- Sep 3, 2017
- 825
- Content source
- https://news.drweb.com/show/?lng=en&i=12980&c=14
Doctor Web virus analysts have detected the Android.BankBot.495.origin Trojan attacking Brazilian financial institution customers on Google Play. This Trojan uses Android’s special features (Accessibility Service). It uses them to control infected mobile devices and steal their owners’ confidential data.
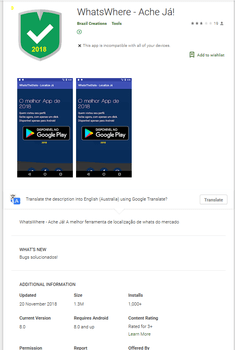
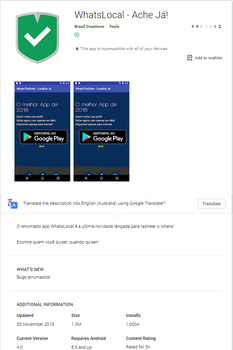
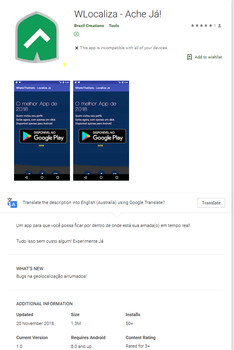
Cybercriminals were distributing Android.BankBot.495.origin under the guise of applications that supposedly allow you to monitor Android-based smartphone and tablet users. The Trojan was hidden in the following software: WLocaliza Ache Já, WhatsWhere Ache Já, and WhatsLocal Ache Já. After Doctor Web’s experts informed Google, the company promptly removed the programs from Google Play. The Trojan was downloaded by more than 2,000 users.
When launched, Android.BankBot.495.origin attempts to gain Android Accessibility features by opening system settings and prompting the user to activate the Accessibility option. If a potential victim agrees to grant the Trojan privileges, Android.BankBot.495.origin will be able to control the programs in the background, tap buttons, and steal the contents of the active application windows.

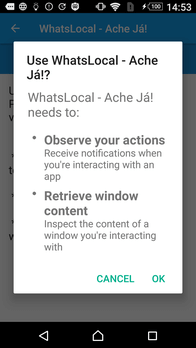
When the user permits the Trojan to access accessibility features, it closes the window, starts the malicious service, and uses it to continue operating in the background. Android.BankBot.495.origin then requests access to display screens over running programs. This option will later be needed to display phishing windows. The previously obtained permission to use the accessibility features helps Android.Bank.Bot.495.origin automatically tap all buttons with the text "PERMITIR" ("Allow") that appears when requesting permissions. As a result, if the system language is Portuguese, the Trojan secures the necessary privileges by itself.
Moreover, the malware uses the special features for self-defense, tracking a number of antiviruses and utilities. When they launch, it tries to close their windows by pressing the “back" button 4 times.
Android.BankBot.495.origin connects to a remote host to accept the initial settings and follows the link given by the virus writers in an invisible WebView window. After several redirections, the Trojan receives a final link with the encrypted IP addresses of two command and control servers. Android.BankBot.495.origin then connects to one of them and accepts a list with app names. The Trojan checks whether they are installed on the device and notifies the server. The Trojan then sends several specific requests one by one. Depending on the server settings, Android.BankBot.495.origin then receives a command to start one of the apps. At the time of our analysis, it could run software of the following financial institutions: Banco Itaú S.A. and Banco Bradesco S.A., as well as the default SMS application.
When the Banco Itaú is launched, the Trojan uses the accessibility feature to read the contents of its window and transfer information on the balance of the user's bank account to the attackers. It then navigates to account management in the application, where it copies and sends the iToken key, a security code used to verify electronic transactions, to the virus writers.
Upon startup of Bradesco, the Trojan reads the victim’s account information and tries to automatically login to it by entering the PIN code received from the command and control server. Android.BankBot.495.origin copies the balance of the user's account and, together with the account information received earlier, transfers it to cybercriminals.
Upon receiving a command to launch an SMS application, the Trojan opens it, reads and saves the text of the available messages and sends them to the server. It also recognizes the messages from CaixaBank S.A. and transmits them in a separate request.
Cybercriminals also use Android.BankBot.495.origin to perform phishing attacks. The Trojan monitors the following software: Itaucard Controle seu cartão, Banco do Brasil, Banco Itaú, CAIXA, Bradesco, Uber, Netflix, and Twitter. If the Trojan detects that one of them has been launched, it displays an overlay window with a fraudulent web page simulating the attacked app, loaded from the second command and control server. The user may be prompted to enter the information on their account, bank account number, bank card details, logins, passwords, and other confidential information.
See an example of such phishing pages below:
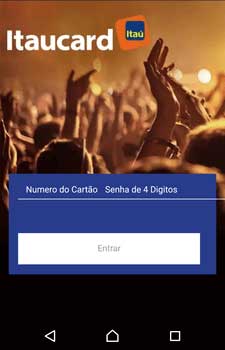
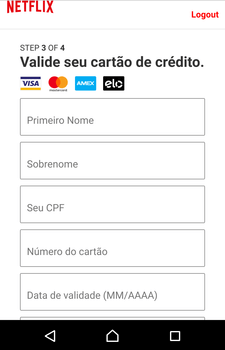
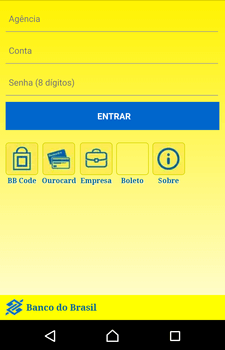
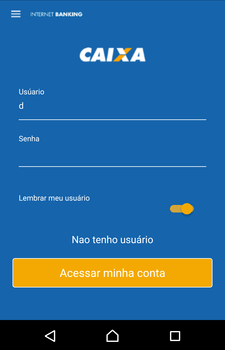
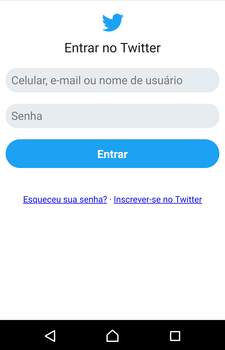
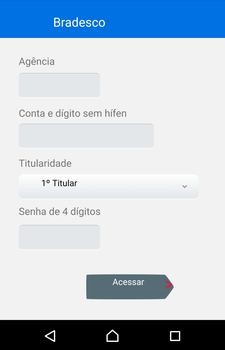
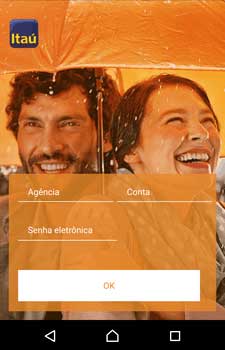
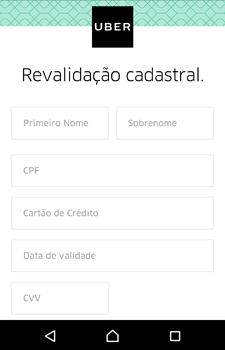
Confidential information, entered by the victim, is transmitted to the attackers, and then the Trojan closes the fraudulent window and re-launches the compromised application in order not to raise suspicion from the user for collapsing and closing the app.
Doctor Web recommends you install Android software with extra care, even if you obtain them from Google Play. Attackers can fake well-known software, as well as create seemingly harmless applications. To reduce the risk of installing a Trojan, you should pay attention to the name of the developer, the date when the app appeared on Google Play, the number of downloads, and reviews from other users. In addition, please use an antivirus.
All known modifications to the Android.BankBot.495.origin banking Trojan have been successfully detected and removed by Dr.Web for Android, so they do not pose any threat to our users.
BRIEF:
Android.BankBot.495.origin
Added to Dr.Web virus database:2018-12-07Virus description was added:2018-12-10
SHA1:
How it starts
When launched, Android.BankBot.495.origin opens system settings and prompts the user to permit it to access the Accessibility option. If a potential victim agrees to do it, the Trojan may read the contents of the active application windows and tap buttons independently of the user.


Having obtained the permissions, Android.BankBot.495.origin launches MainService and automatically closes the accessibility settings window.
Then the malware tries to obtain the privileges needed to show overlay windows and forms. For that, it requests the following permission in the system:
How initial settings are obtained
The MainService starts the Main2Activity, which loads the address http://brazilian*****.ddns.net/renew in an invisible WebView window. Next, the website executes a chain of redirections:
34.222.**.**|52.12.**.***
The first IP address belongs to a server with fraudulent web pages that the Trojan will use for phishing attacks. The second address belongs to the command and control server of the Trojan.
After successfully accepting the settings and receiving the ?finishurl key in the last link, the Trojan terminates the Main2Activity.
Receiving the commands and using accessiblity features to steal confidential data
When launched, MainService starts two permanently active threads, ProcessualThread and AppStartWatchThread. ProcessualThread sends queries to the command and control server at http://52.12.**.***/mobileConfig.php every 6 seconds and executes the commands it sends back. The process is as follows.
Data collected by the Trojan is sent to the server in the thread AppStartWatchThread, which constantly monitors the changes in the class variables. Android.BankBot.495.origin also recognizes the messages from CaixaBank S.A. and sends them to the server in a separate request.
Phishing attacks
Android.BankBot.495.origin uses the accessibility features to track the activities of the following apps:
Fraudulent input forms the Trojan can display:
Attacked application Link to the phishing page View of the fraudulent window Uber34.222.**.**/uber/load.php?hwid=********3X37a********681bf&content=d Itaucard Controle seu cartão34.222.**.**/itcard/load.php?hwid=********3X37a********681bf&content=d
Itaucard Controle seu cartão34.222.**.**/itcard/load.php?hwid=********3X37a********681bf&content=d

