silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,176
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that's designed to load Cobalt Strike onto infected machines.
Dubbed SILKLOADER by Finnish cybersecurity company WithSecure, the malware leverages DLL side-loading techniques to deliver the commercial adversary simulation software.
The development comes as improved detection capabilities against Cobalt Strike, a legitimate post-exploitation tool used for red team operations, is forcing threat actors to seek alternative options or concoct new ways to propagate the framework to evade detection.
"The most common of these include adding complexity to the auto-generated beacon or stager payloads via the utilization of packers, crypters, loaders, or similar techniques," WithSecure researchers said.
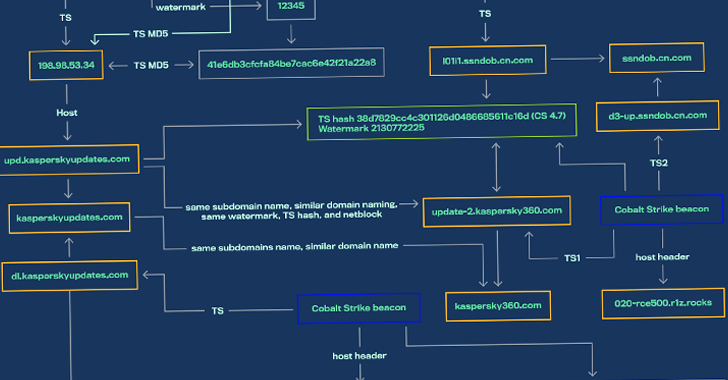
Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection
Threat actors from Chinese and Russian cybercriminal ecosystems have been observed using a new malware designed to load Cobalt Strike.
