- Jul 16, 2014
- 215
CCleaner Malware: Here is the Full List of Affected Companies !

Last week news came out that CCleaner software was infected with a backdoor. An initial investigation showed it was a state-sponsored attack. Now, Avast has finally revealed the complete list of organizations affected by the second stage CCleaner malware in its newest update published last Friday.
The company has been busy in investigating the issue of the presence of malware in its very popular and widely used CCleaner tool. The list was compiled after the company discovered a second server database, which was used by the malware in CCleaner to send information to attackers about the infected hosts.
Avast has narrated the details of the attack in its official blog post that reads:
“Analysis of the CnC server showed that the incident was, in fact, an Advanced Persistent Threat (APT) attack, targeting specific high-tech and telecommunications companies. That is, despite the fact that CCleaner is a consumer product, the purpose of the attack was not to attack consumers and their data; instead, the CCleaner customers were used to gain access to corporate networks of select large enterprises.”
Initially, Avast claimed that the incident happened because one of the servers ran out of disk space on Sep 10, due to which the operator had to rebuild the database fully. However, latest report uploaded on 25 Sep., Avast’s Threats Labs Team explained that after further investigation it was learned that the attackers managed to back up the data from the crashed C&C server to a second server before rebuilding the database. The investigation was conducted by the Threat Labs team from Avast and US law enforcement officials collectively.
The blog post noted that the IP address of the second server was identified to be 216.126.225.163. This server featured the same self-signed SSL certificate and had a usual LAMP configuration (CentOS release 6.9 with Apache 2.2.15, PHP 5.3.3) stack-wise. Avast further revealed that a MySql database was containing the data from August 18. When the backup server was accessed, the complete database was found but only the data between 2017-09-10 19:03:18 and 2017-09-12 9:58:47 UTC was missing. This refers to the timeline between the crashing of the original C&C database and the creation of the new database. However, it is not yet clear how the C&C server behaved during this period.
According to the findings, there were approx. 5,686,677 connections linked with the C&C server while the number of unique MAC addresses communicating with the C&C server was 1,646,536. The second-stage payload was delivered to 40 unique PCs.
It was also noted that the server’s database only contained information about user infections that occurred between 12 Sep and 16 Sep after which the hackers installed another server, which was seized by Avast on 15 Sep.
This refers to the fact that Avast and law enforcement has obtained the full list of infected hosts apart from the 40 hour period including the affected PCs with the first and second stage payloads. The infected version of CCleaner was downloaded by more than 2.27 million users out of which only 40 PCs were delivered the second-stage malware, claimed Avast. This, however, contradicts the company’s previous statement and that of investigation firm Cisco, which claimed that 20 PCs were affected with second-stage malware.
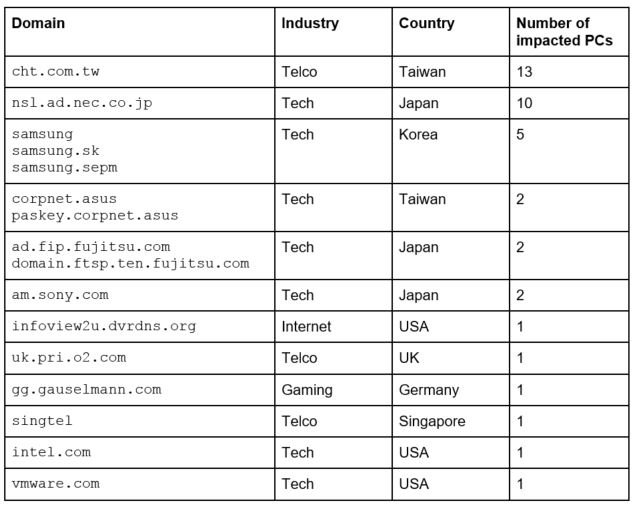
The table shows the complete list of infected hosts:
As apparent, the most infected bots are 13 computers located on the network of Taiwan based ISP Chunghwa Telecom and the company ranked second on the list with ten computers is a Japan-based IT firm NEC while the third on the list is Samsung with five computers.
The companies having two computers infected with the second-stage malware include ASUS, Sony and Fujitsu and one infected computer was identified on the networks of Singtel, IPAddress.com, VMWare, Intel, and O2. It must be noted that the table shown above provides a list of successful infections only because despite the efforts of C&C server to target specific networks, not all of them were affected.
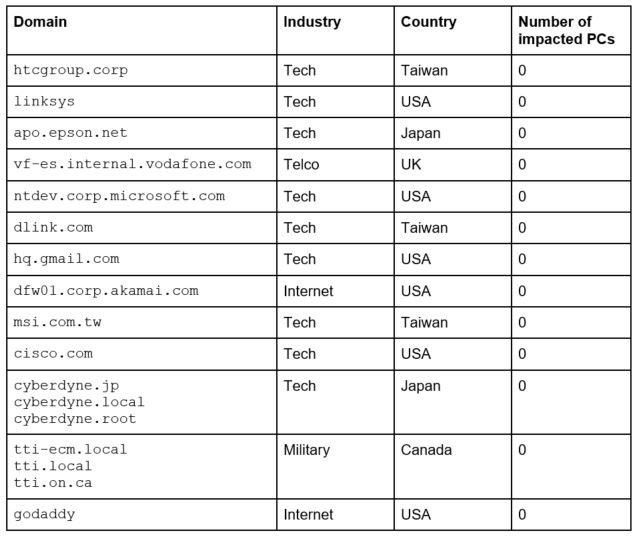
The filtering rules for the seized server depicted that companies like HTC, Microsoft, Google, Samsung, Intel, Sony, VMWare, Vodafone, O2, Epson, Linksys, Oracle, DLink, Singtel, and Gauselmann. The backup server’s filtering rules showed that before Sep 10, the attackers targeted different companies like Microsoft, Akamai, Linksys, HTC, Epson, MSI, Tactical technologies INC., GoDaddy, Cyberdyne, Cisco, Gmail, Vodafone, and DLink. Researchers believe that this filter server was the only one used by attackers while creating a backup and between August 15 and September 10.
Credit: Avast
Credit: Avast
As far as the origin of hackers is concerned, Avast claims that it has solid evidence such as the PHP code on the C&C server, myPhpAdmin logs and some code snippets, which suggests the involvement of China’s Axiom APT.
Bleeping Computer reported that security firm Kaspersky Lab and Cisco last week. Furthermore, Avast also claims that the logins and login activity patterns on the two servers point out to a person residing in the Eastern Russia, India and China timezones. Avast also adheres that these indications can be easily forged to make investigations difficult and avoid detection of the true origin of the hackers.
MORE: CCleaner Malware: Here is the Full List of Affected Companies

