Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,818
This is a short fact sheet for our Business Main-Test Series, containing the results of the Business Malware Protection Test (March) and Business Real-World Protection Test (March-April). The full report, including the Performance Test and product reviews, will be released in July.
To be certified in July 2023 as an “Approved Business Product” by AV-Comparatives, the tested products must score at least 90% in the Malware Protection Test, with zero false alarms on common business software, and an FP rate on non-business files below the Remarkably High threshold. Additionally, products must score at least 90% in the overall Real-World Protection Test (i.e. over the course of four months), with less than fifty false alarms on any clean software/websites, and zero false alarms on common business software. Tested products must also avoid major performance issues (impact score must be below 40) and have fixed all reported bugs in order to gain certification.
Please note that the results of the Business Main-Test Series cannot be compared with the results of the Consumer Main-Test Series, as the tests are done at different times, with different sets, different settings, etc.
Tested Products
The following products were tested under Windows 10 64-bit and are included in this factsheet:
Settings
Bitdefender: “Sandbox Analyzer” (for Applications and Documents) enabled. “Analysis mode” set to “Monitoring”. “Scan SSL” enabled for HTTP and RDP. “HyperDetect” and “Device Control” disabled. “Update ring” changed to “Fast ring”. “Web Traffic Scan” and “Email Traffic Scan” enabled for Incoming emails (POP3). “Ransomware Mitigation” enabled. “Process memory Scan” for “On-Access scanning” enabled. All “AMSI Command-Line Scanner” settings enabled for “Fileless Attack Protection”.
Cisco: “On Execute File and Process Scan” set to Active; “Exploit Prevention: Script Control” set to “Block”; “TETRA Deep Scan File” disabled; “Exclusions” set to “Microsoft Windows Default”; Engines “ETHIS”, “ETHOS”, “SPERO” and “Step-Up” disabled. “MaxScanFileSize” increased to 500 MB.
CrowdStrike: everything enabled and set to maximum, i.e. “Extra Aggressive”. “On-demand Scans” and Uploading of “Unknown Detection-Related Executables” and “Unknown Executables” disabled.
Cybereason: “Anti-Malware” enabled; “Signatures mode” set to “Quarantine”; “Artificial intelligence” set to “Moderate”; “Fileless protection” enabled and set to “Prevent”; Update interval set to 1 minute.
Elastic: MalwareScore (“windows.advanced.malware.threshold”) set to “aggressive”, and Rollback-SelfHealing (“windows.advanced.alerts.rollback.self_healing.enabled”) enabled. “Credential hardening” enabled.
ESET: All “Real-Time & Machine Learning Protection” settings set to “Aggressive”.
G Data: “BEAST Behavior Monitoring” set to “Halt program and move to quarantine”. “BEST Automatic Whitelisting” deactivated. “G DATA WebProtection” add-on for Google Chrome installed and activated. “Malware Information Initiative” enabled.
Kaspersky: “Adaptive Anomaly Control” disabled; “Detect other software that can be used by criminals to damage your computer or personal data” enabled;
Microsoft: “CloudExtendedTimeOut” set to 55; “PuaMode” enabled.
Sophos: “Threat Graph creation”, “Web Control” and “Event logging” disabled.
Trellix: “Web Control” add-on for Google Chrome enabled. “Firewall” and “Exploit Prevention” disabled.
VIPRE: “IDS” enabled and set to “Block With Notify”. “Firewall” enabled.
VMware: policy set to “Advanced”.
Avast, K7, WatchGuard: default settings.
