Interesting
Source: SE Labs
Download PDF: https://selabs.uk/download/enterprise/march-2018-pmr.pdf
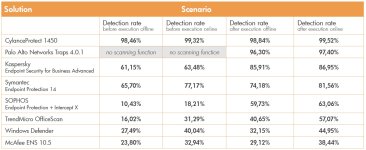
This test was designed to examine Cylance's claim that the Artificial Intelligence (AI) technology at the heart of its endpoint protection product is self-contained, in terms of being effective without relying on regular updates or cloud queries. It was also intended to determine whether or not an AI model created some months and even years in the past could identify and handle threats that subsequently attacked systems on the internet. Predictive Advantage (PA) is the time difference between the creation of the model and the first time a threat is seen by victims and security companies protecting those victims. Out of 45 threats, 43 were detected and prevented from compromising the system with an average PA of 25 months. The threats used in the test were 4. Conclusions discovered in the wild at dates ranging from 11 months to two years and nine months (33 months) after the creation of the AI model. Not only does the data demonstrate that CylancePROTECT (agent v1300, model May 2015) was capable of preventing threats that did not exist at the time the AI model was 'trained', but it provides an insight into how far ahead in time it could be effective without new knowledge. In practical terms, this indicates that regular updates to the product are not always needed, although we would expect Cylance to develop and deploy newly-trained models over time, simply because product development is an ongoing process and machine learning continues to take into account new threats to predict future ones.
Source: SE Labs
Download PDF: https://selabs.uk/download/enterprise/march-2018-pmr.pdf
This test was designed to examine Cylance's claim that the Artificial Intelligence (AI) technology at the heart of its endpoint protection product is self-contained, in terms of being effective without relying on regular updates or cloud queries. It was also intended to determine whether or not an AI model created some months and even years in the past could identify and handle threats that subsequently attacked systems on the internet. Predictive Advantage (PA) is the time difference between the creation of the model and the first time a threat is seen by victims and security companies protecting those victims. Out of 45 threats, 43 were detected and prevented from compromising the system with an average PA of 25 months. The threats used in the test were 4. Conclusions discovered in the wild at dates ranging from 11 months to two years and nine months (33 months) after the creation of the AI model. Not only does the data demonstrate that CylancePROTECT (agent v1300, model May 2015) was capable of preventing threats that did not exist at the time the AI model was 'trained', but it provides an insight into how far ahead in time it could be effective without new knowledge. In practical terms, this indicates that regular updates to the product are not always needed, although we would expect Cylance to develop and deploy newly-trained models over time, simply because product development is an ongoing process and machine learning continues to take into account new threats to predict future ones.
Attachments
Last edited by a moderator: