A
Alkajak
Thread author
Introduction
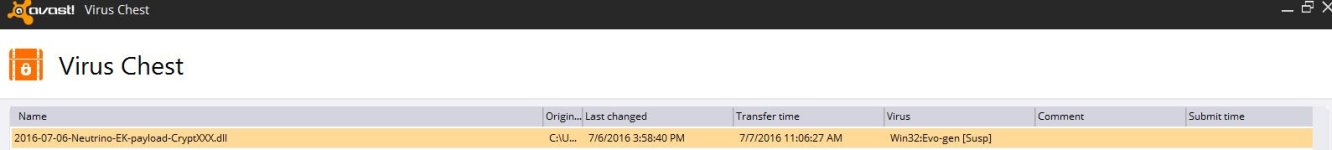
When generating exploit kit (EK) traffic earlier today, I noticed a change in post-infection activity on a Windows host infected with CryptXXX ransomware. This happened after an infection caused by Neutrino EK triggered from the pseudoDarkleech campaign.
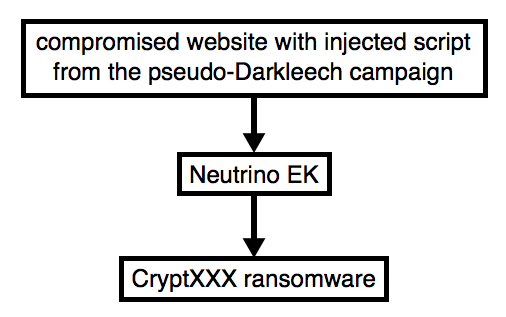
Shown above: Flow chart for Neutrino EK/CryptXXX caused by pseudoDarkleech.
This morning, the decryption instructions for CryptXXX ransomware looked different. A closer examination indicates CryptXXX has been updated. As I write this, I haven't found anything online yet describing these recent changes, so this diary takes a quick look at the traffic.
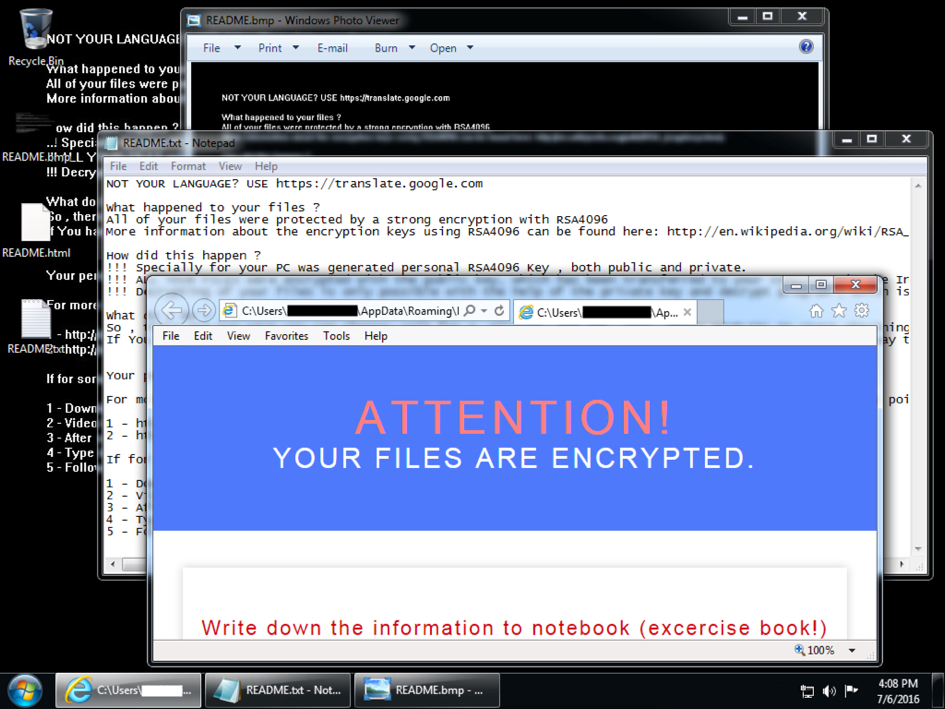
Shown above: An infected Windows desktop from earlier today.
Details
Today's EK traffic was on 198.71.54.211 using the same domain shadowing technique we've seen before from various campaigns using Neutrino EK (formerly using Angler EK [1, 2,3] before Angler disappeared). Post-infection traffic was over 91.220.131.147 on TCP port 443 using custom encoding, a method CryptXXX has used since it first appeared earlier this year [4].
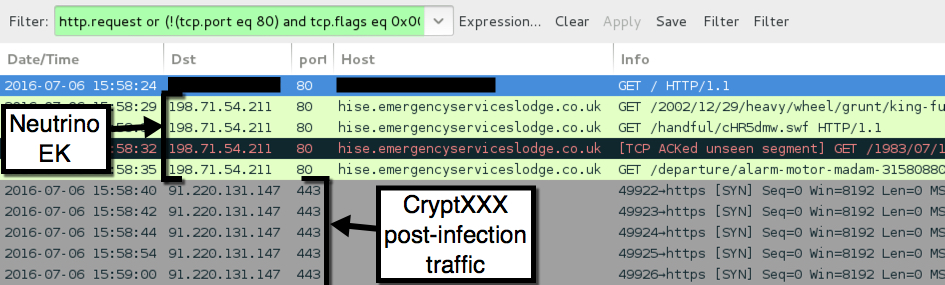
Shown above: Traffic from today's Neutrino EK/CryptXXX infection filtered in Wireshark.
In a change of behavior, text and HTML files for the CryptXXX decryption instructions are downloaded in the clear during the post-infection traffic.
Final words
Although I haven't noticed anything yet, I'm sure some of the usual sources will have a more in-depth article on these recent changes in CryptXXX ransomware. This diary is just meant to give everyone a heads-up.
Source: CryptXXX ransomware updated - SANS Internet Storm Center
*Users are reporting that the updated CryptXXX no longer adds extensions to encrypted files.
When generating exploit kit (EK) traffic earlier today, I noticed a change in post-infection activity on a Windows host infected with CryptXXX ransomware. This happened after an infection caused by Neutrino EK triggered from the pseudoDarkleech campaign.

Shown above: Flow chart for Neutrino EK/CryptXXX caused by pseudoDarkleech.
This morning, the decryption instructions for CryptXXX ransomware looked different. A closer examination indicates CryptXXX has been updated. As I write this, I haven't found anything online yet describing these recent changes, so this diary takes a quick look at the traffic.

Shown above: An infected Windows desktop from earlier today.
Details
Today's EK traffic was on 198.71.54.211 using the same domain shadowing technique we've seen before from various campaigns using Neutrino EK (formerly using Angler EK [1, 2,3] before Angler disappeared). Post-infection traffic was over 91.220.131.147 on TCP port 443 using custom encoding, a method CryptXXX has used since it first appeared earlier this year [4].

Shown above: Traffic from today's Neutrino EK/CryptXXX infection filtered in Wireshark.
In a change of behavior, text and HTML files for the CryptXXX decryption instructions are downloaded in the clear during the post-infection traffic.
Final words
Although I haven't noticed anything yet, I'm sure some of the usual sources will have a more in-depth article on these recent changes in CryptXXX ransomware. This diary is just meant to give everyone a heads-up.
Source: CryptXXX ransomware updated - SANS Internet Storm Center
*Users are reporting that the updated CryptXXX no longer adds extensions to encrypted files.