Test Results
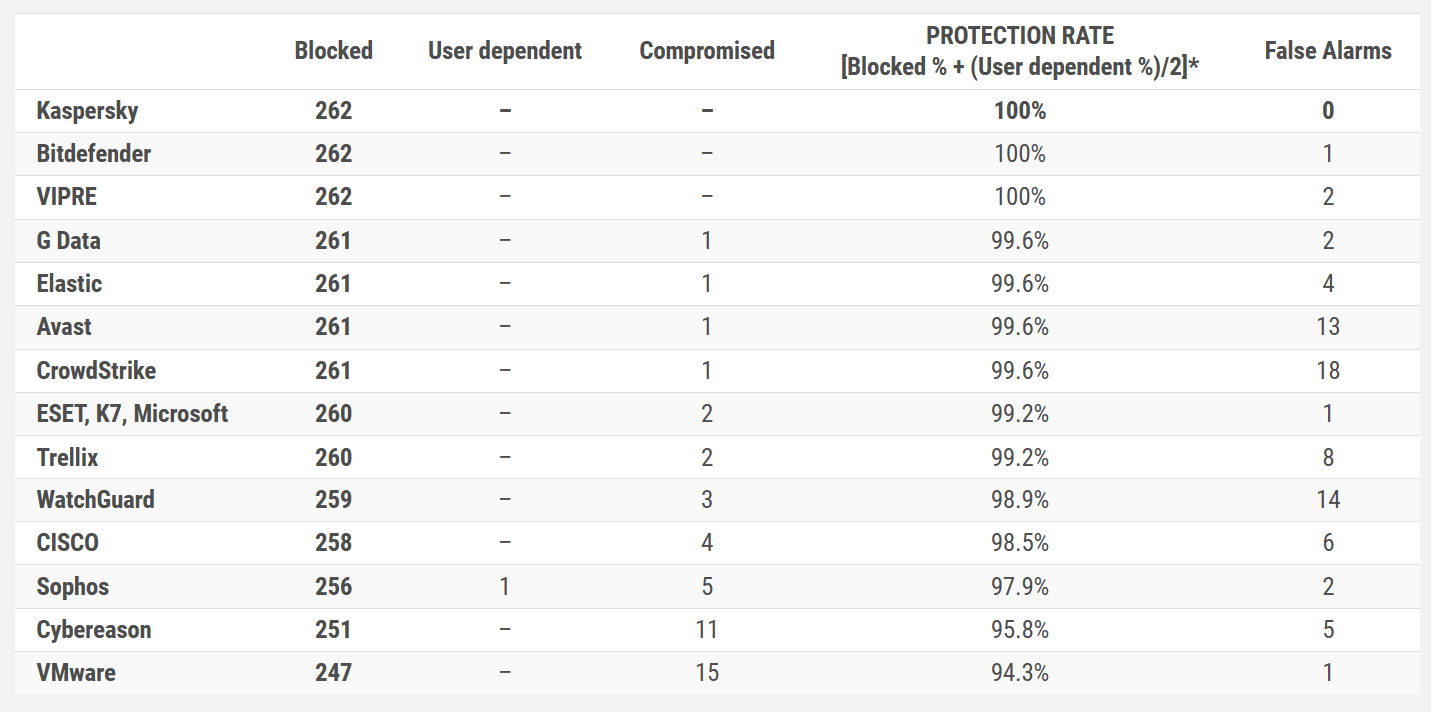
Real-World Protection Test (March-April)
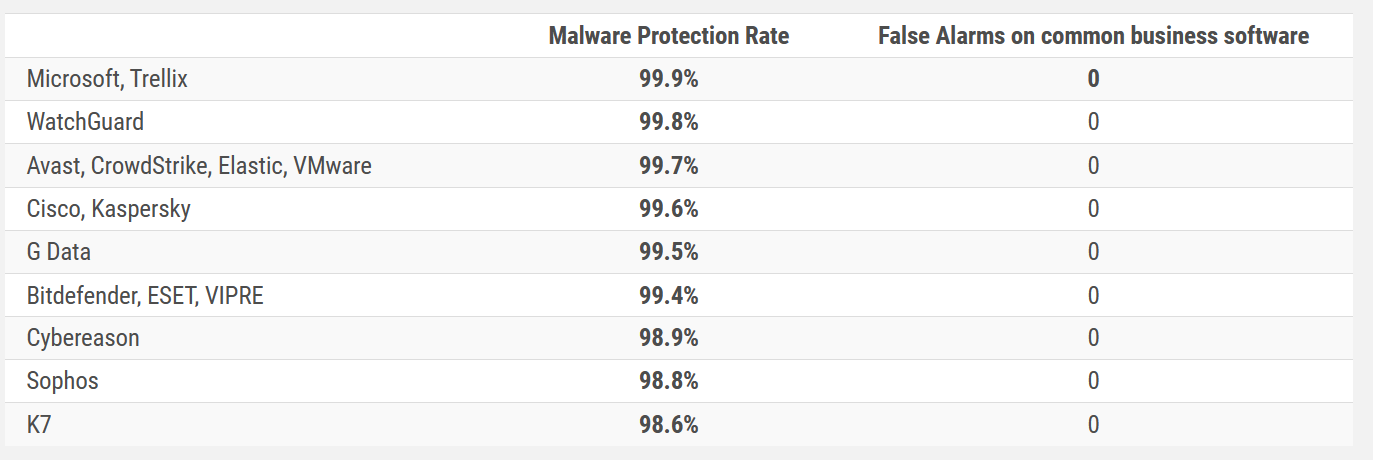
Malware Protection Test (March)

Business Security Test March-April 2023 - Factsheet
The Business Security Test March-April 2023 - Factsheet covering results of our Enterprise main-test series has been released.
 www.av-comparatives.org
www.av-comparatives.org

