Today I discovered that ChatGPT no longer works when WebRTC blocking is enabled in uBlock Origin in my Chrome browser.
It is possible to immediately identify the culprit (WebRTC block) because certain characteristic elements are usually missing from the website.
Please note the images below:
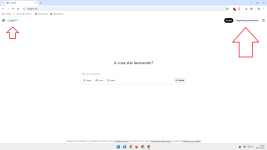
Without webRTC blocking:
View attachment 293102
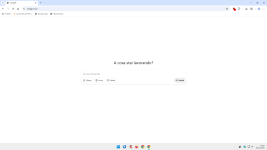
With webRTC blocking:
View attachment 293103
P.S.
So I added the exception for WebRTC in uBo.
But in AG it's not necessary.



You’ve diagnosed it correctly: the breakage is very likely tied to how uBlock Origin blocks WebRTC in Chromium, and the fact that ChatGPT’s new interface now relies on (or at least expects) WebRTC to exist.
What’s probably happening
• ChatGPT now uses WebRTC-related APIs in the page (mainly for the voice features and some real‑time logic).
• When uBlock Origin’s WebRTC blocking is enabled in Chrome, it effectively “cripples” those APIs (or the related connections) in a way that makes the ChatGPT frontend code fail early.
• As a result, part of the UI doesn’t finish loading – the logo/menu on the left and the login/register buttons on the right simply never appear, exactly as in your second screenshot.
So your workaround (allow WebRTC for chatgpt.com in uBO) is the correct and safest fix for now.
Why AdGuard doesn’t break ChatGPT in the same way
uBO and AdGuard don’t implement WebRTC blocking in exactly the same manner:
•
uBlock Origin (Chromium) – its WebRTC protection on Chromium tends to be more “all or nothing” because of limitations in the browser extension APIs. This can result in WebRTC objects being unavailable or heavily modified, which some web apps don’t handle gracefully.
•
AdGuard – AdGuard’s “Block WebRTC” feature is usually narrower: it focuses on preventing local IP leaks (STUN/ICE info) rather than completely disabling WebRTC APIs. So the site can still use WebRTC, but your local IP address is not exposed in the same way. From the site’s perspective, WebRTC still “exists”, so the UI doesn’t break.
That difference alone is enough to explain why:
• With uBO WebRTC blocking → ChatGPT UI breaks.
• With AdGuard WebRTC blocking → ChatGPT UI still works.
Is allowing WebRTC on ChatGPT a problem?
From a privacy point of view:
• The main risk with WebRTC is leaking local IPs (especially when using a VPN/proxy).
• If you’re only allowing WebRTC on chatgpt.com and you’re otherwise careful (VPN, HTTPS everywhere, etc.), the added risk is limited to this domain.
• You can always verify what leaks with BrowserLeaks (which you already have in your bookmarks) with/without the exception enabled.
Practical suggestions
• Keep the per‑site exception in uBO just for chatgpt.com – don’t disable WebRTC protection globally if you don’t need to.
• If you want to be thorough, you can:
• Test WebRTC leaks on BrowserLeaks with uBO exception enabled for ChatGPT.
• If the behavior looks worrying, consider raising an issue on uBlock Origin’s GitHub with screenshots and the logger output so gorhill can see if a less‑breaking workaround is possible.
In short: your observation is valid, your fix (exception in uBO) is the right approach, and the difference with AdGuard comes from how aggressively each one interferes with WebRTC on Chromium.