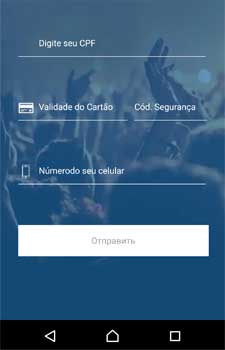 Netflix34.222.**.**/netf/load.php?hwid=********3X37a********681bf
Netflix34.222.**.**/netf/load.php?hwid=********3X37a********681bf
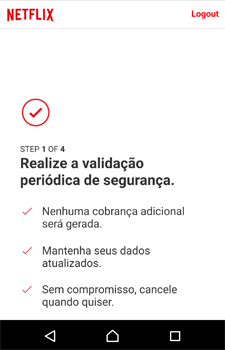
 Banco do Brasil34.222.**.**/biu/load.php?hwid=********3X37a********681bf
Banco do Brasil34.222.**.**/biu/load.php?hwid=********3X37a********681bf
 CAIXA34.222.**.**/cef/load.php?hwid=********3X37a********681bf
CAIXA34.222.**.**/cef/load.php?hwid=********3X37a********681bf
 Twitter34.222.**.**/twit/load.php?hwid=********3X37a********681bf
Twitter34.222.**.**/twit/load.php?hwid=********3X37a********681bf
 Bradesco34.222.**.**/desco/load.php?hwid=********3X37a********681bf
Bradesco34.222.**.**/desco/load.php?hwid=********3X37a********681bf
 Banco Itaú34.222.**.**/itau/load.php?hwid=********3X37a********681bf
Banco Itaú34.222.**.**/itau/load.php?hwid=********3X37a********681bf

Self-protection mechanism
Android.BankBot.495.origin has a self-defense mechanism. The Trojan controls the startup of applications and searches the package names for a match in the following lines:
Cybercriminals were distributing Android.BankBot.495.origin under the guise of applications that supposedly allow you to monitor Android-based smartphone and tablet users. The Trojan was hidden in the following software: WLocaliza Ache Já, WhatsWhere Ache Já, and WhatsLocal Ache Já. After Doctor Web’s experts informed Google, the company promptly removed the programs from Google Play. The Trojan was downloaded by more than 2,000 users.



When launched, Android.BankBot.495.origin attempts to gain Android Accessibility features by opening system settings and prompting the user to activate the Accessibility option. If a potential victim agrees to grant the Trojan privileges, Android.BankBot.495.origin will be able to control the programs in the background, tap buttons, and steal the contents of the active application windows.


When the user permits the Trojan to access accessibility features, it closes the window, starts the malicious service, and uses it to continue operating in the background. Android.BankBot.495.origin then requests access to display screens over running programs. This option will later be needed to display phishing windows. The previously obtained permission to use the accessibility features helps Android.Bank.Bot.495.origin automatically tap all buttons with the text "PERMITIR" ("Allow") that appears when requesting permissions. As a result, if the system language is Portuguese, the Trojan secures the necessary privileges by itself.
Moreover, the malware uses the special features for self-defense, tracking a number of antiviruses and utilities. When they launch, it tries to close their windows by pressing the “back" button 4 times.
Android.BankBot.495.origin connects to a remote host to accept the initial settings and follows the link given by the virus writers in an invisible WebView window. After several redirections, the Trojan receives a final link with the encrypted IP addresses of two command and control servers. Android.BankBot.495.origin then connects to one of them and accepts a list with app names. The Trojan checks whether they are installed on the device and notifies the server. The Trojan then sends several specific requests one by one. Depending on the server settings, Android.BankBot.495.origin then receives a command to start one of the apps. At the time of our analysis, it could run software of the following financial institutions: Banco Itaú S.A. and Banco Bradesco S.A., as well as the default SMS application.
When the Banco Itaú is launched, the Trojan uses the accessibility feature to read the contents of its window and transfer information on the balance of the user's bank account to the attackers. It then navigates to account management in the application, where it copies and sends the iToken key, a security code used to verify electronic transactions, to the virus writers.
Upon startup of Bradesco, the Trojan reads the victim’s account information and tries to automatically login to it by entering the PIN code received from the command and control server. Android.BankBot.495.origin copies the balance of the user's account and, together with the account information received earlier, transfers it to cybercriminals.
Upon receiving a command to launch an SMS application, the Trojan opens it, reads and saves the text of the available messages and sends them to the server. It also recognizes the messages from CaixaBank S.A. and transmits them in a separate request.
Cybercriminals also use Android.BankBot.495.origin to perform phishing attacks. The Trojan monitors the following software: Itaucard Controle seu cartão, Banco do Brasil, Banco Itaú, CAIXA, Bradesco, Uber, Netflix, and Twitter. If the Trojan detects that one of them has been launched, it displays an overlay window with a fraudulent web page simulating the attacked app, loaded from the second command and control server. The user may be prompted to enter the information on their account, bank account number, bank card details, logins, passwords, and other confidential information.
See an example of such phishing pages below:








Confidential information, entered by the victim, is transmitted to the attackers, and then the Trojan closes the fraudulent window and re-launches the compromised application in order not to raise suspicion from the user for collapsing and closing the app.
Doctor Web recommends you install Android software with extra care, even if you obtain them from Google Play. Attackers can fake well-known software, as well as create seemingly harmless applications. To reduce the risk of installing a Trojan, you should pay attention to the name of the developer, the date when the app appeared on Google Play, the number of downloads, and reviews from other users. In addition, please use an antivirus.
All known modifications to the Android.BankBot.495.origin banking Trojan have been successfully detected and removed by Dr.Web for Android, so they do not pose any threat to our users.
BRIEF:
Android.BankBot.495.origin
Added to Dr.Web virus database:2018-12-07Virus description was added:2018-12-10
SHA1:
- 6d0c88f488902d0c975167068027920ca18ff8af
- a305a0f363bc8891ca7a5ca31e20c2c01b5a6c24
- 70e39daafe8d68ec2b43b3ce7353e5364a381ba2
How it starts
When launched, Android.BankBot.495.origin opens system settings and prompts the user to permit it to access the Accessibility option. If a potential victim agrees to do it, the Trojan may read the contents of the active application windows and tap buttons independently of the user.


Having obtained the permissions, Android.BankBot.495.origin launches MainService and automatically closes the accessibility settings window.
Then the malware tries to obtain the privileges needed to show overlay windows and forms. For that, it requests the following permission in the system:
- android.permission.ACTION_MANAGE_OVERLAY_PERMISSION
How initial settings are obtained
The MainService starts the Main2Activity, which loads the address http://brazilian*****.ddns.net/renew in an invisible WebView window. Next, the website executes a chain of redirections:
- http://brazilian*****.ddns.net/renew
- http://brazilian*****.ddns.net/renew/
- http://brazilian*****.ddns.net/renew/1.php?cg=MzQuM******2LjgyfDUyLjEyL******2OA==]
- http://brazilian*****.ddns.net/renew/d.html?finishurl
34.222.**.**|52.12.**.***
The first IP address belongs to a server with fraudulent web pages that the Trojan will use for phishing attacks. The second address belongs to the command and control server of the Trojan.
After successfully accepting the settings and receiving the ?finishurl key in the last link, the Trojan terminates the Main2Activity.
Receiving the commands and using accessiblity features to steal confidential data
When launched, MainService starts two permanently active threads, ProcessualThread and AppStartWatchThread. ProcessualThread sends queries to the command and control server at http://52.12.**.***/mobileConfig.php every 6 seconds and executes the commands it sends back. The process is as follows.
- The Trojan executes a query with the parameters
hwid=********3X37a********681bf&type=1&act=firstRun (where hwid is a device identifier that contains the serial number of hardware and Settings.Secure.ANDROID_ID). In response, the Trojan receives JSON with a list of applications. Android.BankBot.495.origin checks whether these applications are installed on the mobile device and sends the result in the following query:hwid=********3X37a********681bf&ttdd=%5B%22oct2%22%5D - The Trojan executes a query with the parameters
hwid=********3X37a********681bf&operador=cfData&content=chkItTk. If the server response contains the string “mobile_ita_tk”, the Trojan launches the Banco Itaú (com.itau) application. Next, it reads the contents of its window, saves, and transmits the data on the balance of the victim’s bank account to the server. Then it taps the buttons “alterar conta”, “acessar com outra”, as well as “iToken”, by itself. After that Android.BankBot.495.origin sends the contents of the application interface element with the text “Número válido por” (the iToken key value) to the server. - The Trojan executes a query with the parameters