Last week news came out that CCleaner software was infected with a backdoor. An initial investigation showed it was a state-sponsored attack. Now, Avast has finally revealed the complete list of organizations affected by the second stage CCleaner malware in its newest update published last Friday.
The company has been busy in investigating the issue of the presence of malware in its very popular and widely used CCleaner tool. The list was compiled after the company discovered a second server database, which was used by the malware in CCleaner to send information to attackers about the infected hosts.
Avast has narrated the details of the attack in its official blog post that reads:
“Analysis of the CnC server showed that the incident was, in fact, an Advanced Persistent Threat (APT) attack, targeting specific high-tech and telecommunications companies. That is, despite the fact that CCleaner is a consumer product, the purpose of the attack was not to attack consumers and their data; instead, the CCleaner customers were used to gain access to corporate networks of select large enterprises.”
Initially, Avast claimed that the incident happened because one of the servers ran out of disk space on Sep 10, due to which the operator had to rebuild the database fully. However, latest report uploaded on 25 Sep., Avast’s Threats Labs Team explained that after further investigation it was learned that the attackers managed to back up the data from the crashed C&C server to a second server before rebuilding the database. The investigation was conducted by the Threat Labs team from Avast and US law enforcement officials collectively.
The blog post noted that the IP address of the second server was identified to be 216.126.225.163. This server featured the same self-signed SSL certificate and had a usual LAMP configuration (CentOS release 6.9 with Apache 2.2.15, PHP 5.3.3) stack-wise. Avast further revealed that a MySql database was containing the data from August 18. When the backup server was accessed, the complete database was found but only the data between 2017-09-10 19:03:18 and 2017-09-12 9:58:47 UTC was missing. This refers to the timeline between the crashing of the original C&C database and the creation of the new database. However, it is not yet clear how the C&C server behaved during this period.
According to the findings, there were approx. 5,686,677 connections linked with the C&C server while the number of unique MAC addresses communicating with the C&C server was 1,646,536. The second-stage payload was delivered to 40 unique PCs.
It was also noted that the server’s database only contained information about user infections that occurred between 12 Sep and 16 Sep after which the hackers installed another server, which was seized by Avast on 15 Sep.
This refers to the fact that Avast and law enforcement has obtained the full list of infected hosts apart from the 40 hour period including the affected PCs with the first and second stage payloads. The infected version of CCleaner was downloaded by more than 2.27 million users out of which only 40 PCs were delivered the second-stage malware, claimed Avast. This, however, contradicts the company’s previous statement and that of investigation firm Cisco, which claimed that 20 PCs were affected with second-stage malware.
The table shows the complete list of infected hosts:
As apparent, the most infected bots are 13 computers located on the network of Taiwan based ISP Chunghwa Telecom and the company ranked second on the list with ten computers is a Japan-based IT firm NEC while the third on the list is Samsung with five computers.
The companies having two computers infected with the second-stage malware include ASUS, Sony and Fujitsu and one infected computer was identified on the networks of Singtel, IPAddress.com, VMWare, Intel, and O2. It must be noted that the table shown above provides a list of successful infections only because despite the efforts of C&C server to target specific networks, not all of them were affected.
The filtering rules for the seized server depicted that companies like HTC, Microsoft, Google, Samsung, Intel, Sony, VMWare, Vodafone, O2, Epson, Linksys, Oracle, DLink, Singtel, and Gauselmann. The backup server’s filtering rules showed that before Sep 10, the attackers targeted different companies like Microsoft, Akamai, Linksys, HTC, Epson, MSI, Tactical technologies INC., GoDaddy, Cyberdyne, Cisco, Gmail, Vodafone, and DLink. Researchers believe that this filter server was the only one used by attackers while creating a backup and between August 15 and September 10.

Credit: Avast

Credit: Avast
As far as the origin of hackers is concerned, Avast claims that it has solid evidence such as the PHP code on the C&C server, myPhpAdmin logs and some code snippets, which suggests the involvement of China’s Axiom APT.
Bleeping Computer reported that security firm Kaspersky Lab and Cisco last week. Furthermore, Avast also claims that the logins and login activity patterns on the two servers point out to a person residing in the Eastern Russia, India and China timezones. Avast also adheres that these indications can be easily forged to make investigations difficult and avoid detection of the true origin of the hackers.
MORE: CCleaner Malware: Here is the Full List of Affected Companies

