How DeepGuard work
When DeepGuard detects a program attempting to make potentially harmful changes to the system, it allows the program to run in a safe-zone, unless you have specifically allowed or blocked the program.
In the safe-zone, the program cannot harm your computer. DeepGuard analyzes what changes the program tried to make, and based on this, decides how likely the program is to be malware .
DeepGuard automatically either allows or blocks the program, or asks you whether to allow or block the program, depending on:
- how likely the program is to be malware , and
- which action you have told DeepGuard to take when it detects a potentially harmful attempt to change the system.
This whitepaper was last time updated 13 June 2016.
Full source : http://bit.do/f-secure-deepguard-whitepaper
Quote : " This whitepaper explains the trends and developments in computing that have made host-based behavioral analysis and exploit interception necessary elements of computer security and provides an overview of the technology and methodology used by DeepGuard, the Host-based Intrusion Prevention System (HIPS) of F-Secure’s security products. DeepGuard offers dynamic proactive behavioral analysis technology that efficiently identifies and intercepts malicious behavior. When used in tandem with other components of a multi-layered security approach, DeepGuard provides lightweight and comprehensive endpoint protection with minimal impact to the user experience. "
" The purpose of this document is to help customers better understand how F-Secure products function, and the benefits F-Secure DeepGuard provides. This document is not designed to be a legally binding agreement that defines the content of products and services provided by F-Secure Corporation. y F-Secure DeepGuard, as with any of our other products and services, is a constantly evolving set of software, systems and processes. "
" Ideally, protection should begin even before the machine environment is reached "
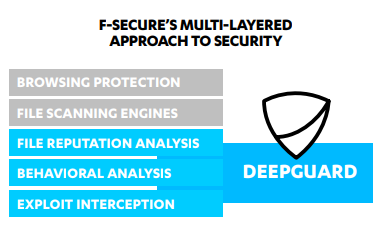
" Whenever a file arrives on a machine, is installed or modified, it is first scanned using a file scanning engine to determine if it is a known threat. File scanning engines use custom, family, generic and heuristic detections, which respectively identify specific malware, families of malware with similar features, and broad ranges of malicious physical features and behavior patterns. If the file’s characteristics match those of previously seen malware, it is blocked. Though often overlooked in favor of more sophisticated technology, file scanning engines are still an effective method of identifying and blocking the vast majority of malware seen to date, protecting users against lingering threats such as Downadup[3] or Sality[4], which debuted and peaked years ago but are still present in the wild, where they continue to infect new victims. If the file isn’t identified as a known threat, a query is sent to F-Secure’s cloud infrastructure to gather the latest metadata available for the file. Analysis is subsequently handled by DeepGuard, which collectively handles all the behavioral analysis, process monitoring and exploit interception of suspect files, both at the point of application launch and during execution. "
" Given the short-lived nature of most malware variants, the detections created for file scanning approaches tend to lose effectiveness rather quickly. In contrast, behavioral detections can effectively identify malware over a much longer time period, as malware behavior is much less mutable. DeepGuard observes an application’s behavior and prevents any potentially harmful action from successfully completing. The apparently simple nature of this task belies its importance however, as this proactive, on-thefly monitoring and interception serves as the final and most critical line of defense against new threats, even those targeting previously unknown vulnerabilities. Behavior-based analysis addresses the Achilles’ heel of file scanning approaches: the need for analysts to have an actual sample of the malware in order to create the signature to identify it. Given the huge numbers of malware constantly being created and distributed, new samples must be acquired and analyzed prior to detections being created. Prevalence logic increases effectiveness against rare files Enhanced protection against exploit-based attacks Performance and precision improvements Behavior-based detections cover that crucial gap between the first appearance of new malware and a detection being issued for the threat. By moving the focus from structural to functional characteristics of a sample, DeepGuard can identify and block programs performing harmful actions, even before an actual sample has been acquired and examined. For example, in April 2016, DeepGuard detected and blocked files that attempted to encrypt stored files. Subsequently, signature databases were updated to flag these files (chart above) as Locky ransomware, but for users facing new threats, DeepGuard’s proactive analysis provided immediate protection against infection. In 2011, an entirely rewritten DeepGuard engine was introduced that included (among numerous other improvements) a switch from using hard-coded scanning logic to an updateable detections database. F-Secure Labs analysts constantly monitor the threat landscape and analyze the latest threats to determine the best way to identify malicious behavior. Being able to update the engine with the results of this research keeps DeepGuard consistently effective against the latest threats. "
