Hi Everyone:
Has/have you heard about Crypt0L0cker, thread on:
http://www.bleepingcomputer.com/forums/t/574608/crypt0l0cker-support-topic/
There is a new ransomware out called Crypt0L0cker (the OHs are replaced with ZEROs). This ransomware appears to be a direct descendant of TorrentLocker, with the only known difference at this point being how it targets files for encryption. It is currently being distributed via email campaigns claiming to be government notices such as speeding violations. Once a user is infected the ransom will be set at approximately 2 bitcoins. This infection is targeting almost all countries other than the United States. Computers using an United States IP address will not become infected at this time.
In the past TorrentLocker would target only certain file types for encryption. Crypt0L0cker on the hand uses an exclude list that contains only a few file types. This exclude list is:
avi,wav,mp3,gif,ico,png,bmp,txt,html,inf,manifest,chm,ini,tmp,log,url,lnk,cmd,bat,scr,msi,sys,dll,exe
Known Command & Control Servers and associated IP addresses:
62.173.145.212 tidisow . ru
62.173.145.212 lepodick . ru
We will be using this topic to support this ransomware and to post new analysis as it comes in.
Screenshots:
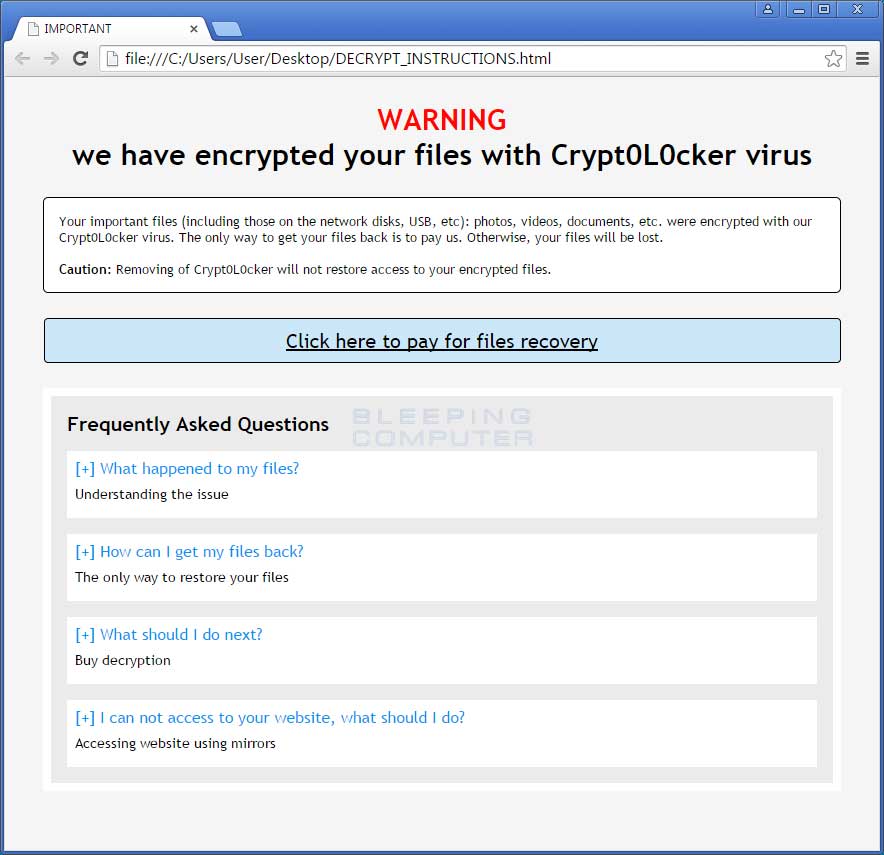
DECRYPT_INSTRUCTIONS.HTML
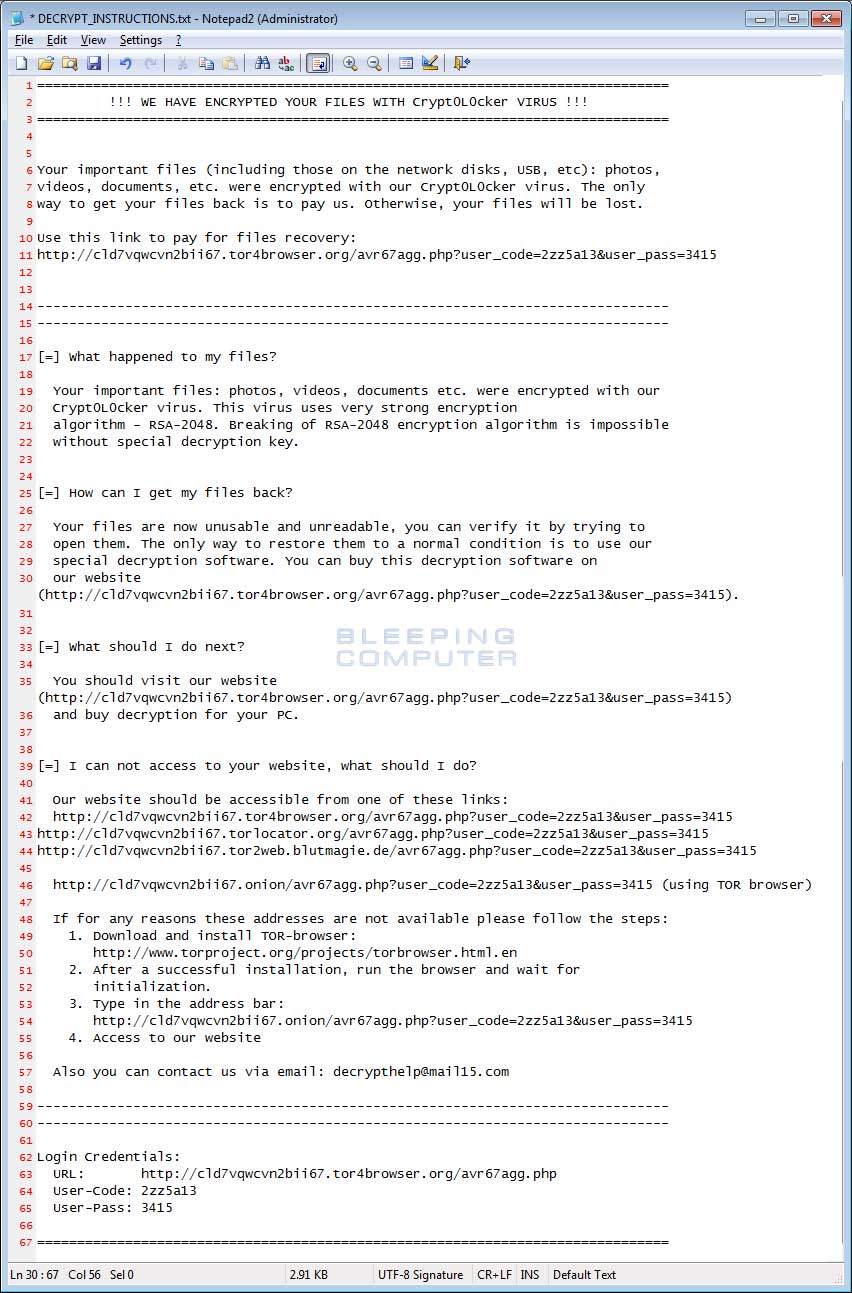
DECRYPT_INSTRUCTIONS.TXT
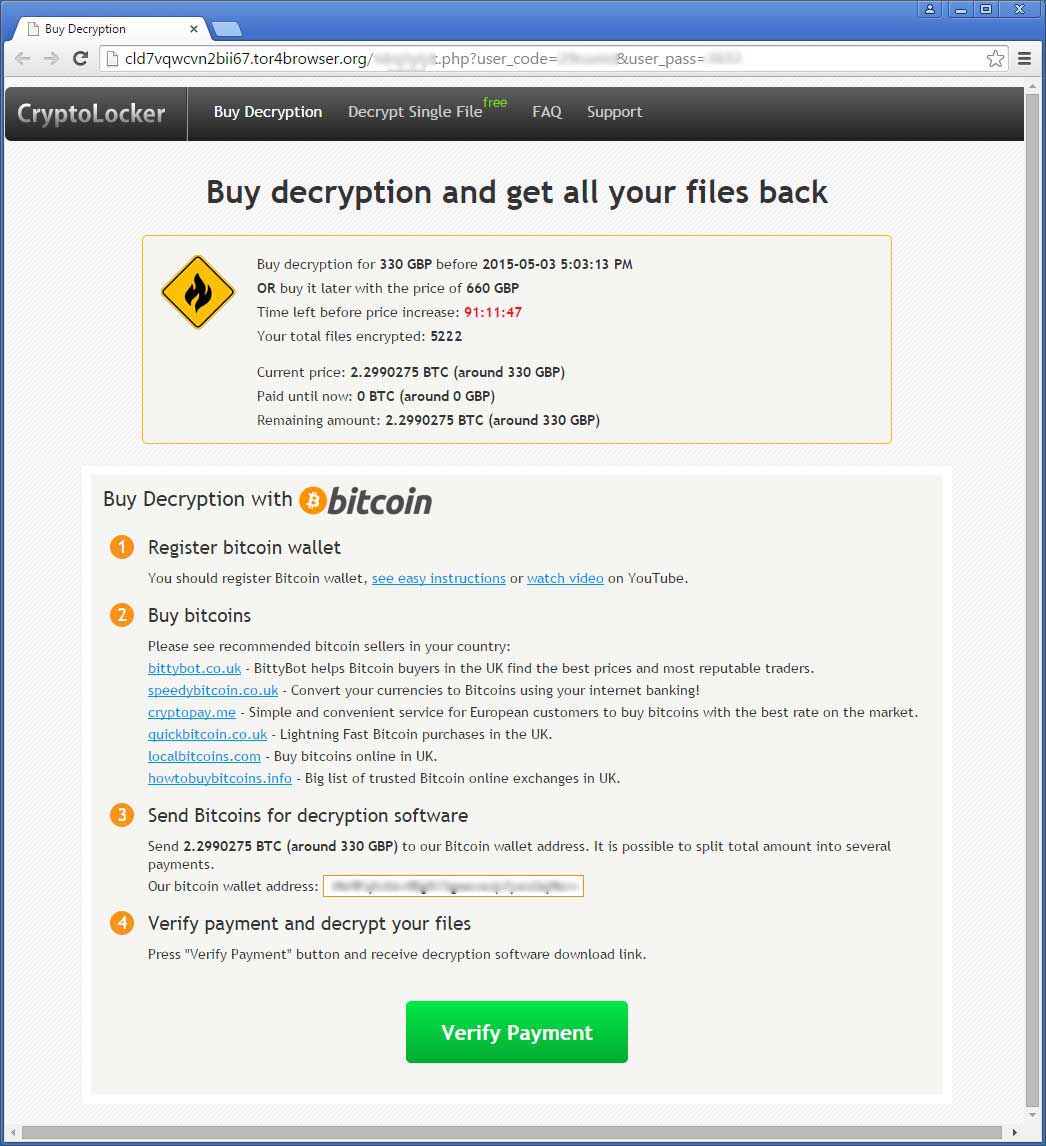
Decryption Site Buy Decryption Page
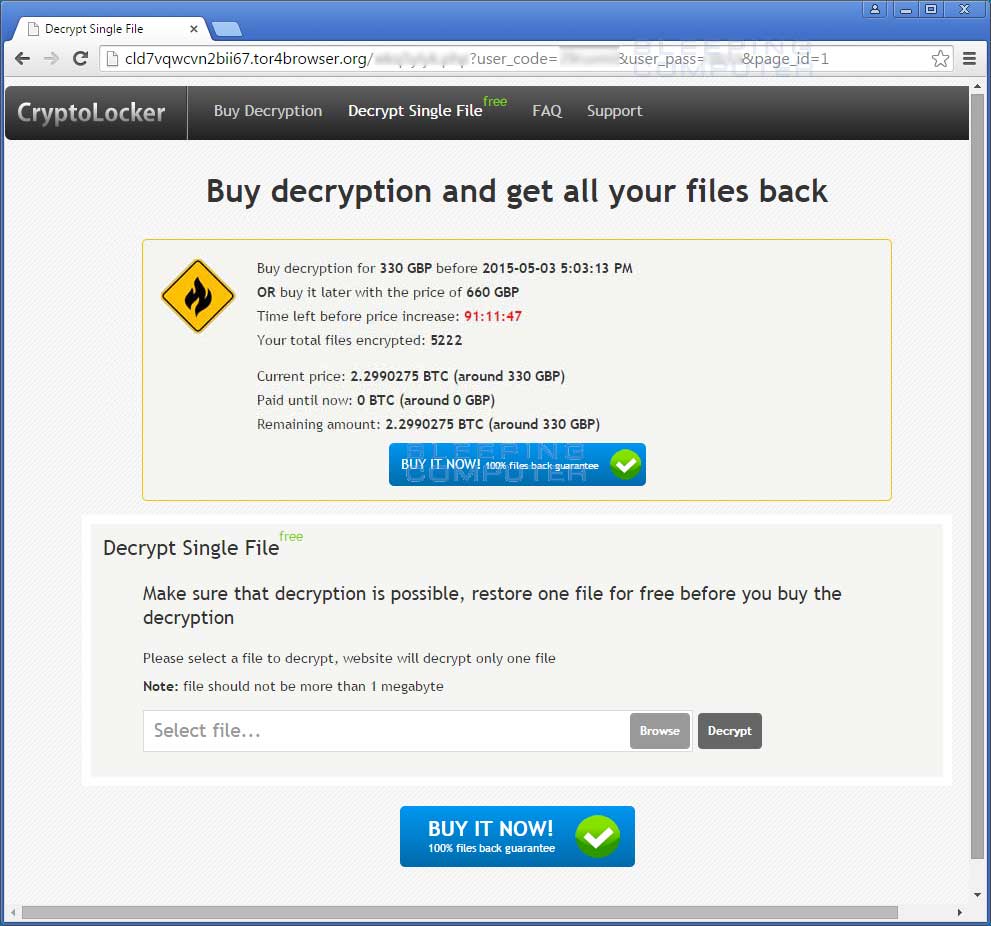
Decryption Site One Free Decryption Page
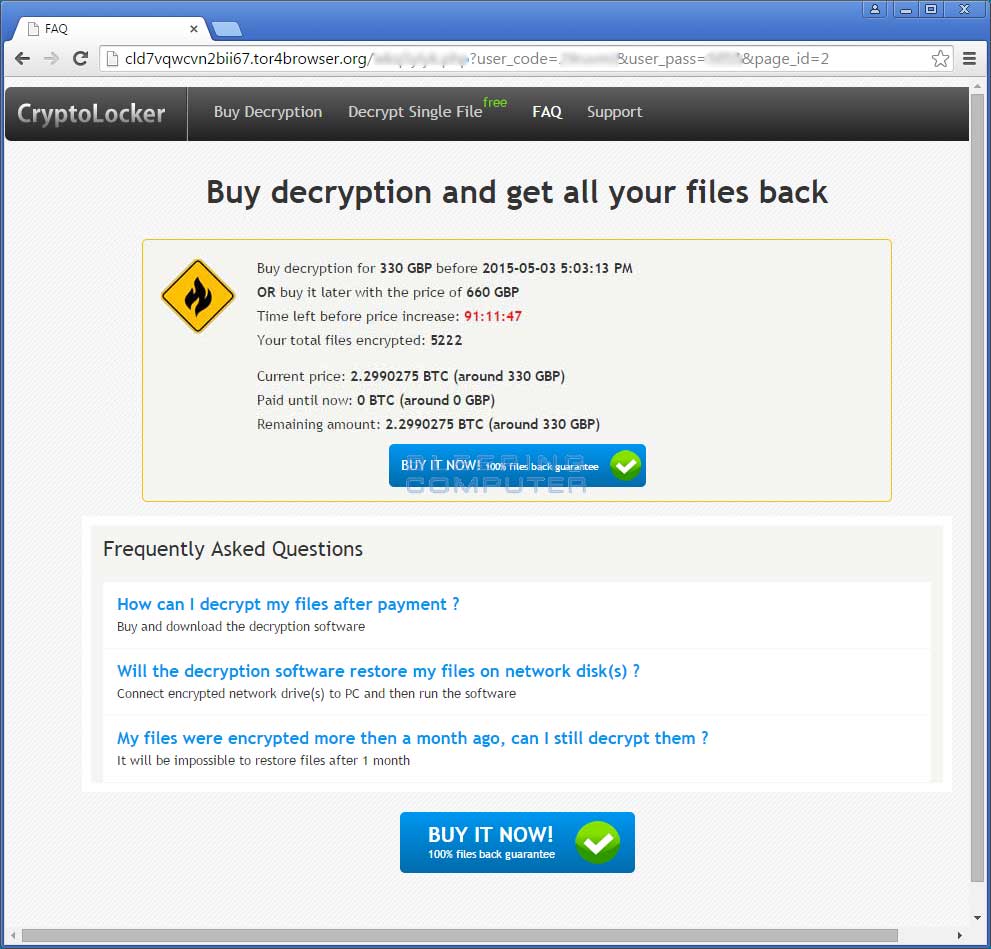
Decryption Site FAQ Page
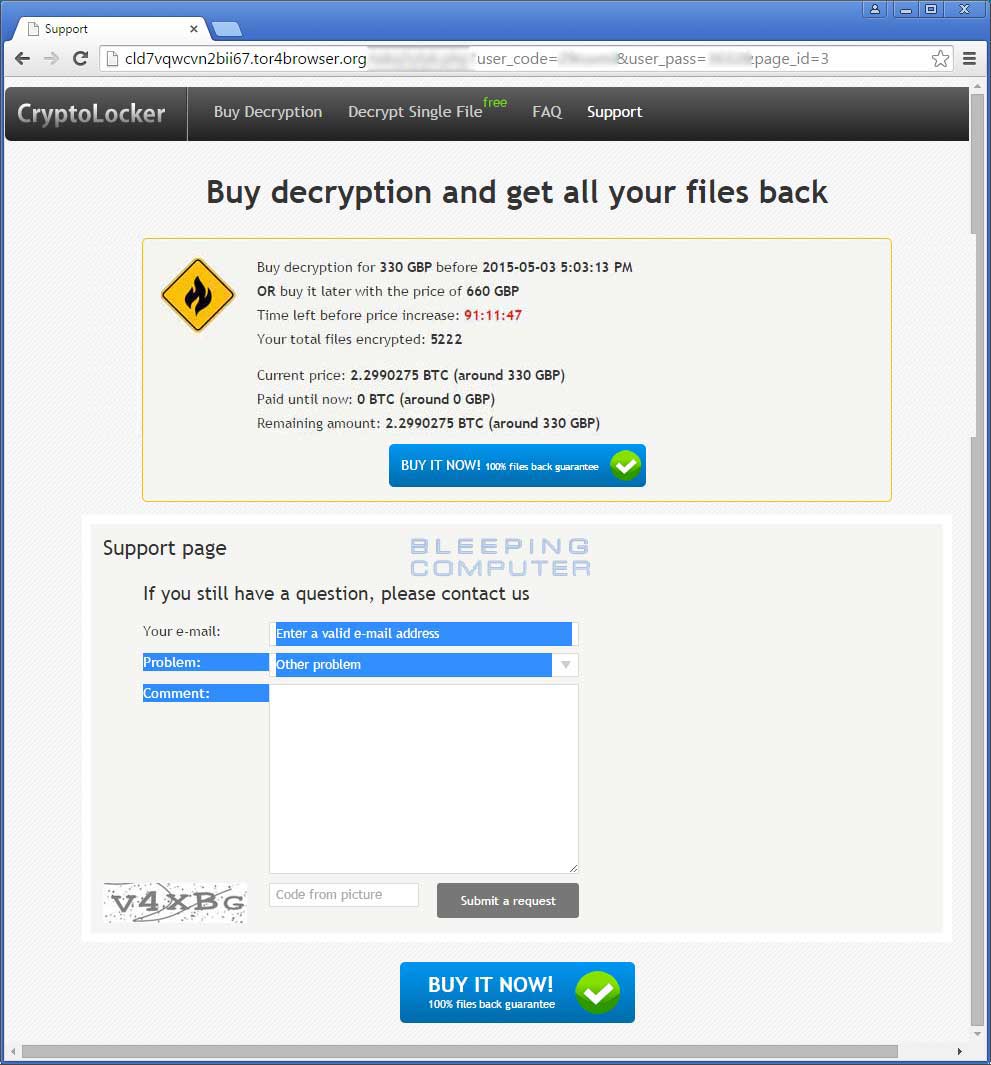
Decryption Site Support Page
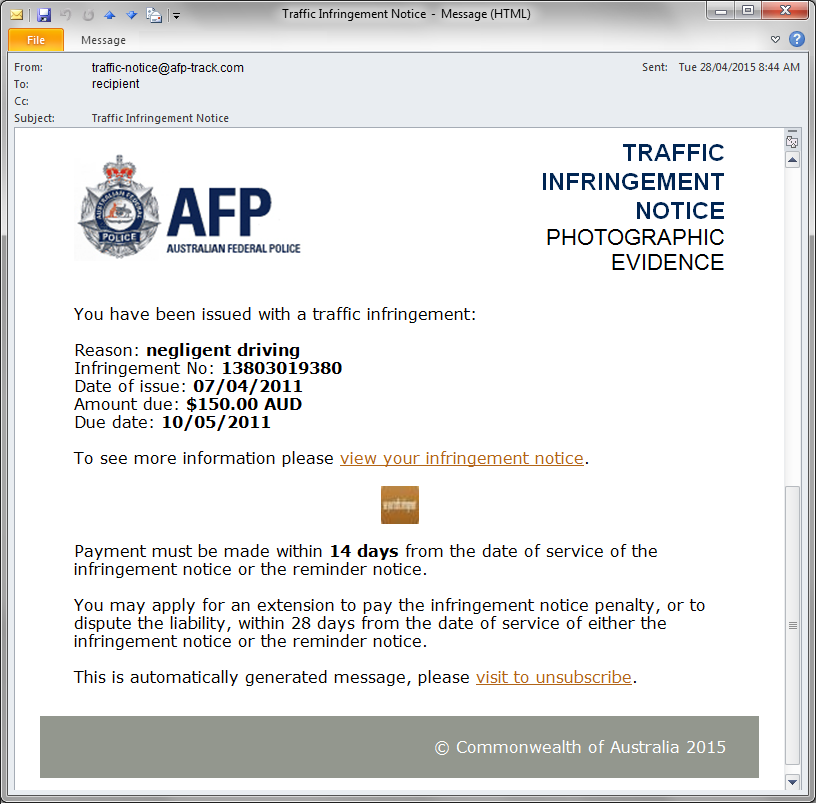
Has/have you heard about Crypt0L0cker, thread on:
http://www.bleepingcomputer.com/forums/t/574608/crypt0l0cker-support-topic/
There is a new ransomware out called Crypt0L0cker (the OHs are replaced with ZEROs). This ransomware appears to be a direct descendant of TorrentLocker, with the only known difference at this point being how it targets files for encryption. It is currently being distributed via email campaigns claiming to be government notices such as speeding violations. Once a user is infected the ransom will be set at approximately 2 bitcoins. This infection is targeting almost all countries other than the United States. Computers using an United States IP address will not become infected at this time.
In the past TorrentLocker would target only certain file types for encryption. Crypt0L0cker on the hand uses an exclude list that contains only a few file types. This exclude list is:
avi,wav,mp3,gif,ico,png,bmp,txt,html,inf,manifest,chm,ini,tmp,log,url,lnk,cmd,bat,scr,msi,sys,dll,exe
Known Command & Control Servers and associated IP addresses:
62.173.145.212 tidisow . ru
62.173.145.212 lepodick . ru
We will be using this topic to support this ransomware and to post new analysis as it comes in.
Screenshots:

DECRYPT_INSTRUCTIONS.HTML

DECRYPT_INSTRUCTIONS.TXT

Decryption Site Buy Decryption Page

Decryption Site One Free Decryption Page

Decryption Site FAQ Page

Decryption Site Support Page
