silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,176
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign.
Earth Kitsune, active since at least 2019, is known to primarily target individuals interested in North Korea with self-developed malware such as dneSpy and agfSpy. Previously documented intrusions have entailed the use of watering holes that leverage browser exploits in Google Chrome and Internet Explorer to activate the infection chain.
The differentiating factor in the latest attacks is a shift to social engineering to trick users into visiting compromised websites related to North Korea, according to a new report from Trend Micro released last week.
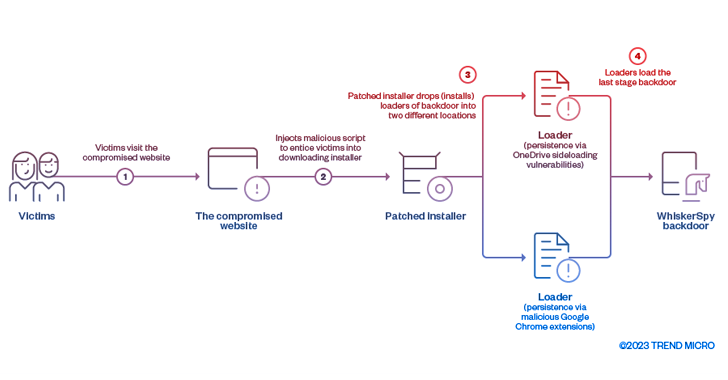
The cybersecurity company said the website of an unnamed pro-North Korean organization was hacked and modified to distribute the WhiskerSpy implant. The compromise was discovered at the end of last year.
"When a targeted visitor tries to watch videos on the website, a malicious script injected by the attacker displays a message prompt notifying the victims with a video codec error to entice them to download and install a trojanized codec installer," researchers Joseph C Chen and Jaromir Horejsi said.

Cyber Espionage Group Earth Kitsune Deploys WhiskerSpy Backdoor in Latest Attacks
North Korean group hacked a pro-North Korean organization's website and distributed their latest backdoor, WhiskerSpy, to unsuspecting visitors.
