- Mar 12, 2024
- 63
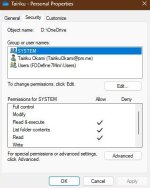
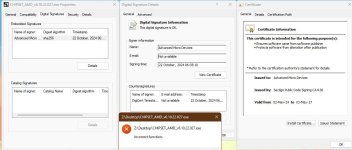
Check it out:
The video has subtitles in English, Spanish, German and Thai.
Ps.: Sorry the delay in bringing the video here and with subtitles. Life is crazy lately...
Edit.: The thumb says: Reliable Ransomware.
The video has subtitles in English, Spanish, German and Thai.
Ps.: Sorry the delay in bringing the video here and with subtitles. Life is crazy lately...
Edit.: The thumb says: Reliable Ransomware.