" Also in 2011, DeepGuard was updated to use prevalence rate checks in its detection logic [6]. This feature was a logical corollary of the fact that legitimate software are usually found installed by a large percentage of our customer base - that is, they are highly prevalent. These files also change relatively infrequently, making them easy to whitelist and track in a ‘clean file’ database. In contrast, files that have low prevalence quite often turn out to be malware. According to statistics generated from F-Secure’s internal systems monitoring known threats, in a random sample of malicious programs found in the first four months of 2013, 99.7% of the threats were rarely seen in our user base. DeepGuard’s prevalence rate check helps filter out known clean files from suspicious unknown ones, improving both performance and accuracy. DeepGuard’s updateable detection logic is especially useful in countering attacks that exploit vulnerabilities in installed programs in order to run malware on a machine. In such cases, the dropped malware itself can be spotted and blocked by file scanning engines. To halt the attack at an even earlier stage however - that is, at the point of exploitation - F-Secure Labs analysts examine the exploit mechanism for tell-tale actions or behavior patterns, and then incorporate the research results into DeepGuard’s scanning engine. It is then able to pinpoint and block suspicious actions that bear the hallmarks of a vulnerability exploit attempt, preventing malware from being dropped on the machine at all. "
How DeepGuard Works
" DeepGuard’s behavioral analysis is activated by two events. When a program is launched for the first time, DeepGuard analyses it to determine if it is safe to run. Subsequently, DeepGuard continues to monitor the program while running. 1. Pre-launch analysis When a program is first executed, regardless of how it is launched (the user clicks the file icon, an e-mail attachment or program initiates it, etc.), DeepGuard temporarily delays it from executing in order to perform the following checks: 1.1 File reputation check If an Internet connection is available, DeepGuard sends a query to the Security Cloud (below) to check for the latest information on the program’s reputation in the clean file database, which contains the latest security evaluations for a vast catalog of commonly used applications. This database is maintained and constantly updated by F-Secure Labs analysts. Programs that have been rated as clean in the database are allowed to bypass additional checks and launch immediately, whereas known malicious files are blocked at once. For the user, the clean file cloud lookup functionality offers a number of advantages. Being able to use the security verdict for a known file from the clean file database not only removes the burden of identifying unknown or unfamiliar programs as legitimate or malicious from the user, it also means unnecessary security checks on clean files can be avoided. At the same time, by reducing to a manageable level the volume of software that needs to be individually evaluated, the ability to still white- or black-list selected programs becomes more meaningful. "
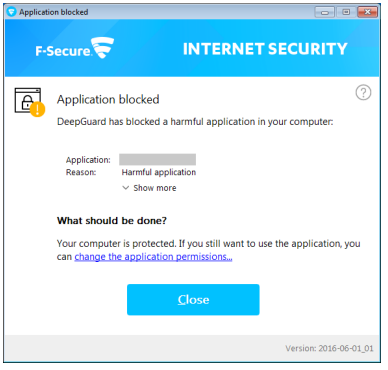
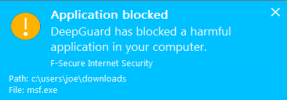
" DeepGuard includes a module that focuses on a file’s prevalence rate. Clean files typically have thousands or millions of users, making them highly prevalent. In contrast, malware samples are comparatively rare. Rare or new files are automatically considered more suspect and subjected to greater scrutiny during the subsequent process monitoring stage. Judgement on execution Based on the file’s reputation and behavior during emulation, DeepGuard makes one of four possible judgements: A. The file is malicious and blocked B. The user is given the option to allow or deny the launch C. The file is clean and allowed to execute D. The file’s status as clean or malicious is still unknown If the file is blocked from launching, a notification message is displayed (right) providing additional details and an option to whitelist the program, if so desired. If the status of the file is still unknown, DeepGuard allows the file to execute but continues to monitor it during the subsequent process monitoring stage.