hwid=********3X37a********681bf&operador=cfData&content=chkDescoTk. If the server response contains the string “mobile_desco_tk”, the Trojan launches the Bradesco (com.bradesco) application and tries to enter the PIN code received in the command. Then Android.BankBot.495.origin uses the accessibility feature to analyze the contents of the app window and perform the following steps, depending on the interface element:- if the string representation contains “viewIdResName: agn”, the Trojan stores it to the Agencia variable;
- if the string representation contains “viewIdResName: ctaDig”, Android.BankBot.495.origin stores it to the Conta variable;
- if the window contains an element with the text “CHAVE DE”, and the server sends a command to launch the compromised application, the Trojan taps this element and checks the box to indicate that the button has been tapped;
- if the checkbox that corresponds to the “CHAVE DE” button is active, and the window contains an element titled “DIGITAR A SENHA”, the Trojan taps it;
- if the checkbox that corresponds to the “CHAVE DE” button is active, and the window contains an element titled “Digite seu PIN”, Android.BankBot.495.origin enter the PIN code received from the server and checks the box to confirm that password has been entered;
- if the box indicating that PIN code has successfully been entered is checked, and the element contains the description “OK”, the Trojan taps it;
- if the window element description contains the string “valorSaldoBox”, Android.BankBot.495.origin stores its value to the Saldo variable;
- if the element description contains “id/otp_field”, the Trojan stores its string representation as “Token”.
- Contents of the variables Agencia, Conta, Saldo, and Token are uploaded to the server http://52.12.**.*** in the thread AppStartWatchThread.
- Then the Trojan executes two queries:
- hwid=********3X37a********681bf&operador=cfData&content=chkSMSB;
- hwid=********3X37a********681bf&operador=cfData&content=chkSMSCf.
Data collected by the Trojan is sent to the server in the thread AppStartWatchThread, which constantly monitors the changes in the class variables. Android.BankBot.495.origin also recognizes the messages from CaixaBank S.A. and sends them to the server in a separate request.
Phishing attacks
Android.BankBot.495.origin uses the accessibility features to track the activities of the following apps:
- Itaucard Controle seu cartão;
- Banco do Brasil;
- CAIXA;
- Bradesco;
- Banco Itaú;
- Uber;
- Netflix;
- Twitter.
Fraudulent input forms the Trojan can display:
Attacked application Link to the phishing page View of the fraudulent window Uber34.222.**.**/uber/load.php?hwid=********3X37a********681bf&content=d
 Itaucard Controle seu cartão34.222.**.**/itcard/load.php?hwid=********3X37a********681bf&content=d
Itaucard Controle seu cartão34.222.**.**/itcard/load.php?hwid=********3X37a********681bf&content=d

 Netflix34.222.**.**/netf/load.php?hwid=********3X37a********681bf
Netflix34.222.**.**/netf/load.php?hwid=********3X37a********681bf

 Banco do Brasil34.222.**.**/biu/load.php?hwid=********3X37a********681bf
Banco do Brasil34.222.**.**/biu/load.php?hwid=********3X37a********681bf
 CAIXA34.222.**.**/cef/load.php?hwid=********3X37a********681bf
CAIXA34.222.**.**/cef/load.php?hwid=********3X37a********681bf
 Twitter34.222.**.**/twit/load.php?hwid=********3X37a********681bf
Twitter34.222.**.**/twit/load.php?hwid=********3X37a********681bf
 Bradesco34.222.**.**/desco/load.php?hwid=********3X37a********681bf
Bradesco34.222.**.**/desco/load.php?hwid=********3X37a********681bf
 Banco Itaú34.222.**.**/itau/load.php?hwid=********3X37a********681bf
Banco Itaú34.222.**.**/itau/load.php?hwid=********3X37a********681bf

Self-protection mechanism
Android.BankBot.495.origin has a self-defense mechanism. The Trojan controls the startup of applications and searches the package names for a match in the following lines:
- com.vtm.uninstall
- com.ddm.smartappunsintaller
- com.rhythm.hexise.uninst
- com.GoodTools.Uninstalle
- mobi.infolife.uninstaller
- om.utils.uninstalle
- com.jumobile.manager.systemapp
- com.vsrevogroup.revouninstallermobi
- oo.util.uninstall
- om.barto.uninstalle
- om.tohsoft.easyuninstalle
- vast.android.mobile
- avast.android.cleane
- om.antiviru
- om.avira.andro
- om.kms.fre
