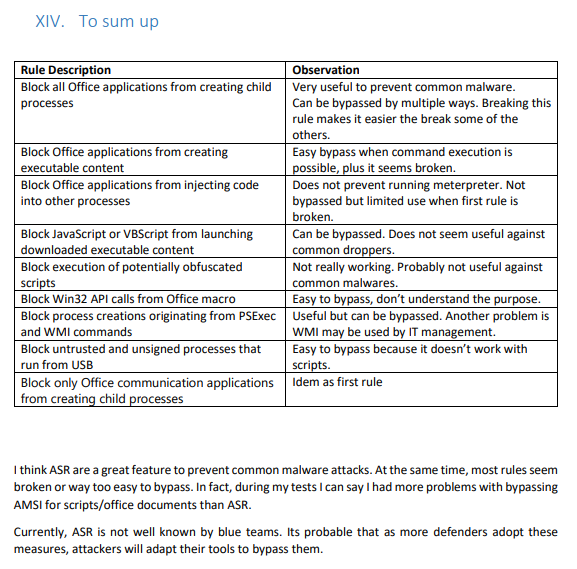
Looks like all the Windows Defender ASR mitigations have been bypassed in this test one way or another ☹
This is disappointing and shows that Microsoft needs to step up and patch this loopholes.
The test was done in February 2019 so don't know if Microsoft has fixed this issues by now or not
Read the full report here
This is disappointing and shows that Microsoft needs to step up and patch this loopholes.
The test was done in February 2019 so don't know if Microsoft has fixed this issues by now or not
Read the full report here




