silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,743
- 123,908
- 8,399
The developers of the Brave Browser revealed in a new blog post on the official company site that the browser's logic for blocking content will change inthe upcoming Brave Browser 1.30 version.
Brave includes a content blocker by default that blocks resources similarly to how content blocking extensions such as uBlock Origin operate.
Brave Shields, the browser's blocking feature, is set to a standard level of blocking by default. The component includes other protections, such as automatic connection upgrades from HTTP to HTTPS, or fingerprinting protections.
The blocking logic of the browser changes in Brave 1.30 in the following way:
In order to improve privacy and Web compatibility, Brave will by default not apply network level filter list blocking to same-site subresources, starting in version 1.30, or the Beta and Nightly versions at time of this posting
Brave continues to block third-party resources just like before, even in standard mode. The company notes that it has decided to roll out the change for two reasons. First, because it improved protections in Brave that limit first-party subresource tracking, and second, to reduce the number of times Brave users need to turn off the browser's Shields feature to access sites or use certain functionality on sites.
Dropping Brave Shields disables the browser's content blocking. All site resources are loaded in that case.
How can privacy be improved if the blocking is reduced in the standard configuration? The company has two explanations for that.
For one, it reduces the number of times Brave users need to turn off the Shields feature. Besides impacting the current connection to the site and all resources loaded on it, it could result in users forgetting to re-enable the protective feature; this would reduce privacy in future sessions as well.
For the second reason, Brave notes that there is not much benefit in regards to privacy when it comes to blocking first-party requests. The IP address is known to the site already, and the browser's other protective features offer privacy protections against other forms of tracking.
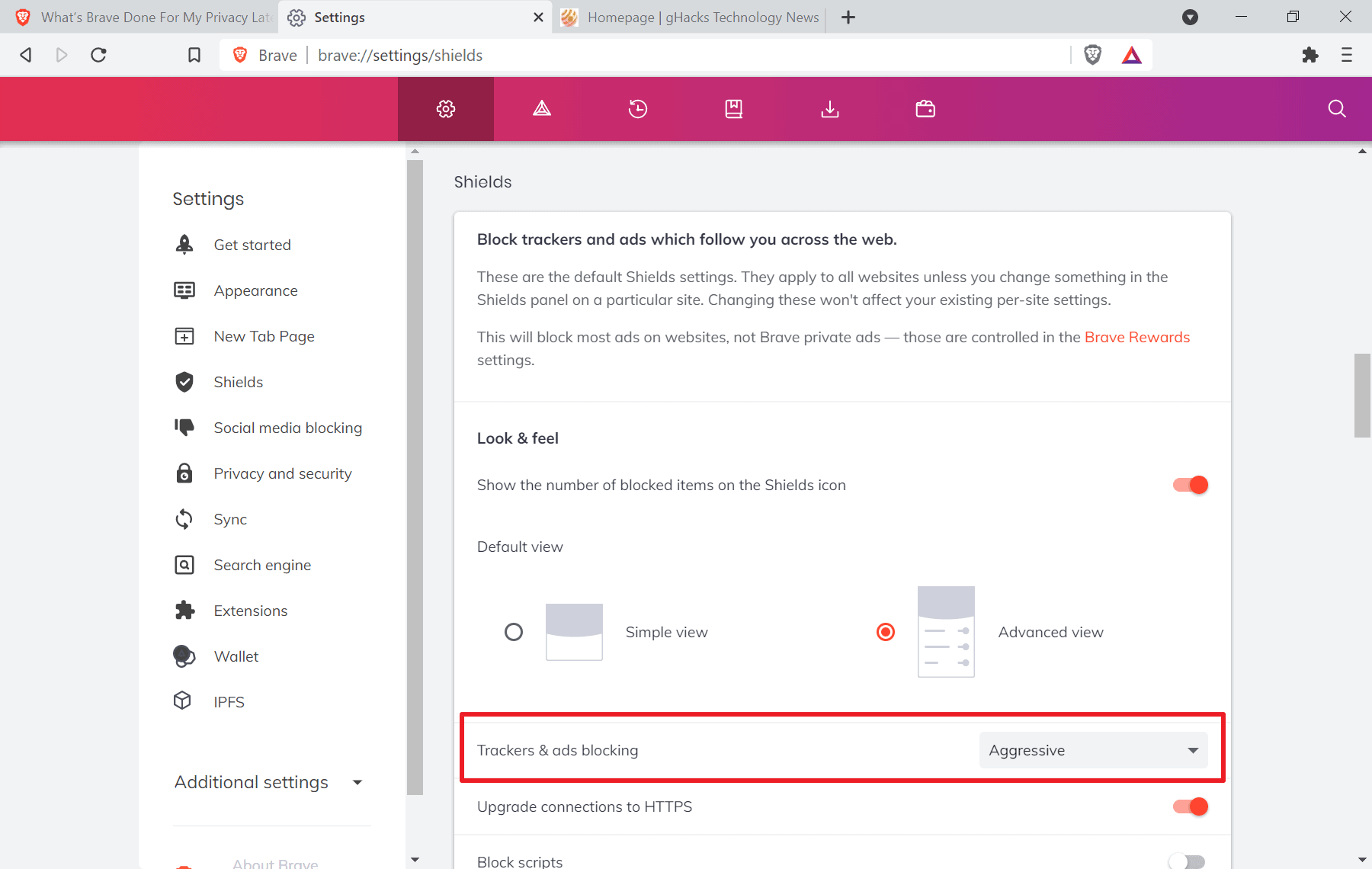
The change is applied to the default blocking behavior of the web browser only. Brave users who want to retain the previous blocking level may switch the blocking to aggressive, as it continues to block these first-party subresources.
Brave published a table that highlights the blocking behavior and differences between the browser's standard and aggressive blocking modes:
Standard (default) Aggressive Cosmetic filtering Hide page elements related to third-party advertising Hide page elements related to first and/or third party advertising Network filtering Apply filter lists to all third-party sub-resource requests Apply filter lists to all sub-resource requests, first and third-party alike Bounce tracking Strip known tracking query parameters from URLs Strip known tracking query parameters from URLs and warn users before navigating to suspected bounce tracking domains
Brave users who want to maintain the current level of blocking when using the browser need to set the blocking to aggressive.
- Load brave://settings/shields in the browser's address bar.
- Scroll down to the "Look & feel" section.
- Locate "Tackers & ads blocking" and switch it to Aggressive.
Brave Browser: content blocking changes to improve web compatibility - gHacks Tech News
The developers of the Brave Browser revealed that the browser's logic for blocking content will change in Brave Browser 1.30.
Last edited: