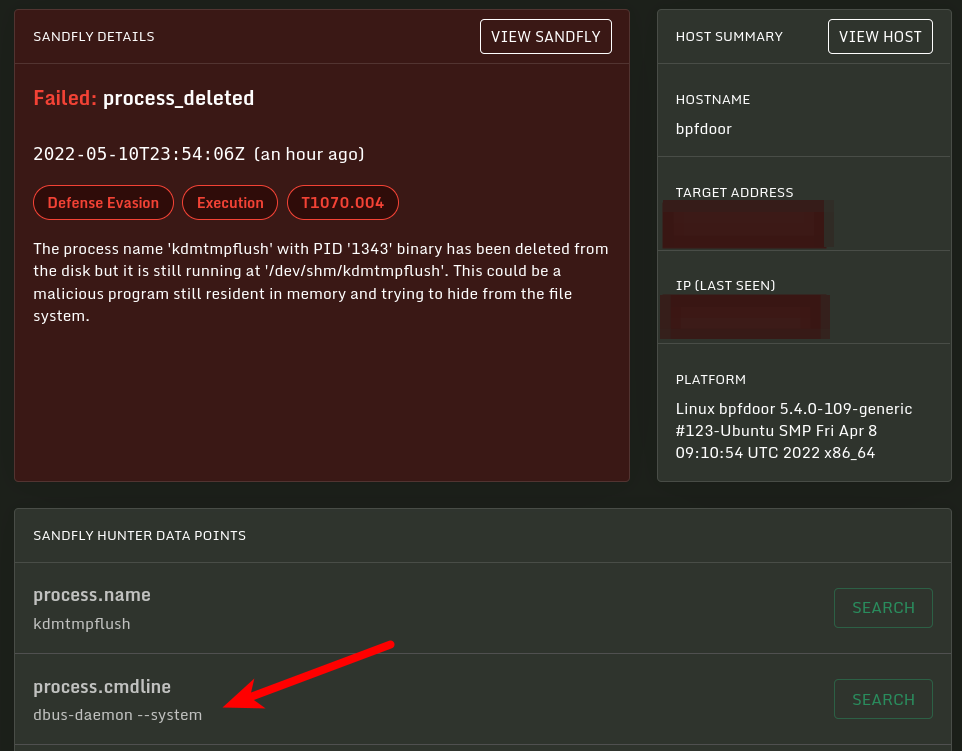
Operators have access to a tool which allows communication to the implants, using a password, which allows features such as remotely executing commands. This works over internal and internet networks. Because BPFDoor doesn’t open any inbound network ports, doesn’t use an outbound C2, and it renames its own process in Linux (so ps aux, for example, will show a friendly name) it is highly evasive. I swept the internet for BPFDoor throughout 2021, and discovered it is installed at organisations in across the globe— in particular the US, South Korea, Hong Kong, Turkey, India, Viet Nam and Myanmar, and is highly evasive. These organisations include government systems, postal and logistic systems, education systems and more. Inside those organisations I believe it is likely present on thousands of systems. The implant appears to be for surveillance purposes.
Per PwC: " We also identified that the threat actor sends commands to BPFDoor victims via Virtual Private Servers (VPSs) hosted at a well-known provider, and that these VPSs, in turn, are administered via compromised routers based in Taiwan, which the threat actor uses as VPN tunnels. Most Red Menshen activity that we observed took place between Monday to Friday (with none observed on the weekends), with most communication taking place between 01:00 and 10:00 UTC. This pattern suggests a consistent 8 to 9-hour activity window for the threat actor, with realistic probability of it aligning to local working hours. "
The implant has been in use for many years — over 5 — and has flown under the radar. "
" PwC plan to present their findings in June "

 doublepulsar.com
doublepulsar.com
Operators have access to a tool which allows communication to the implants, using a password, which allows features such as remotely executing commands. This works over internal and internet networks. Because BPFDoor doesn’t open any inbound network ports, doesn’t use an outbound C2, and it renames its own process in Linux (so ps aux, for example, will show a friendly name) it is highly evasive. I swept the internet for BPFDoor throughout 2021, and discovered it is installed at organisations in across the globe— in particular the US, South Korea, Hong Kong, Turkey, India, Viet Nam and Myanmar, and is highly evasive. These organisations include government systems, postal and logistic systems, education systems and more. Inside those organisations I believe it is likely present on thousands of systems. The implant appears to be for surveillance purposes.
Per PwC: " We also identified that the threat actor sends commands to BPFDoor victims via Virtual Private Servers (VPSs) hosted at a well-known provider, and that these VPSs, in turn, are administered via compromised routers based in Taiwan, which the threat actor uses as VPN tunnels. Most Red Menshen activity that we observed took place between Monday to Friday (with none observed on the weekends), with most communication taking place between 01:00 and 10:00 UTC. This pattern suggests a consistent 8 to 9-hour activity window for the threat actor, with realistic probability of it aligning to local working hours. "
The implant has been in use for many years — over 5 — and has flown under the radar. "
" PwC plan to present their findings in June "

BPFDoor — an active Chinese global surveillance tool
Recently, PwC Threat Intelligence documented the existence of BPFDoor, a passive network implant for Linux they attribute to Red Menshen…
 doublepulsar.com
doublepulsar.com