- Oct 23, 2012
- 12,527
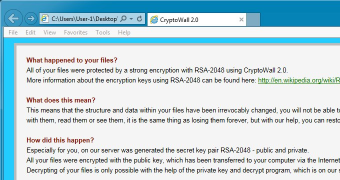
Malware authors have officially updated CryptoWall, as version 2.0 has been spotted in the wild, using Tor anonymous network to establish a connection with the command and control server.
Although samples of the crypto-malware using Tor have been observed by security researchers a while back, they still had the 1.0 mark. The Tor component was not built into the crypto-malware, but downloaded as an encrypted binary from compromised websites.
Modified version 1.0 of the threat could have been a test build
Recently, a sample was caught that uses the ransom message to explicitly inform the owner of a compromised computer that their data has been locked with CryptoWall 2.0; Tor communication is used in this one, too.
Security experts believe that the modified version 1.0 of the malware was nothing but a way to test the new capabilities of the threat before deploying it to unsuspected users.
If this is true, the behavior of the crooks is similar to regular software developers who test their products on a smaller audience before releasing them to the general public.
CryptoWall 2.0 has more anti-analysis tricks
According to Malware-Traffic-Analysis.net, the new release of the crypto-malware is distributed through fake emails from IRS claiming to be a reply to an alleged complaint sent by the potential victim.
While analyzing the fresh variant, F-Secure has noticed that it includes a new packer/obfuscator that integrates a larger number of methods designed to prevent debugging and analysis.
“Perhaps it was the efforts of security researchers to shut down CryptoWall C&C servers that was hurting the gangs business. Or maybe they just felt it was time for change. In any case the author(s) clearly felt a new C&C communication method was needed,” F-Secure says.
But regardless of the reason behind the creation of the new version, researchers believe that plenty more of CryptoWall 2.0 is to be expected in the near future.
A sample from this malware family has been used recently in a malvertising campaign conducted over top-ranked websites. The novelty factor was that the threat was signed with a digital certificate released just hours before the campaign started.
The malicious advertisements were delivered through the Zedo network on websites like hindustantimes[.]com, bollywoodhungama[.]com, one[.]co[.]il, codingforums[.]com, and mawdoo3[.]com.
Initially, the sample went undetected by the antivirus engines on VirusTotal; later on, detection became available, and currently, 29 out of 52 engines are capable of identifying the threat.
Crypto-malware is particularly frequent in Australia, where it is generally distributed through emails claiming to be from local companies.

Although samples of the crypto-malware using Tor have been observed by security researchers a while back, they still had the 1.0 mark. The Tor component was not built into the crypto-malware, but downloaded as an encrypted binary from compromised websites.
Modified version 1.0 of the threat could have been a test build
Recently, a sample was caught that uses the ransom message to explicitly inform the owner of a compromised computer that their data has been locked with CryptoWall 2.0; Tor communication is used in this one, too.
Security experts believe that the modified version 1.0 of the malware was nothing but a way to test the new capabilities of the threat before deploying it to unsuspected users.
If this is true, the behavior of the crooks is similar to regular software developers who test their products on a smaller audience before releasing them to the general public.
CryptoWall 2.0 has more anti-analysis tricks
According to Malware-Traffic-Analysis.net, the new release of the crypto-malware is distributed through fake emails from IRS claiming to be a reply to an alleged complaint sent by the potential victim.
While analyzing the fresh variant, F-Secure has noticed that it includes a new packer/obfuscator that integrates a larger number of methods designed to prevent debugging and analysis.
“Perhaps it was the efforts of security researchers to shut down CryptoWall C&C servers that was hurting the gangs business. Or maybe they just felt it was time for change. In any case the author(s) clearly felt a new C&C communication method was needed,” F-Secure says.
But regardless of the reason behind the creation of the new version, researchers believe that plenty more of CryptoWall 2.0 is to be expected in the near future.
A sample from this malware family has been used recently in a malvertising campaign conducted over top-ranked websites. The novelty factor was that the threat was signed with a digital certificate released just hours before the campaign started.
The malicious advertisements were delivered through the Zedo network on websites like hindustantimes[.]com, bollywoodhungama[.]com, one[.]co[.]il, codingforums[.]com, and mawdoo3[.]com.
Initially, the sample went undetected by the antivirus engines on VirusTotal; later on, detection became available, and currently, 29 out of 52 engines are capable of identifying the threat.
Crypto-malware is particularly frequent in Australia, where it is generally distributed through emails claiming to be from local companies.