N
NullByte
Thread author
Hi
I will talk about how easy is to bypass most security software and how you can protect yourself. The first thing is Digital Signature and then how to use delays to bypass different features.
If you search a little you can find tools that will copy the digital signature from a file to another. This is used with Backdoors (Remote Access Tools) and Botnets. If you like to download cracks or other "hacking tools" you may had this type of infection.
In this example I used FTB Launcher (a game) that doesn't have and Digital signature and I copied the Digital Signature from Comodo Internet Security.
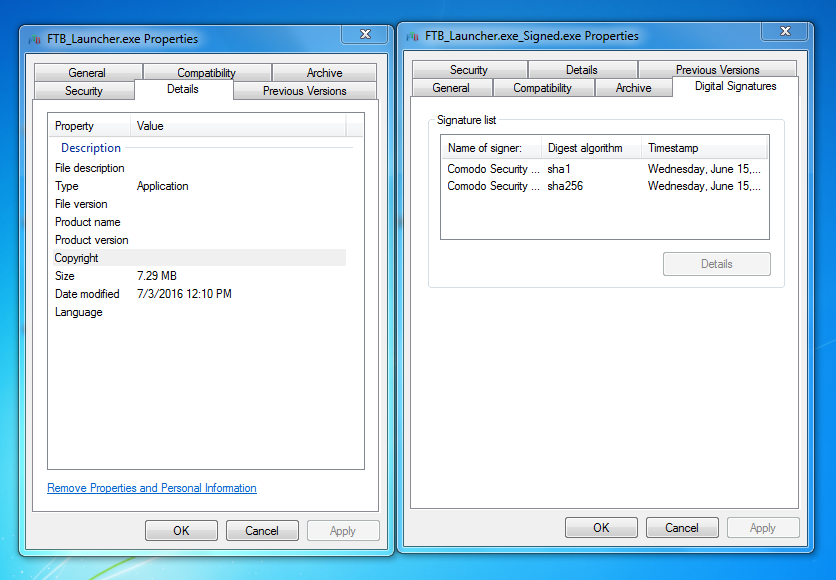
As you can see in the screenshot, it copied the SHA1 and the SHA256. The issue with Digital Signed files is that, there are a lot of security products that will not scan the file if the sample is "Signed" by a trusted company.
Products like HitmanPro (not the HitmanPro.Alert), Zemana, Reason and most Cloud AVs will not scan it or even if they scan it, they will look at the PE Header and see it "clean".
If you also use EXE Protectior, DE EVO, CodeLux Protector and other tools that will "protect" the code, you will have almost 100% chance that the file will bypass your security software.
Info: Most PUP/Adware are signed software that is why its so hard to detect them. Also, if you sign your malware with a driver signature you will have a higher chance of success.
Now, it comes to a the second part, delaying payload and using safe (clean files) to drop the payload.
As I said in the first part, signing malware is really easy (if you have the tools), if you also add a delay to the payload (more then 30 seconds) you will bypass the security software and there is a high chance that your security software will not say anything.
I will talk about the new epic Avast (this works with most security products too).
I've notice how Avast works and if you add more then 30 seconds delay the sample will infect the PC. How it works is like this: When you execute a new file avast will use DeepScreen and the new CyberCapture to get it, if the file is digital signed and you execute the avast will start looking at the file and since the "timeout is 25 seconds" and the payload will drop after 30 seconds the "online" analysis will say it's clean. If you have HIPS set on default (level 1) the sample will bypass with not warning, if you have it on high (level 3) the HIPS will ask you when the backdoor will auto-start.
The third part is using the first and the second techniques and inject the file in a safe file. This technique is very good because it uses all what I said above and a clean file.
In conclusion, if your security product doesn't check the files just uses VirusTotal or other services then there is a high chance that you will get infected.
This is just a short post about some techniques, if you like it I will make more. If you have any questions feel free to post below or send me a PM. If you work for a security company and you are interested in the tools send me a PM
I will talk about how easy is to bypass most security software and how you can protect yourself. The first thing is Digital Signature and then how to use delays to bypass different features.
If you search a little you can find tools that will copy the digital signature from a file to another. This is used with Backdoors (Remote Access Tools) and Botnets. If you like to download cracks or other "hacking tools" you may had this type of infection.
In this example I used FTB Launcher (a game) that doesn't have and Digital signature and I copied the Digital Signature from Comodo Internet Security.
As you can see in the screenshot, it copied the SHA1 and the SHA256. The issue with Digital Signed files is that, there are a lot of security products that will not scan the file if the sample is "Signed" by a trusted company.
Products like HitmanPro (not the HitmanPro.Alert), Zemana, Reason and most Cloud AVs will not scan it or even if they scan it, they will look at the PE Header and see it "clean".
If you also use EXE Protectior, DE EVO, CodeLux Protector and other tools that will "protect" the code, you will have almost 100% chance that the file will bypass your security software.
Info: Most PUP/Adware are signed software that is why its so hard to detect them. Also, if you sign your malware with a driver signature you will have a higher chance of success.
Now, it comes to a the second part, delaying payload and using safe (clean files) to drop the payload.
As I said in the first part, signing malware is really easy (if you have the tools), if you also add a delay to the payload (more then 30 seconds) you will bypass the security software and there is a high chance that your security software will not say anything.
I will talk about the new epic Avast (this works with most security products too).
I've notice how Avast works and if you add more then 30 seconds delay the sample will infect the PC. How it works is like this: When you execute a new file avast will use DeepScreen and the new CyberCapture to get it, if the file is digital signed and you execute the avast will start looking at the file and since the "timeout is 25 seconds" and the payload will drop after 30 seconds the "online" analysis will say it's clean. If you have HIPS set on default (level 1) the sample will bypass with not warning, if you have it on high (level 3) the HIPS will ask you when the backdoor will auto-start.
The third part is using the first and the second techniques and inject the file in a safe file. This technique is very good because it uses all what I said above and a clean file.
In conclusion, if your security product doesn't check the files just uses VirusTotal or other services then there is a high chance that you will get infected.
This is just a short post about some techniques, if you like it I will make more. If you have any questions feel free to post below or send me a PM. If you work for a security company and you are interested in the tools send me a PM