Even after a program has successfully passed pre-launch analysis and is executed, DeepGuard continues to monitor its behavior as a precaution against delayed malicious routines, a common tactic used by malware to circumvent runtime checks. This form of quiet vigilance also allows DeepGuard to provide constant protection for the user without visibly intruding on their experience by displaying excessive prompts. "
" By evaluating the metadata sent, together with information drawn from the in-house databases and various other sources, the Security Cloud’s automated analysis systems (which make up to 8 million decisions per day) can provide a fully-informed, up-to-date risk assessment for the object during DeepGuard’s pre-launch security evaluation stage, immediately blocking a threat that has been previously seen by any other machine connected to the Security Cloud. This also removes the need to perform further analysis of the object on the client, reducing impact on the user’s experience. The Security Cloud also allows F-Secure Labs analysts to provide critical human intelligence and judgment to complement the automated systems and on-host scanning technology. In addition to creating and maintaining the rules that underpin the databases and automated analysis systems, analysts actively monitor the threat landscape and research malware characteristics and behavior patterns to find the most effective ways to identify truly malicious programs. Once a threat has been confirmed (or a known file’s reputation is modified), the updated details take 60 seconds to replicate across all products connected to the Security Cloud, ensuring up-to-date protection. "
" 2.1 Process monitoring Applications are monitored for a number of suspicious actions, including (but not limited to): y Modifying the Windows registry y Editing files in certain critical system directories y Injecting code in another process’s space y Attempting to hide processes or replicate themselves As legitimate programs will also perform such actions from time to time, DeepGuard does not red-flag a program on the basis of a single action but instead watches for multiple suspicious operations. Once a critical threshold of suspect actions is reached, DeepGuard will block the process from continuing. If available, file reputation and prevalence rating information from the Security Cloud is taken into account to determine this critical threshold. For example, DeepGuard treats files with a low-prevalence rating more aggressively by lowering the critical threshold of suspicious actions that can be performed before the file is blocked "
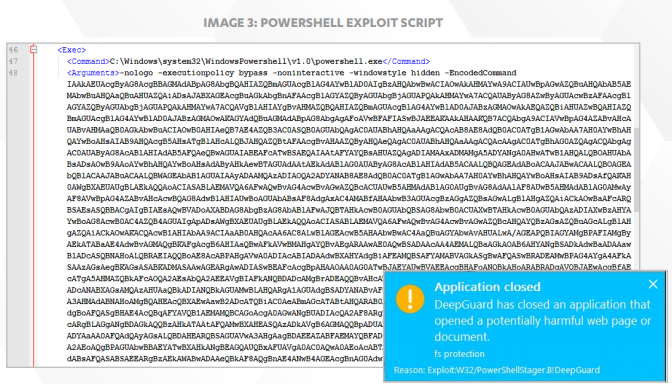
" Starting in 2013, DeepGuard also employs two exploit interception methods that extend the dynamic protection of on-host behavioral analysis by focusing specifically on monitoring the processes of programs that are commonly targeted for exploitation and on document file types commonly used to deliver exploits. 1. Monitoring exploit-prone programs The first method focuses on frequently exploited programs such as Adobe Flash Player, Microsoft Office, web browsers and so on. These programs are kept under especially close watch and are blocked more aggressively if malicious behavior is detected. Of course, which programs become favored targets is unlikely to stay fixed. For example, it was only in the last couple years that Adobe’s Flash Player superseded Oracle’s Java Runtime Environment (JRE) as the most targeted software; in the future, another program may assume that unenviable distinction. The specific programs chosen by DeepGuard for closer attention can be updated by F-Secure Labs analysts when necessary, a responsive approach that allows DeepGuard to adapt to changes in the threat landscape.
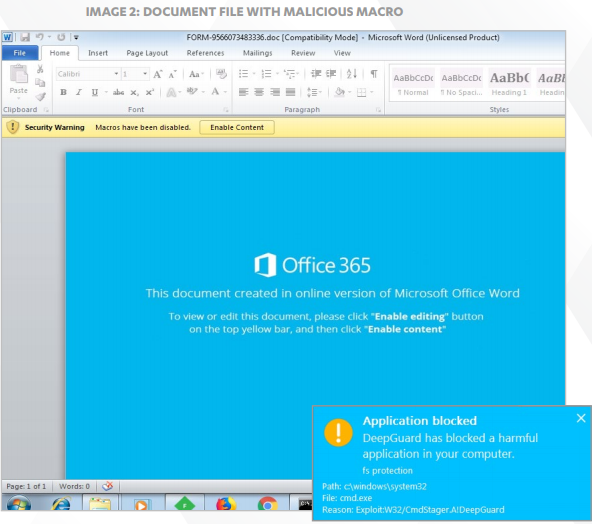
2. Monitoring for document exploits Some document types, such as Microsoft Word or Adobe PDF, are commonly used to deliver exploits. Thus, any software used to open these types of documents is also subject to greater attention by the second exploit interception method, which scrutinizes these programs closely for suspicious behavior caused by malicious document files. This exploit interception module addresses the most common form of targeted attack, which involves sending carefully crafted, exploit-loaded documents to the intended victim or organization. This was the type of attack carried out by the threat actors behind such campaigns as the 2013 ‘Red October’ campaign [7] and the 2014 attacks against Ukrainian targets reported in our ‘BlackEnergy & Quedagh’ whitepaper [8]. This type of attack is particularly effective if the exploits used target a zero-day vulnerability. In a more recent example, in 2015 the cyber espionage group known variously as Sofacy, Pawn Storm or APT28 used exploits targeting zero-day flaws in Microsoft Office (CVE-2015- 2424) and Java (CVE-2015-2590) in order to install a dropper on the affected machine [9]. In all these cases, booby-trapped document files were used to exploit either known or new vulnerabilities in installed programs. By focusing on detecting malicious actions originating from document files however, Deepguard’s exploit interception module is able to provide significant breadth of coverage against document-based exploits, regardless of the file’s physical features or the specific vulnerability being targeted. "
" using DeepGuard in tandem with the other components in a multi-layered security strategy, F-Secure products can share critical details so that all clients are protected against even the latest threats."
Last edited: