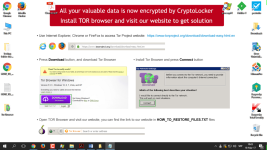
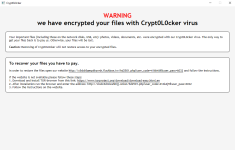
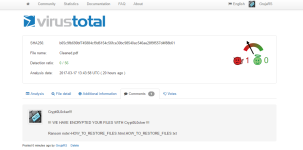
CryptOLOcker Ransomware - Demonstration of attack
- Thread starter GrujaRS
- Start date
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
You may also like...
-
Unknown ransomware - .dthnrHygS extension (Session messenger note)
- Started by matei33m
- Replies: 9
-
iDefender Pro (Présentation & Reviews)
- Started by Shadowra
- Replies: 8
-
-
-
Video... Windows Hardening Guide 2025 Edition
- Started by annaegorov
- Replies: 3